Virtual Environment Security
With data migrating to the cloud, organisations are increasingly reliant on virtual server support, to make it easy for applications to be more portable on-premises or in the cloud. Sensitive data needs to be protected wherever it resides on physical and virtual infrastructures, from advanced cyberattacks launched by sophisticated cyber criminals. In this kind of evolving IT environment, organisations need ensure that sensitive data is protected and compliant with the most stringent requirements mandated by local and global data privacy regulations.
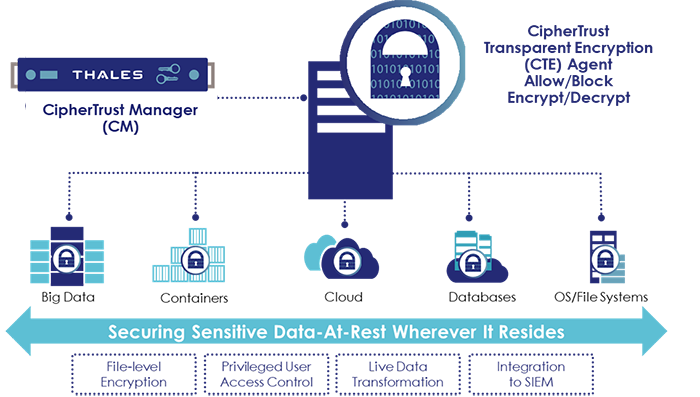
CipherTrust Transparent Encryption is one of the widely deployed data protection solutions within the CipherTrust Data Security Platform, which provides data at rest encryption, fine-grained access control and data access logging. It transparently encrypts data in files, volumes and linked cloud storage on physical, virtual and cloud environments. Deployment is simple, scalable and fast with centralised key management and transparent encryption that does not require any changes to applications.
- Challenges
- Solutions
- Benefits
- Data Exposure in Virtual Environments: As organisations move application workloads to virtual environments and the cloud, sensitive data is exposed to breaches and companies are subject to compliance violations. -
- Administration Complexity across Multiple Data Silos: Administrators are faced with a complex and costly task of managing disparate encryption keys for many different data stores accumulated over time from separate vendors. They have to factor in the cost of administrative resources required to manage multiple incompatible encryption solutions across multiple databases.
- Operational Inefficiencies of Key Management: Managing encryption keys for each data repository and manual systems to store and transmit encryption keys, lack of password control and centralised ways to revoke keys when employees leave creates operational inefficiencies and result in data breaches.
CipherTrust Data Security Platform enables organisations to protect their business critical data by transparently encrypting data-at-rest in files, volumes and databases on Windows, Unix and Linux OSs across physical and virtual servers and centrally manage encryption keys and policies.
- Transparent Encryption with Fine-grained Access Controls
- CipherTrust Transparent Encryption delivers data at rest encryption, privileged user access controls and detailed data access audit logging. It transparently protects data in files, volumes and databases on Windows, AIX and Linux OSs across physical and virtual servers, in cloud and big data environments, without any changes to the applications.
- Centralised Security Policy and Key Management
- CipherTrust Manager provides centralised control for the CipherTrust Data Security Platform and simplifies management of encryption key lifecycle management, including secure key generation, backup/restore, clustering, deactivation and deletion. CipherTrust Manager is available in physical and virtual form factors that can use FIPS 140-2 complaint Thales Luna or third party HSMs.
- Broadest Operating System and Environment Support
- Secure structured databases and unstructured files across data centres, cloud, containers, big data and virtual environments on Linux, Windows and UNIX with a single infrastructure and management environment. Encryption, access control and data access audit logging are available without changes to infrastructure, applications or workflow for maximum control with minimal costs and resource requirements.
• Transparent data protection: CipherTrust Transparent Encryption continuously enforces file-level encryption that protects against unauthorised access by users and processes and creates detailed data access audit logs of all activities without requiring changes to applications, infrastructure, systems management tasks or business practices.
• Seamless and easy to deploy: CipherTrust Transparent Encryption agents and CipherTrust Manager are deployed on physical and virtual servers.
• Comprehensive security intelligence: CipherTrust Transparent Encryption provides detailed data access audit logs that not only satisfy compliance requirements, but also enable data security analytics using security information and event management (SIEM) systems.



