Selecting the Right Encryption Approach for your Organisation
In the board-room, data encryption may be viewed as binary: if data encryption is employed, the company’s assets are secure; and if it’s not, the company’s data assets are not secure and it’s time to panic.
However, for the security teams whose job it is to secure sensitive data, the reality is not so simple. At a high level, data encryption types can be broken out into the four levels in the technology stack at which data encryption typically is employed:
- 1. Full-disk or media
- 2. File system
- 3. Database
- 4. Application
In general, the lower in the stack encryption is employed, the simpler and less intrusive the implementation will be. However, the number and types of threats these data encryption approaches can address are also reduced. By employing encryption higher in the stack, organisations can typically realise higher levels of security and mitigate more threats.
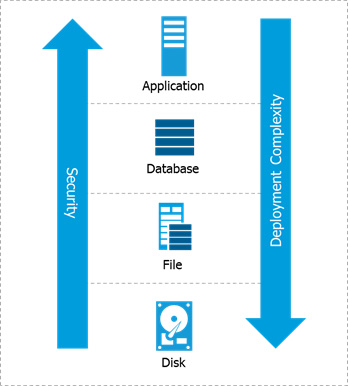
- Full-Disk Encryption
- File-Level Encryption
- Database eEcryption
- Application-Layer Encryption
Full-Disk Encryption (FDE) and Self-Encrypting Drives (SED) encrypt data as it is written to the disk and decrypt data as it is read off the disk.
FDE/SED Advantages:
- Simplest method of deploying encryption
- Transparent to applications, databases and users.
- High-performance, hardware-based encryption
FDE/SED Limitations:
- Addresses a very limited set of threats – protects only from physical loss of storage media.
- Lacks safeguards against Advanced Persistent Threats (APTs), malicious insiders or external attackers
- Meets minimal compliance requirements
- Doesn’t offer granular access audit logs
Key takeaways:
- Mainstream cloud providers offer the functional equivalent of FDE with its attendant limitations listed above.
- FDE makes sense for laptops, which are highly susceptible to loss or theft. But FDE isn’t suitable for the most common risks faced in data centre and cloud environments.
Learn More:
- Analyst Resources:
- Relevant Thales solutions:
- CipherTrust Enterprise Key Management securely manages encryption keys for on-premises FDE storage.
- Those who use encryption provided by their Cloud Service Provider (CSP) can employ CipherTrust Cloud Key Manager to take control of data encryption keys from CSPs and thereby enhance compliance around encryption key management.
Encrypting data at the file or volume level (typically used for databases) offers security controls with software agents installed in the operating system. Agents intercept disk reads and writes and apply policies to determine if the data should be encrypted or decrypted. Mature file-system encryption products offer strong policy-based access controls, including for privileged users and processes, and granular logging capabilities.
File-Level Encryption Advantages:
• Transparent to users and applications, so organisations don’t have to customise applications or change associated business processes.
• Supports both structured and unstructured data.
• Establishes strong controls that guard against abuse by privileged users and meet common compliance requirements.
• Offers granular file access logs and speeds up threat detection using SIEM systems that can be used for security intelligence and compliance reporting.
File-Level Encryption Limitations:
• Encryption agents are specific to operating systems, so it is important to ensure the solution selected offers coverage of a broad set of Windows, Linux and Unix platforms.
Key takeaways:
• For many organisations and purposes, file encryption represents the optimal approach. Its broad protections support the vast majority of use cases and it is easy to deploy and operate.
Relevant Thales solutions and capabilities:
• CipherTrust Transparent Encryption offers encryption of structured and unstructured files along with strong privileged user access controls.
• CipherTrust Security Intelligence offers robust capabilities for leveraging granular security logs.
This approach enables security teams to encrypt a specific subset of data within the database or the entire database file. This category includes solutions known as Transparent Data Encryption (TDE) from multiple database vendors. This category also includes column level encryption. This is a type of database encryption method that allows users to select specific information or attributes to be encrypted instead of encrypting the entire database file.
Advantages:
- Safeguards data in databases, which are critical repositories.
- Establishes strong safeguards against a range of threats, including malicious insiders – even in some cases a malicious database administrator.
- Provides transparent encryption of sensitive database content on a per-column basis.
Limitations:
- With TDE, offerings from one database vendor can’t be applied to databases from other vendors.
- TDE doesn’t enable central administration across multiple vendor databases or other areas in environment.
- Only encrypts columns or tables of a database, leaving configuration files, system logs and reports exposed.
The takeaway:
- While TDE technologies can meet specific, tactical requirements, they don’t enable organisations to address security across heterogeneous environments. As a result, they can leave organisations with significant security gaps.
Learn More:
- Relevant Thales solutions:
- CipherTrust Database Protection can be used to integrate data encryption for sensitive columns in databases.
- CipherTrust Enterprise Key Management can be used to manage TDE cryptographic keys.
When employing this approach, application logic is added to govern the encryption or tokenisation of data from within the application.
Advantages:
- Secures specific subsets of data, such as fields in a database.
- Encryption and decryption occur at the application layer, which means data can be encrypted before it is transmitted and stored.
- Offers highest level of security, providing protections against malicious DBAs and SQL-injection attacks.
- Tokenisation can also significantly reduce PCI DSS compliance costs and administrative overheads.
Limitations:
- These approaches need to be integrated with the application and therefore require development effort and resources.
The takeaway:
- These approaches may be optimal in cases in which security policies or compliance mandates require specific sets of data to be secured. In addition, variants of application-layer encryption, including tokenisation and format-preserving encryption, can help reduce the impact on databases.
- Look for solutions with well-documented, standards-based APIs and sample code to simplify application development.
Learn More:
- Relevant Thales solutions:
- CipherTrust Application Data Protection simplifies the process of adding encryption to existing applications.
- CipherTrust Tokenisation simplifies the process of adding tokenisation and dynamic data masking into existing applications.



