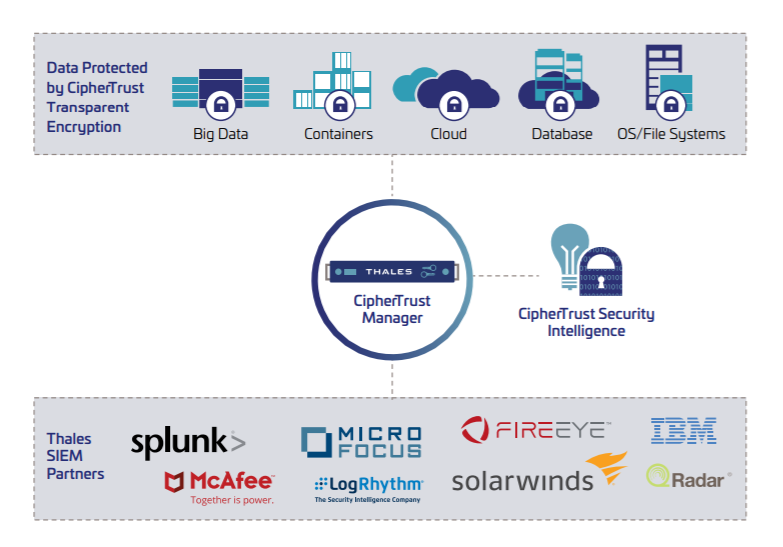
Security Intelligence
CipherTrust Transparent Encryption delivers detailed data access audit logs, which are useful for compliance, identifying unauthorized access attempts, and building baselines of authorized user access patterns. CipherTrust Security Intelligence (formerly known as Vormetric Security Intelligence) logs and reports streamline compliance reporting and speedup threat detection using leading Security Information and Event Management (SIEM) systems. The solution allows immediate automated escalation and response to unauthorized access attempts and provides all the data needed to build behavioral patterns required to identify suspicious usage by authorized users.
- Benefits
- Features
Speed Response
Leverage immediate alerts that fuel the fastest, most efficient response when issues arise.
Boost Visibility
Produces an auditable trail of permitted and denied access attempts from users and processes.
Strengthens Data Security
Uncover anomalous process and user access patterns that could point to an APT attack or malicious insider activities.
Pre-built SIEM Integrations
Collected at the system level, CipherTrust Transparent Encryption logs report authorized and unauthorized access attempts to encrypted files and volumes--including user, time, process, and more. CipherTrust Security Intelligence logs and reports streamline compliance reporting and speedup threat detection using leading Security Information and Event Management (SIEM) systems. Authorized user access data is available to create baselines for user's data usage, and can be integrated with other security data, such as user location and access points for pinpoint threat identification.
Granular, Actionable Security Intelligence
CipherTrust Security Intelligence logs produce an auditable trail of permitted and denied access attempts from users and processes. The solution’s detailed logs can be reviewed to specify when users and processes accessed data, under which policies, and if access requests were allowed or denied.
Streamlined Compliance and Auditing Reporting
To adhere to many compliance mandates and regulations, organizations must prove that data security is in place and meets required standards. CipherTrust Security Intelligence integration to SIEM systems can be used to easily demonstrate to an auditor that encryption, key management, and access policies are effective and appropriate. With its detailed visibility and integration capabilities, CipherTrust Security Intelligence helps streamline the effort associated with audits and ongoing compliance reporting.


