The Need for VPN Two-Factor Authentication and Access Management
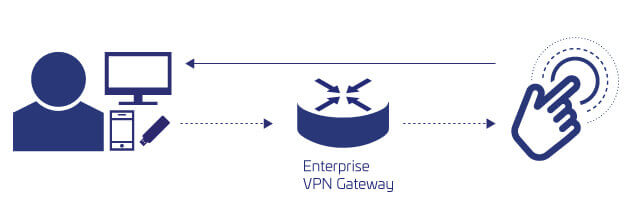
In a decentralized IT environment, the organizational Virtual Private Network (VPN) is just one of several ways to access confidential network resources and critical business applications. Organizations are deploying core business applications and sensitive resources across a greater number of web-based, cloud-based and on premises servers.
At the same time, as employees are increasingly mobile and expect ‘anywhere’ access, organizations are looking to ensure network security with strong VPN authentication. Administrators are looking to enforce consistent authentication policies and user access controls on all corporate resources, while keeping their authentication solution flexible, cost-effective, and easy to-deploy.
Complying with Strong Authentication Mandates
Strong authentication is imperative for a sound, layered security strategy that mitigates against data breaches and enables regulatory compliance.
Learn more about how Thales' strong authentication solutions which enable you to comply with corporate and industry mandates:
Start a STA Free Trial



