Key Management
Thales Key Management solutions simplify and strengthen the management of keys across cloud and on-premises environments. They support a wide range of use cases and run on FIPS 140-2 Level 1–compliant virtual or hardware appliances, providing strong protection for sensitive data. These tools centralize key management so you can manage keys from CipherTrust Data Security Platform as well as third-party applications from a single location.
By consolidating data control, Thales gives you better visibility and governance over your keys while improving overall data security. Thales Key Management products integrate smoothly with your applications through standard interfaces, delivering reliable, scalable, and robust key-management capabilities.
Key Management Challenges and Trends
57 %
Enterprises use five or more key managers*1
48 %
Keys managed in cloud provider consoles*2
28 %
BYOK is the most common key control approach*2
Key Management Benefits
Centralized control and visibility
Manage all encryption keys from a single, unified platform—across on-premises, cloud, and hybrid environments—for streamlined operations and reduced complexity.
Enhanced Security and Compliance
Enforce consistent security policies and meet regulatory requirements with FIPS 140-2–compliant appliances and centralized key lifecycle management.
Seamless Multi-Cloud Integration
Gain full control of cloud-native keys and services across multiple providers, ensuring secure, compliant operations in hybrid and multi-cloud deployments.
We built our encryption key management software to support AWS, Azure, Google Cloud, and other major cloud providers already in your ecosystem.

Interoperability and Flexibility
Leverage KMIP and standard interfaces for seamless integration with third-party applications, databases, and security tools—reducing vendor lock-in.
Developer Empowerment and Operational Efficiency
Simplify key management for developers with application-level integration and automated workflows, minimizing manual key handling and improving security at scale.


Gartner® and Peer Insights™ are trademarks of Gartner, Inc. and/or its affiliates. All rights reserved. Gartner Peer Insights content consists of the opinions of individual end users based on their own experiences, and should not be construed as statements of fact, nor do they represent the views of Gartner or its affiliates. Gartner does not endorse any vendor, product or service depicted in this content nor makes any warranties, expressed or implied, with respect to this content, about its accuracy or completeness, including any warranties of merchantability or fitness for a particular purpose.


Enhance your security
See how we can help you discover, protect and control your data
Unify and Simplify Key Management Across All Your Environments
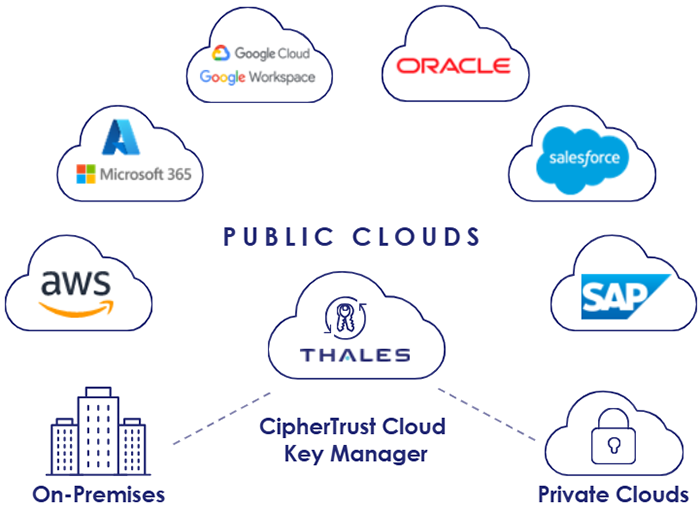
Products: CipherTrust Manager (CM), CipherTrust Cloud Key Management (CCKM)
Use Case: Centrally manage and control encryption keys across AWS, Azure, Google Cloud, and other cloud providers to maintain visibility, enforce policies, and ensure compliance in hybrid and multi-cloud environments.
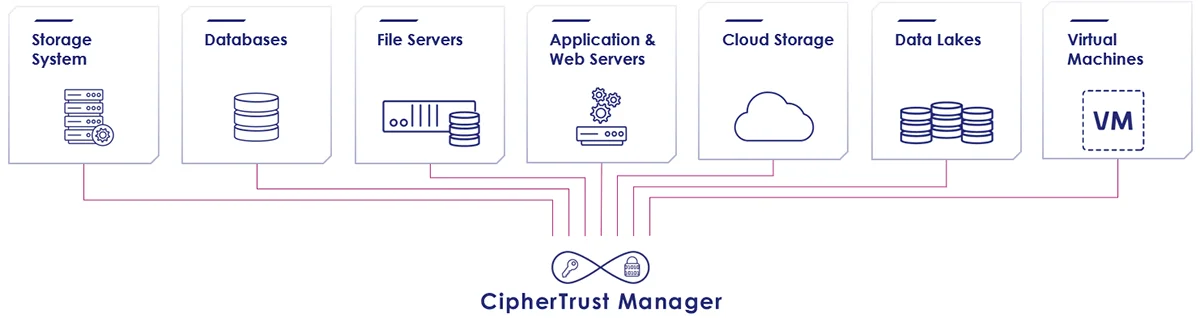
Products: CipherTrust Manager (CM), CipherTrust Enterprise Key Management (EKM)
Use Case: Secure databases, file systems, and storage arrays within enterprise data centers. Ensure data sovereignty and compliance with standards such as GDPR, HIPAA, and PCI DSS through centralized key lifecycle management.
Products: CipherTrust Application Key Management (CAKM)
Use Case: Enable developers to encrypt sensitive data at the application layer without managing keys directly. Improve security for cloud-native and SaaS applications by isolating keys from application data.
Products: Key Management Interoperability Protocol (KMIP), CipherTrust Manager (CM), CipherTrust Enterprise Key Management (EKM)
Use Case: Integrate with third-party encryption tools, databases, and storage systems using KMIP standards. Simplify operations and reduce vendor lock-in across diverse IT environments.
Products: CipherTrust Manager (CM), CipherTrust Enterprise Key Management (EKM), CipherTrust Cloud Key Management (CCKM)
Use Case: Ensure encryption keys are securely backed up, synchronized, and recoverable across distributed environments. Maintain access to encrypted data during outages or cloud service disruptions.
Products: CCKMaaS and CAKMaaS
Use Case: CCKMaaS and CAKMaaS on the DPoD Matrketplace provide centralized, cloud-delivered lifecycle management for both cloud-native and application-level encryption keys across multi-cloud and hybrid environments. Together, they automate key discovery, rotation, application-level key services, and policy enforcement—giving organizations unified control over disparate cloud KMS platforms and the cryptographic keys used directly by their applications. This combined approach streamlines compliance, strengthens data protection, and ensures consistent, enterprise-wide cryptographic governance from the cloud layer down to the application layer.
Click-and-Deploy Data Security
Conveniently deploy best-in-class key management services from the cloud, or on-premises – making security simpler, more cost-effective, and easier to manage.
Thales key management includes the following products
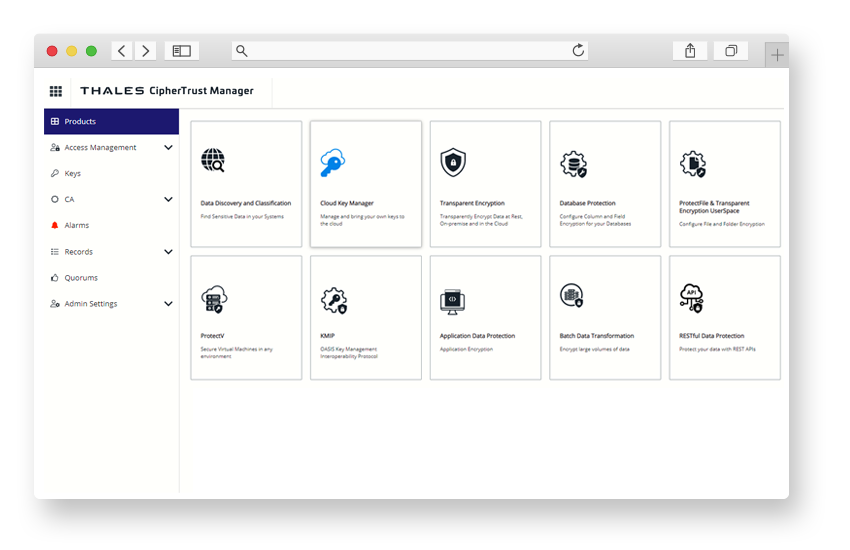
CipherTrust Manager
Centralized management platform that unifies encryption key lifecycle control, policy enforcement, and access management across cloud, on-premises, and hybrid environments.
Key Management Interoperability Protocol
An open standard that defines communication between encryption key management systems and clients, enabling interoperability across diverse security products and vendors.
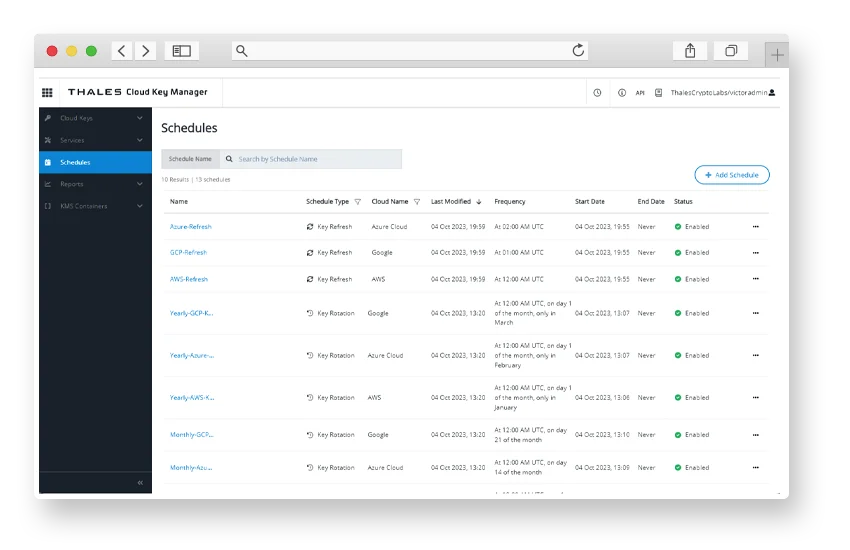
CipherTrust Cloud Key Management
Enables centralized management of cloud provider encryption keys, giving organizations visibility, control, and compliance across multi-cloud environments and services.
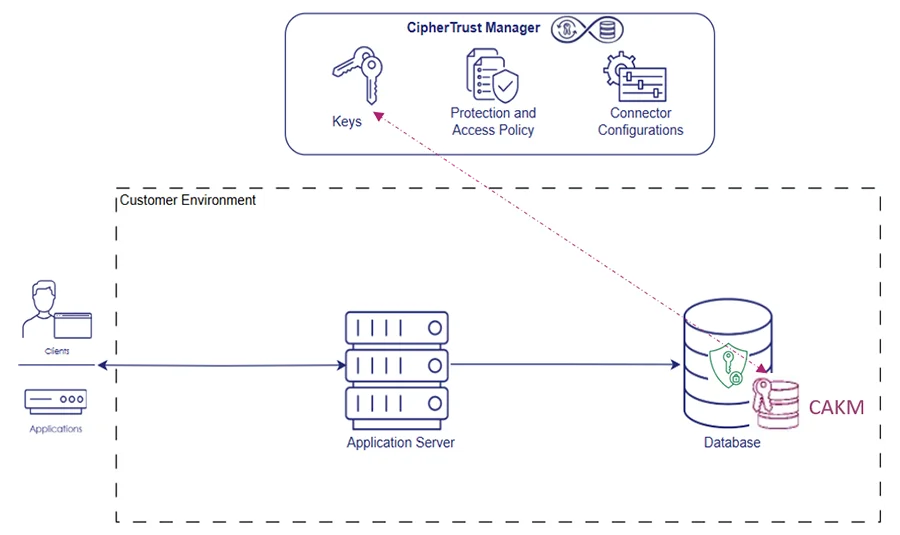
CipherTrust Application Key Management
Offers application-level key management and encryption in the cloud, allowing developers to secure data without handling or storing encryption keys directly.
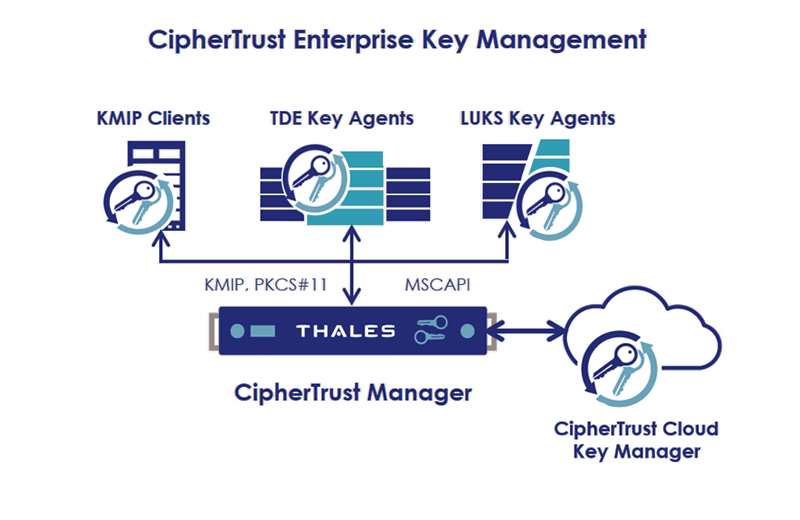
CipherTrust Enterprise Key Management
Provides secure, centralized lifecycle management of encryption keys for on-premises systems, databases, and storage, ensuring consistent security and compliance.
Data Security Platform Demos
Thales’ interactive demos showcase how its unified CipherTrust Data Security Platform delivers both protection and visibility across hybrid and multi-cloud environments.