Protecting Data in Databases
Protecting data in databases at the OS, Database and Application layers.
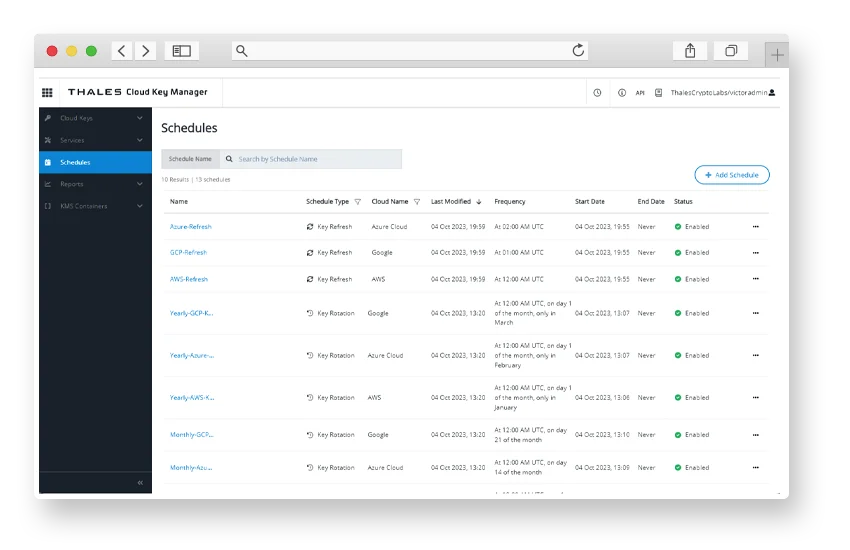
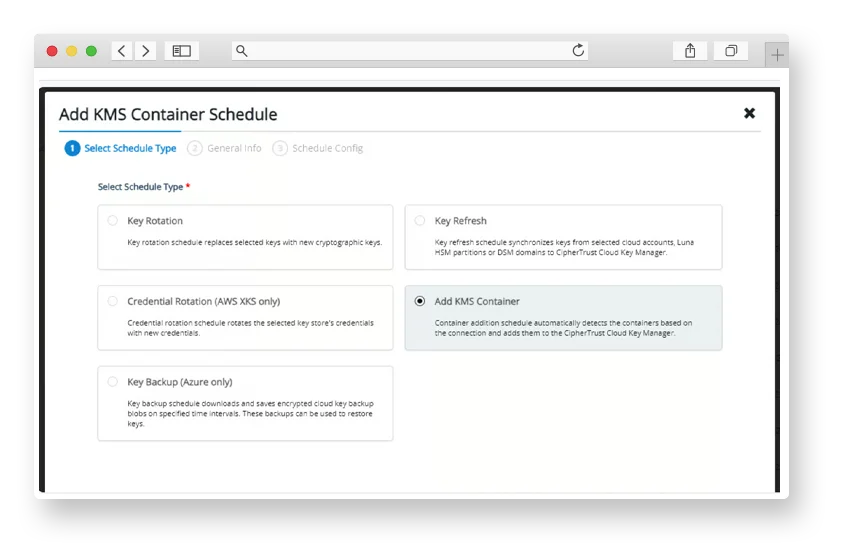
Cloud Key Management
Simplify key lifecycle management across clouds enabling centralized control and compliance-ready operations.
Auto Key Service Detection
Automatically discover and integrate with cloud-native key services, reducing configuration overhead and improving visibility.
Hold Your Own Key
Empower customers to retain full control of encryption keys—even in cloud provider environments—enhancing data sovereignty.
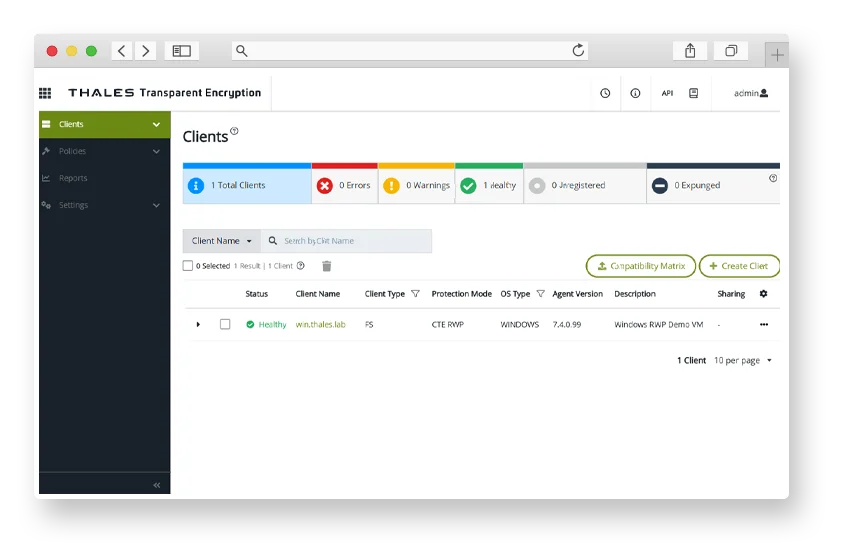
Transparent Encryption
Ensure data-at-rest protection across on-premises and cloud environments without application changes.
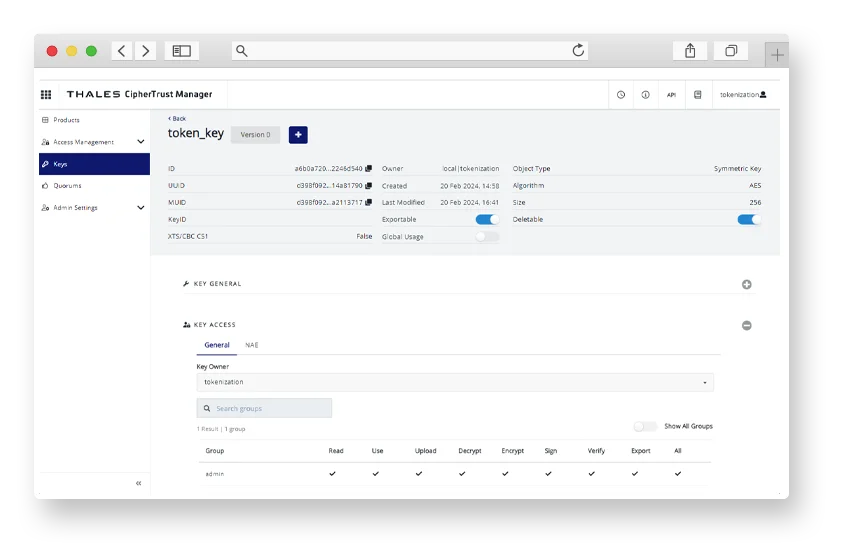
Tokenization
Protect sensitive data while keeping it usable for businesses and minimizing compliance scope.
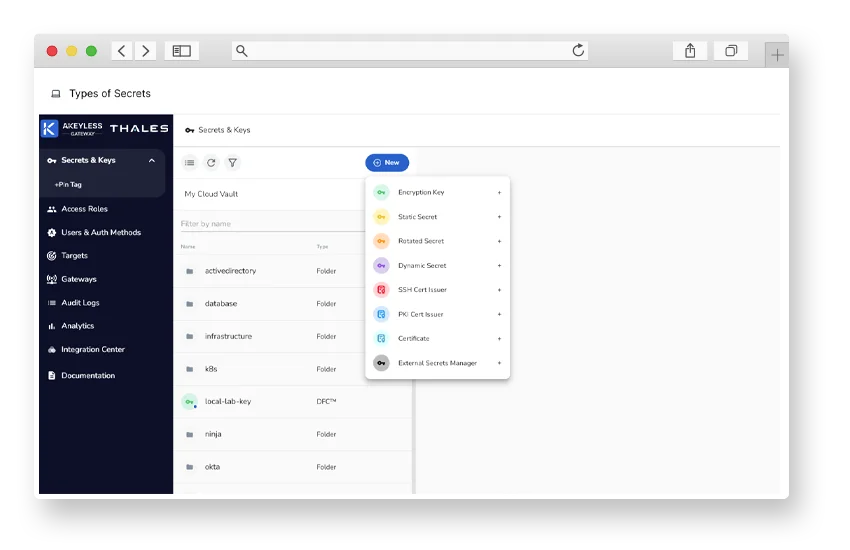
Secrets Management
Secure API keys, credentials, and other secrets through centralized lifecycle management and access controls.
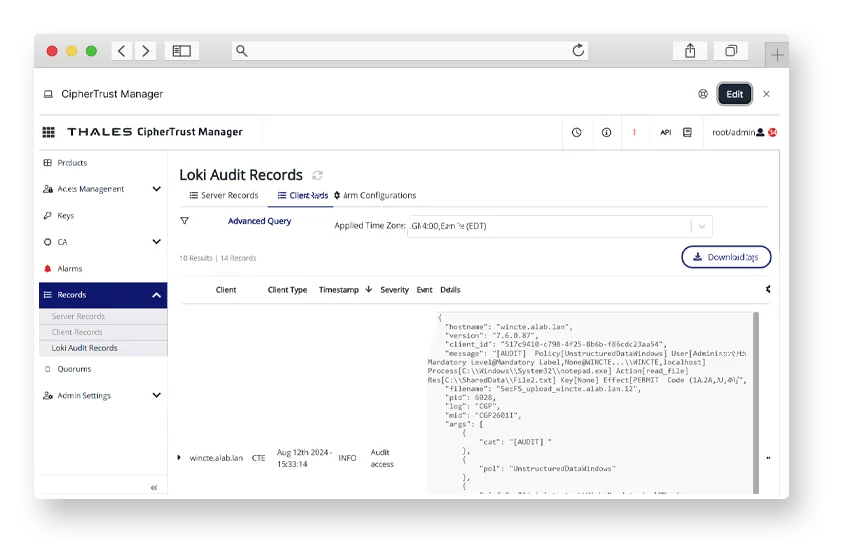
Ransomware Protection
Learn how policy enforcement and encryption capabilities can minimize ransomware impact by blocking unauthorized data access and modification.
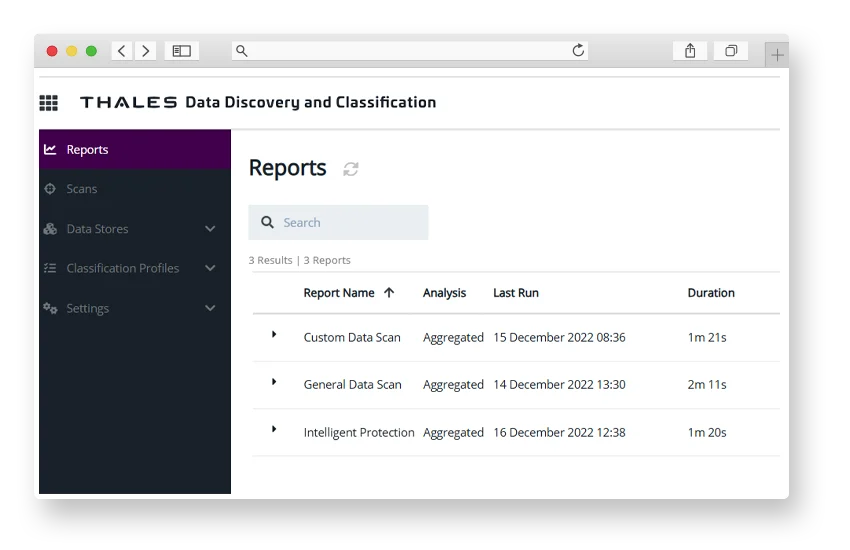
Data Discovery and Classification
Shift data security from reactive to strategic by providing clear visibility into the various types of data that exist anywhere within your organization.
Transparent Encryption as a Service
Take a tour of CipherTrust Transparent Encryption as a service, part of CDSPaaS on the Data Protection on Demand Marketplace.
Cloud Key Management
Simplify key lifecycle management across clouds enabling centralized control and compliance-ready operations.
Auto Key Service Detection
Automatically discover and integrate with cloud-native key services, reducing configuration overhead and improving visibility.
Hold Your Own Key (HYOK)
Empower customers to retain full control of encryption keys—even in cloud provider environments—enhancing data sovereignty and compliance.
Transparent Encryption
Ensure data-at-rest protection across on-premises and cloud environments without application changes.
Tokenization
Learn how format-preserving tokenization protects sensitive data while keeping it usable for business processes and minimizing compliance scope.
Secrets Management
Secure API keys, credentials, and other secrets through centralized lifecycle management and access controls.
Ransomware Protection
Learn how policy enforcement and encryption capabilities can minimize ransomware impact by blocking unauthorized data access and modification.
Data Discovery and Classification
Enable the overall approach to data security from reactive to strategic. By providing clear visibility into the various types of data that exist anywhere within your organization.
Transparent Encryption as a Service
Take a tour of CipherTrust Transparent Encryption as a service, part of CDSPaaS on the Data Protection on Demand Marketplace.