CipherTrust Application Data Protection Software Development Kit (CADP SDK) protects data in applications/services as a performant SDK and eliminates the need for Developers (Devs) to manage security details and regularly update data protection.
Updates are no longer made in code
Decrease Dev Involvement
- Close vulnerability gaps for sensitive data in realtime
- Keep on top of the latest data security without creating major projects
- Decrease complexity with bulk data protection
Increase Dev Capacity
- Reduce the drag on the Dev team
- Pass responsibility for data protection to the data security team via simplified APIs
- Gain a competitive edge over organizations that use traditional code
Separation of Duties
- Devs call data protection
- Data Security Admins control the what, the how, and the who via centrally managed policies
- Crypto agility enables Data Security Admins to change ciphers, parameters and keys in realtime

GARTNER is a trademark and service mark of Gartner, Inc., and/or its affiliates, and is used herein with permission. All rights reserved.
Apply any type of data protection from a single interface
CADP SDK supports tokenization, encryption and data generalization so that organizations can optimize data protection for each piece of data to decrease the risk of sensitive data being leaked. CADP SDK supports format preservation to fit each organization’s current schema so that organizations don’t have to make changes in their environment.
CADP SDK supports Data Masking and Redaction to reveal sensitive data on a need-to-know basis.
- Static Data Masking masks the data that doesn’t need to be accessed, revealing only the data relevant to the group – this is especially valuable for data analysts (pseudonymization) and increased performance for customer service (data is already masked when it arrives).
- Dynamic Data Masking is preferred when users with different access levels will be accessing the data and have rights to access different parts of the data.
- Redaction provides an absolute mask that shows a field with redacted data or hides the field.
Centralized management
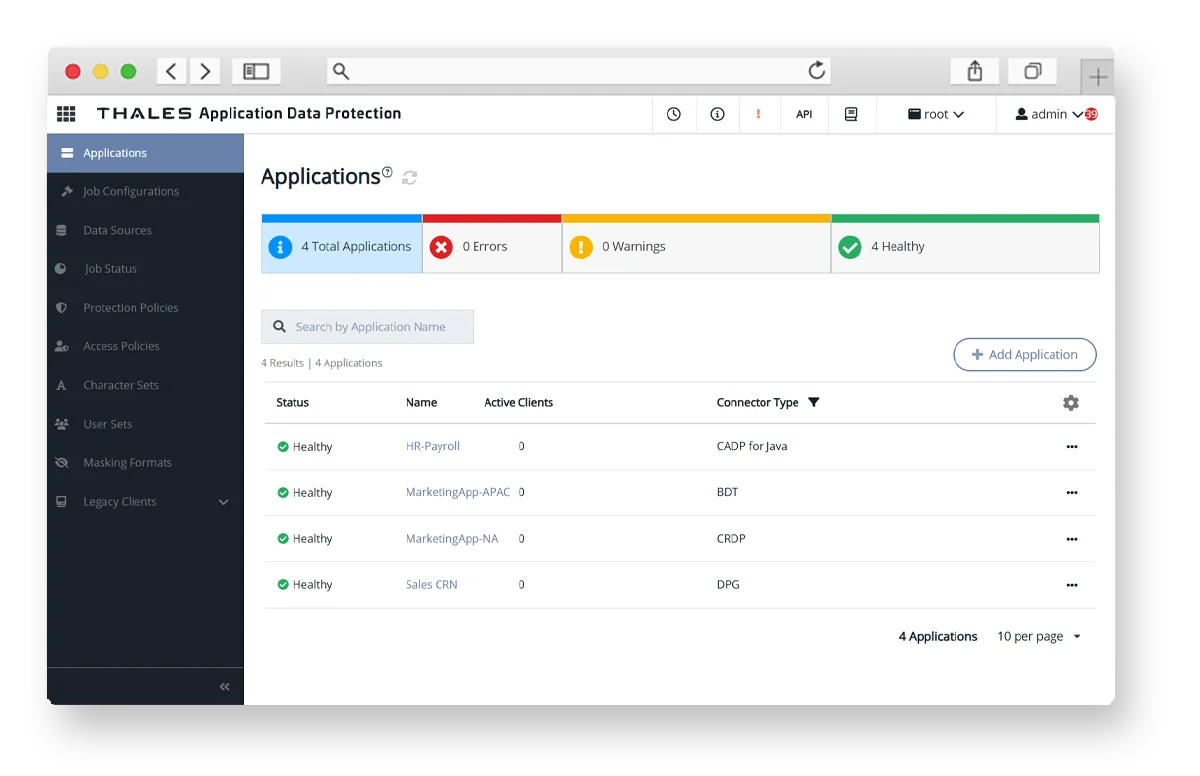
Audits become accurate, significantly faster and complete due to visibility of all policies on a single pane of glass showing where Connectors are deployed and the corresponding version numbers.
CipherTrust Manager provides a centralized view of every crypto agile Connector’s status—whether operational, offline, or requiring attention, alongside metrics such as health and last check-in time. Data Security Administrators can instantly drill down into individual Connectors for detailed information, configuration adjustments or automated remediation.
We have Tokenization and Encryption solutions to meet your security and infrastructure requirements.
Benefits for each role
With CADP SDK you can have:
- More revenue, due to increased Dev capacity
- More security, due to the ability to close vulnerability gaps in realtime
- More innovation, due to not increasing the backlog
Close vulnerability gaps in < minute, Roadmap is respected (because there are no data protection fire drills taking Devs off revenue-generating projects).
Devs can remain focused on revenue-generating projects because they are not involved in updating data protection.
No downtime or fire drills required to update data protection.
Ultra secure (staying on top of your security posture by closing vulnerability gaps in < minute), Roadmap is respected (because there are no data protection fire drills taking Devs off revenue-generating projects).
Visibility into current security posture (single pane of glass, centralized-management, policy-based), No code change to make updates (removes dependency on DevOps for updates).
Reputation is protected, audits are passed, in compliance, does not add to technical debt.
Audits are passed, in compliance, empowered to update data protection whenever needed.
No need to learn crypto or do the data protection updates, does not add to technical debt.