Customer Identity
Empower your customers with seamless, secure and compliant customer experiences
Learn MoreFrom the moment we engage with a platform or service, our identity shapes the experience: how we're recognized, the level of personalization we receive, and the trust we place in the interaction. That’s why Thales is committed to providing you with everything necessary to manage identities successfully.
Thales’ Identity and Access Management solutions ensure the right individuals have access to the right resources at the right times for the right reasons. We’re here to deliver the expertise, capabilities, and support you need to make IAM processes straightforward, frictionless, and more dependable.
Get modern, phishing-resistant authentication without sacrificing control or seamless access—on-prem and in the cloud.

Empower your customers with seamless, secure and compliant customer experiences
Learn More
Modernize partner collaboration. Build trusted experiences with IAM solutions tailored for external relationships
Learn More
Increase productivity and efficiency by ensuring employees have secure and efficient access to applications
Learn MoreThales offers comprehensive Identity and Access Management solutions designed to securely manage and authenticate the identities of individuals accessing digital services. Our people and technologies provide organizations with capabilities needed to improve user experiences, build customer trust, and modernize identity administration.
Improve user convenience with frictionless log in and account creation. Strengthen security and ensure compliance with additional or step-up authentication methods.
Allow users to seamlessly bring their identity from one platform to another.
Protect your customers against unauthorized access with additional layers of security.
Proof and validate the identities of your customers online with KYC requirements.
Improve security and meet regulatory requirements with passkeys and strong authentication measures.
Minimize fraud-related risks with adaptive authentication capabilities.
Empower your customers to eliminate passwords and facilitate easier re-engagement with your brand.
Ensure that only legitimate users gain access to digital banking services.
Orchestrate customer journeys with personalization and compliance at the forefront. Build rich customer profiles in a non-invasive matter. Foster customer trust – and loyalty – by showing them your commitment to protecting their privacy and digital space.
Optimize engagement, personalize interactions, and drive conversions with tailored user journeys.
Foster customer trust and ensure compliance with transparent consent management processes.
Develop rich customer profiles by gradually collecting firsthand data, without overwhelming them.
Streamline access control, enforce consistent authorization policies, and fortify API security to drive seamless digital growth.
Streamline access control and effortlessly assign and manage user roles.
Establish consistent authorization policies and allow access control based on user attributes.
Enforce adaptive access policies at the individual, group or application level, with a broad range of authentication options.
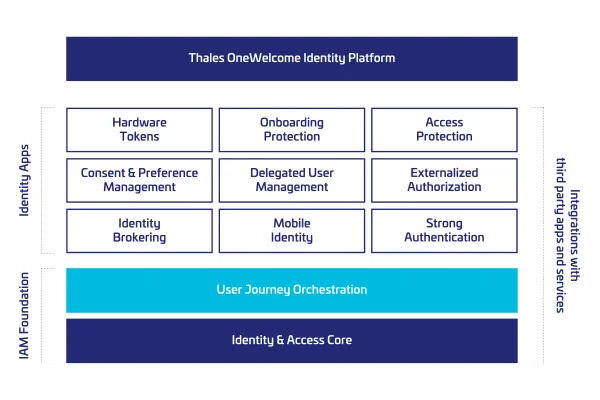
The OneWelcome Identity Platform empowers organizations with a versatile set of identity applications suitable for a wide range of use cases, including customer, partner, and supplier identities. Identity apps can be mixed and matched to help you achieve your IAM objectives quickly and with less complexity.
The platform supports various authentication methods FIDO2 passkeys, hardware tokens, smart cards, and software authenticators, ensuring secure access across different environments and devices.
Thales Authenticators address numerous use cases, assurance levels, and threat vectors, leveraging both current and emerging protocols (OTP, PKI, FIDO) as well as multiple form factors (hardware and virtual smart cards and tokens, software and mobile authenticators).
SafeNet Trusted Access, our cloud-based workforce IAM service, will help you deliver intuitive and secure authentication journeys. Accelerate your cloud transformation, secure hybrid infrastructures, reduce the risk of shadow IT, and make work life easier.
SafeNet Authentication Service Private Cloud Edition (SAS PCE) is an on-premises authentication platform making authentication easy and cost effective to implement and manage. Our approach has been to design a solution which takes away many of the traditional pain points in authentication.
Thales helps banks take advantage of their ongoing digital transformation by ensuring customer trust and regulatory compliance. IdCloud – now part of the OneWelcome Identity Platform – is a suite of cloud-based managed services that enable FIs to combine identity proofing, strong customer authentication (SCA), and risk management to secure onboarding and access to digital banking services.