CipherTrust Database Protection (CDP) quickly protects sensitive column-level data directly inside databases with no need to modify many applications. CDP eliminates the need for Developers to learn cryptography or re-test applications after live key rotation or cipher updates.
Encrypt data without modifying applications
Decrease Dev Involvement
- < 5 minutes to set up protection at the column level
- Maintain consistent high performance across on-prem, hybrid, and multi-cloud databases
- Eliminate the need to modify application code or database logic
Increase Dev Capacity
- Reduce the drag on the Dev team by removing crypto maintenance from the backlog
- Pass responsibility for data protection to the security team via centralized key management
- Gain a competitive edge over solutions which require application modification
Separation of Duties
- Developers and applications call standard SQL queries — encryption is handled transparently by CDP
- Data Security Admins control what is encrypted, how, and who has access through centrally managed policies
- Crypto agility enables Data Security Admins to rotate keys or change ciphers in real time without downtime
The Forrester Wave™: Data Security Platforms, Q1 2025
Cost savings and business benefits enabled by the CipherTrust Data Security Platform

Data is everywhere, and what constitutes sensitive data for organizations today has greatly expanded."
Database encryption management
Decrease ongoing costs with centralized key and policy management in CipherTrust Manager (FIPS 140-2 up to Level 3) with built-in key rotation and data rekeying.
Data Security Administrators can instantly drill down into encryption parameters for individual columns or perform configuration adjustments.
Rapid setup - simply identity the column to be protected and set the data protection parameters to align with your organization's security policy. Determine what unauthorized users (including the DBA/security officer) will see after the column has been encrypted.
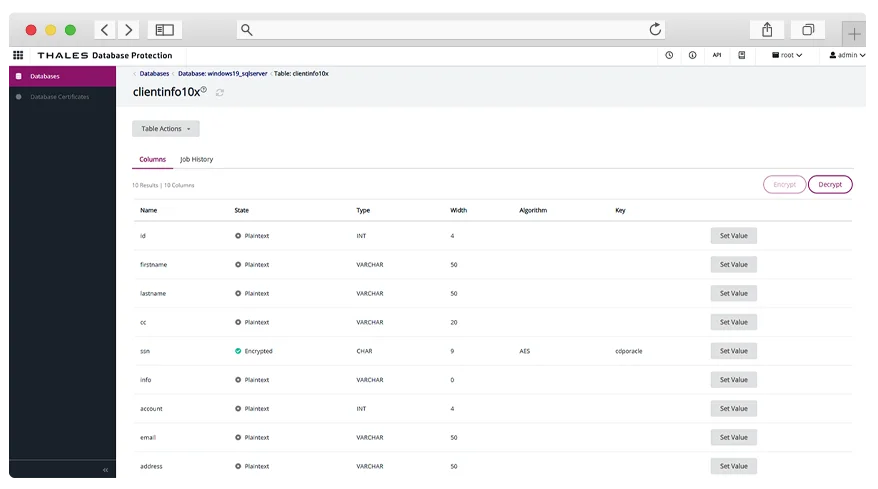
5 minutes to set up protection at the column level
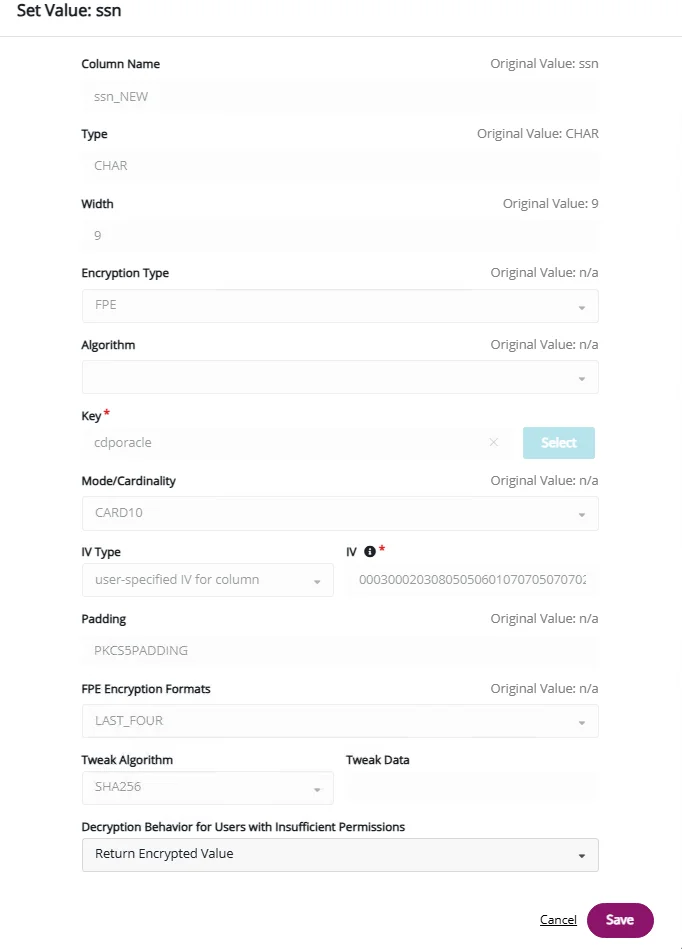
Increase efficiency with centrally-managed protection parameters
Selectively limit access
Without CDP, DBAs and other system administrators can decrypt sensitive data.
CDP protects structured data with AES and Format-Preserving Encryption (FPE) so organizations can secure and decrypt sensitive fields efficiently and perform data analytics on encrypted data.
Organizations can choose local encryption on the database server for maximum performance or remote encryption within CipherTrust Manager to ensure encryption keys never leave the secure enclave.
Data masking made easy
CDP supports data masking with FPE and granular access controls so that sensitive data can be revealed only on a need-to-know basis:
- Static Data Masking masks data that doesn’t need to be accessed, revealing only the data relevant to each group—ideal for analysts and customer support use cases
- Dynamic Data Masking (via replacement values for unauthorized users) applies different visibility rules based on user roles and privileges
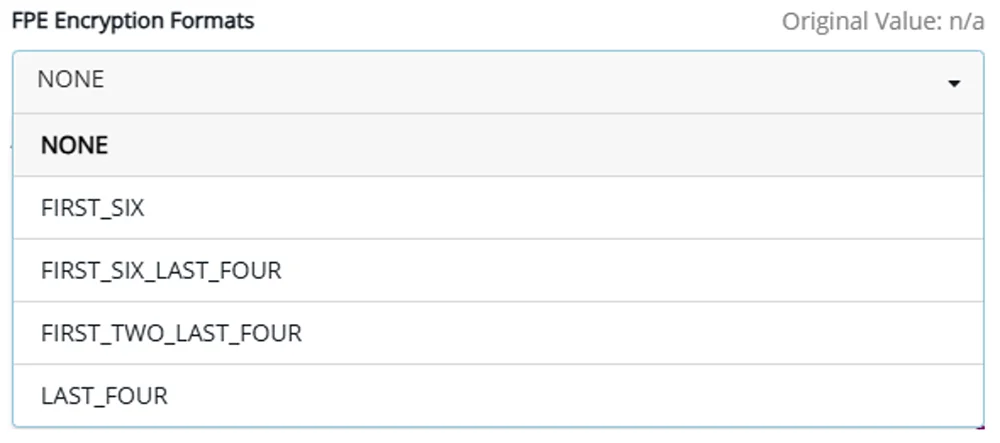
Maintain Operations transparency post-encryption (5 Data Masking options)
Benefits for each role
With CDP, you can have:
- More revenue, due to increased Dev capacity
- More security, with column-level encryption and live key rotation
- More innovation, without adding to the backlog
Close vulnerability gaps in < minute, Roadmap is respected (because there are no data protection fire drills taking Devs off revenue-generating projects).
Devs can remain focused on revenue-generating projects because they are not involved in updating data protection.
No downtime or fire drills required to update data protection.
Ultra secure (staying on top of your security posture by closing vulnerability gaps in < minute), Roadmap is respected (because there are no data protection fire drills taking Devs off revenue-generating projects).
Visibility into current security posture (single pane of glass, centrally-managed), No code change to make updates (removes dependency on DevOps for updates).
Reputation is protected, audits are passed, in compliance, does not add to technical debt.
Audits are passed, in compliance, empowered to update data protection whenever needed.
No need to learn crypto or do the data protection updates, does not add to technical debt.