Establishing Integrity, Confidentiality, and Availability across 5G networks
5G connectivity is ready to transform industries and the way telcos operate, and 5G users will benefit from more connections with fewer drops and less interference, while enjoying remote access from almost anywhere. Though 5G creates extraordinary opportunities for people and businesses, this groundbreaking technology relies on virtualized, cloud-based, and multi-vendor architecture, which introduces unique technical and security challenges.
According to the 2023 Thales Data Threat Report Telecommunications Edition, telco companies, global enterprises and governments share the same areas of concern when it comes to addressing 5G cybersecurity:
- Data in Motion: Securing data moving across 5G networks.
- Identities: Protecting the identities of people and devices connecting to 5G networks.
- Applications and Infrastructure: Securing applications, infrastructure, and sensitive data on 5G networks.
Thales provides 5G security solutions that help address these complex challenges and mitigate the threat to data integrity, availability, and confidentiality across 5G networks.
5G security is a significant concern in telecom and in the broad market.
81%
of telecom respondents are concerned about 5G security threats.
Achieving Quantum Readiness in 5G Networks
Quantum computers could undermine the integrity of the most modern telecommunications networks, including 5G, and they will be staple in the future of 5G security.
With billions invested in 5G, make your network quantum-safe from the beginning. Find out how in this Thales and ABI whitepaper.
5G Data Security Threats and Vulnerabilities
Growing number of connected devices (IoT)
Storing more consumer data
Network functionality virtualization (NFV)
Use of open-source platforms and multi-vendor networks
Distributed nature of 5G networks (multi-cloud, multi-sites, hybrid)
Disaggregated RAN and network slicing
5G Security Solutions from the Edge to the Core
Thales 5G security solutions deliver end-to-end encryption and authentication to protect data across fronthaul, midhaul, and backhaul operations as data moves from users and IoT, to radio access, to the edge (including multi-user edge computing), and finally, in the core network and data stores, including containers.
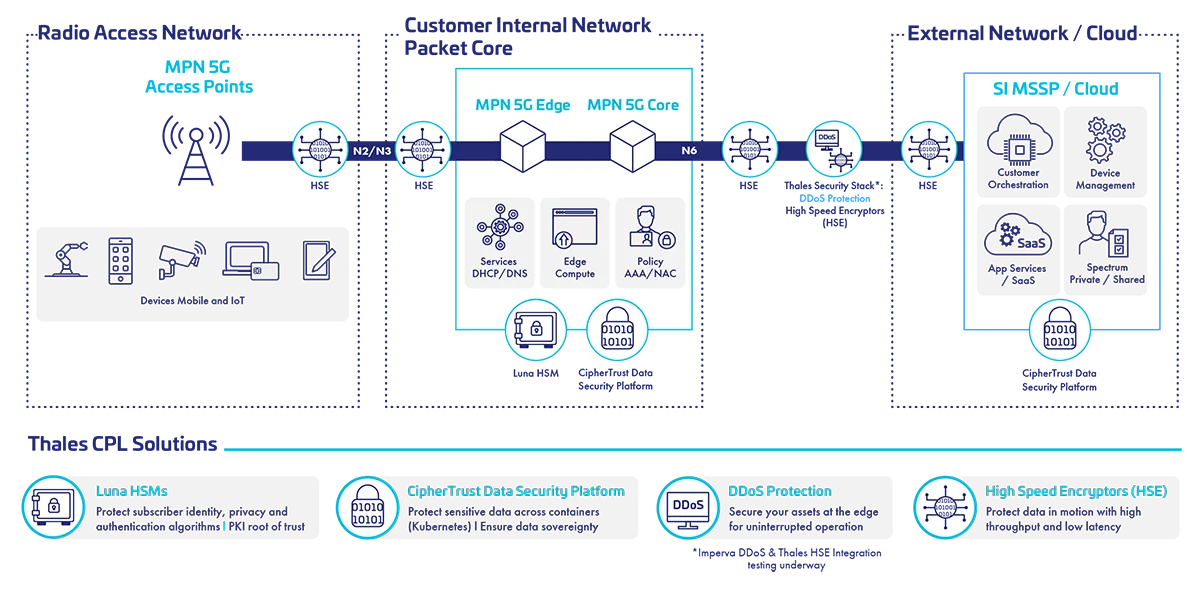
5G Network Security Solutions Diagram
Protect data in motion
Secure data in motion from the RAN/O-RAN to the edge datacenter and back to the core of the network with Thales High Speed Encryptors (HSE).
- Built for modern networks like 5G to provide ultra-low latency, improved performance, compatibility with 5G network architecture, and scalability.
- HSE hardware and virtual appliances provide a multi-point solution and support a wide range of RAN/O-RAN network requirements such as network slicing and are equipped with Transport Independent Mode (TIM), for concurrent encryption over network Layers 2, 3 and 4.
- Compliance and Post-Quantum (PQC) Ready: Provide a FIPS 140-2 Level 3 and Common Criteria EAL 4+ certified solution that’s also vetted by the US Department of Defense Information Systems Agency and NATO. PQC ready and crypto agile, with field upgradeable support for all four NIST PQC algorithm finalists, and more as they evolve.
Learn more about Thales High Speed Encryption (HSE) Solutions in the HSE solution brief, read the Delivering on the Promise of 5G blog or watch the Securing 5G Private Networks video.
Protect virtualized data-at-rest across hybrid IT
Encryption, key management and secrets management and Kubernetes solutions: Thales CipherTrust Manager provides a single pane of glass to meet the complex needs of 5G security, combining tools such as key management, CipherTrust Transparent Encryption (CTE), CipherTrust Cloud Key Management (CCKM), and CipherTrust Secrets Management (CSM).
- CTE provides consistent encryption of sensitive data across all 5G network configurations and virtual network functions with granular access control. This solution encrypts data generated from containerized applications without any change to application business logic.
- CipherTrust Manager centralizes cryptographic key management across multiple cloud vendors and hardware storage providers.
- DevOps, Secrets Management and Kubernetes Security: Secure, deploy and run cloud-native workloads across environments by transparently protecting sensitive data with RESTful calls, secrets management, and establish strong safeguards around data stored in Kubernetes environments.
- Ensure strict access controls and the capability to audit all file operation/access events to protected data (users can monitor usage via SIEMs to better understand who is accessing the information).
Learn more about how Thales and Red Hat Secure Kubernetes Data in a 5G World or watch the Securing Kubernetes and Hybrid Cloud for 5G webinar.
Protect PKI, critical infrastructure and networks
Secure 5G virtual network functions (VNFs), protect the entire PKI-based telco infrastructure and provide a FIPS 140 validated hardware root of trust for the entire network.
- PKI Root of Trust: It is paramount to execute all cryptographic functions within a secure environment to ensure both the integrity and the confidentiality of the keys used to encrypt and decrypt data and perform functions such as code signing. Luna HSMs provide extra security to public key infrastructures (PKIs), including digital certificate management for cell towers.
- Compliance and Quantum Readiness: Luna HSMs provide a FIPS 140 validated and Common Criteria EAL 4+ certified crypto agile solution, enabling quantum safe algorithms to secure users and data today and into the future.
- Thales has optimized its Luna Network Hardware Security Modules (HSMs) to meet the performance, flexibility, scalability, and high availability needed to secure the 5G core network and entire PKI-based telco infrastructure. Learn more in the 5G Luna Network HSM product brief.
Protect subscriber privacy, identities and authentication
Provide end-to-end security of 5G subscriber identifiers (SUCI de-concealment), and subscriber authentication (subscriber authentication vector generation and subscriber keys provisioning flow protection).
- Protect Subscriber Privacy and Identities: Generate encryption keys, store home network private keys, and perform crypto operations to de-conceal SUCI within the Luna HSM to ensure subscriber identities and privacy, including the SUPI, are protected with a hardware root of trust.
- Secure Authentication Vector Generation: Store master keys and run authentication algorithms within the secure confines of the Luna HSM to protect authentication related keys during the authentication execution process.
- Key Provisioning: Store encryption keys for provisioning and storage systems and perform encryption/decryption of provisioning and storage system keys for secure authentication-related keys during SIM personalization and provisioning.
Learn more in the 5G Subscriber Privacy and Authentication HSM Protection solution brief.
Talk to a specialist about 5G security solutions
Get Enhanced Security for Private 5G Networks
Private 5G networks are a key means to support the business and the mission critical needs of today’s enterprises. Security, data management and privacy remain the key drivers for private network adopters.
Learn how Thales can support your private 5G network security strategy, including integration, deployment, and meeting compliance needs.
Ericsson Extends 5G Core Authentication Solution with Thales Hardware Security Module
5G is changing the security landscape. The need for security increases to effectively address a growing number of new use cases, new devices, going well beyond consumer mobile broadband to industries and enterprises. The Ericsson Authentication Security Module integrates the Thales 5G Luna Hardware Security Module to enable communication service providers (CSPs) to provide premium security for markets and use cases that have more strict security requirements.
To accelerate the adoption of 5G and overcome the challenges related to managing highly distributed infrastructures, Red Hat and Thales have partnered to provide integrated solutions to mitigate 5G data security risks. Together, Red Hat and Thales enable telco and cloud service providers to quickly harness the power of 5G across their cloud, edge, and legacy environments while steadfastly protecting sensitive data.
5G Security Resources
Frequently Asked Questions
5G is the next technology standard for cellular networks. Each service area is called a cell, and all the wireless devices are connected by radio waves through an antenna. 5G offers higher bandwidth than previous cellular networks, and higher download speeds of up to 10 gigabits per second.
5G security uses more encryption than previous generations of cellular networks. 5G also is more cloud and software based than previous generations thus allowing potential threats to be identified quicker.
Some of the top challenges to securing 5G are:
- More bandwidth and devices for hackers to breach
- Virtualization along with network slicing could bring more risks if the different layers are insulated from each other
- The need to automate the identification of and defense against all the new threats posed versus manually spotting hacking attempts
5G technology relies on virtualized, cloud-based, and multi-vendor architecture, which introduces unique technical and security challenges. The distributed nature of 5G networks, the growing number of connected devices (IoT), the use of open-source platforms and multi-vendor networks, cloud adoption and increased entry points for cyber-attacks, add to the list of security challenges to address.
Mobile Network Operators (MNOs), NEPs, Private Mobile Network Operators (PMNs), Cloud Vendors, and System Integrators who operate within the 5G ecosystem, need security solutions to address these challenges and protect 5G infrastructure, networks, data and users.
Telco companies, global enterprises and governments, particularly those operating in highly regulated industries like healthcare, mission-critical infrastructure, manufacturing, defense and transportation need 5G cybersecurity solutions to protect the identities of people and devices connecting to 5G networks; the data as it moves across the network; and the applications, infrastructure and sensitive data on 5G networks.
5G improves security with improved data encryption and stronger user authentication. 5G also offers better roaming encryption than 4G.














