Why database security matters
Cyber threats and regulatory pressures demand more than basic security. Whether you're securing structured SQL environments or modern NoSQL systems, Thales provides powerful database encryption and key management that protects your most valuable data without disrupting performance or user access.
Database Security Challenges
Multiple database types and platforms
14% Reported experiencing a recent data breach.*
Diverse deployment environments (cloud, hybrid, multi-cloud)
68% of sensitive cloud data is encrypted still leaving major gaps.*
Limited visibility into sensitive data and user activity
24% have little or no confidence in identifying where their data is stored.*
Complex compliance requirements and audit burdens
78% of enterprises that failed audits had a breach history.*
Database security best practices
Universal database coverage
Protects leading databases including Oracle, Microsoft SQL Server, PostgreSQL, MongoDB, Snowflake, SAP HANA, and more.
Seamless integration
Deploy encryption with minimal to no changes to applications or databases using Transparent Data Encryption (TDE).
Centralizes key management
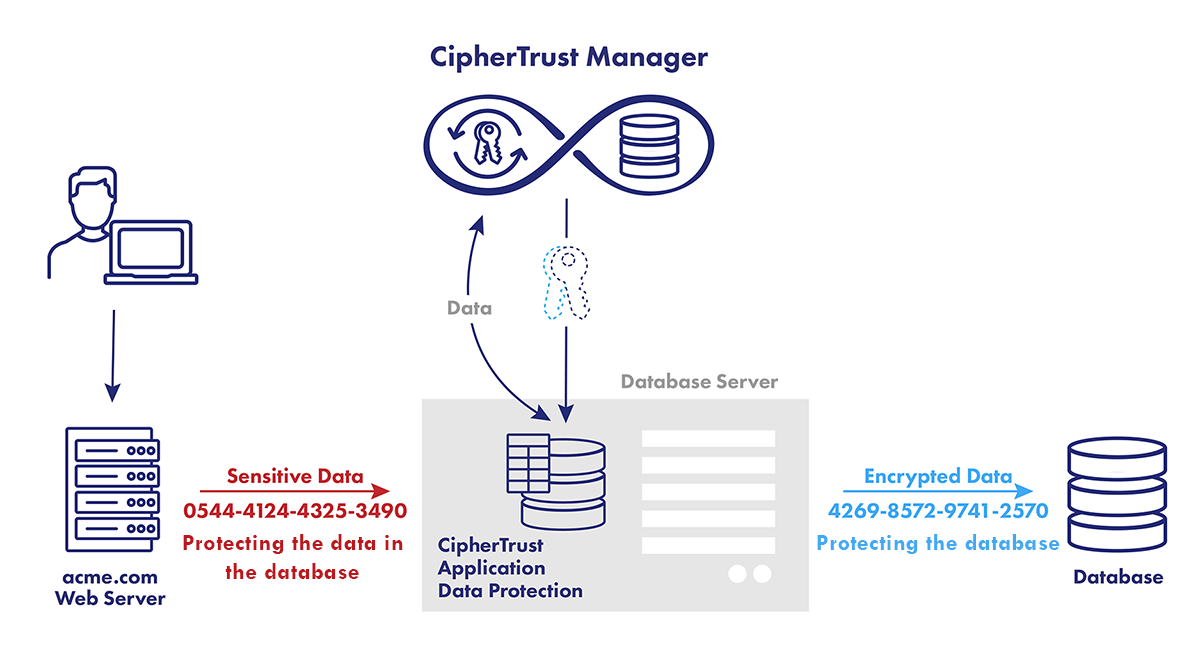
Centralize key management across hybrid and multi-cloud environments. TIP: leverage CipherTrust Manager for this.
Regulatory compliance made easier
Supports organizations in meeting GDPR, HIPAA, PCI DSS, and other data protection regulations.
Database protection portfolio
Oracle Database Encryption
Enable TDE for Oracle environments with centralized key lifecycle management and auditing via CipherTrust Data Security Platform. Fully supports Oracle Wallet and HSM integration using the latest database security tools.

Microsoft SQL Server Encryption
Secure SQL Server data at rest with support for Microsoft TDE, Extensible Key Management (EKM), and integration with Thales HSMs and CipherTrust Manager.
PostgreSQL Database Encryption
Achieve robust encryption in PostgreSQL using Thales solutions for application-level and column-level encryption. Leverage centralized access policies and strong key protection.

MongoDB Encryption
Ensure end-to-end data confidentiality in MongoDB environments. Thales offers native encryption key management integration with CipherTrust Manager and KMIP compatibility for ease of deployment.

Snowflake Database Security
Secure Snowflake data cloud environments with strong encryption, centralized key management, and consistent policy enforcement across cloud platforms.

Data Security for SAP Environments
Protect SAP data using granular database encryption security and tokenization that integrates with SAP HANA and SAP NetWeaver. Ensures full compliance for enterprise-scale deployments.

Compliance & risk reduction
Thales database security solutions simplify compliance with global mandates like:
- General Data Protection Regulation (GDPR)
- Payment Card Industry Data Security Standard (PCI DSS)
- Health Insurance Portability and Accountability Act (HIPAA)
- Federal Information Security Management Act (FISMA)
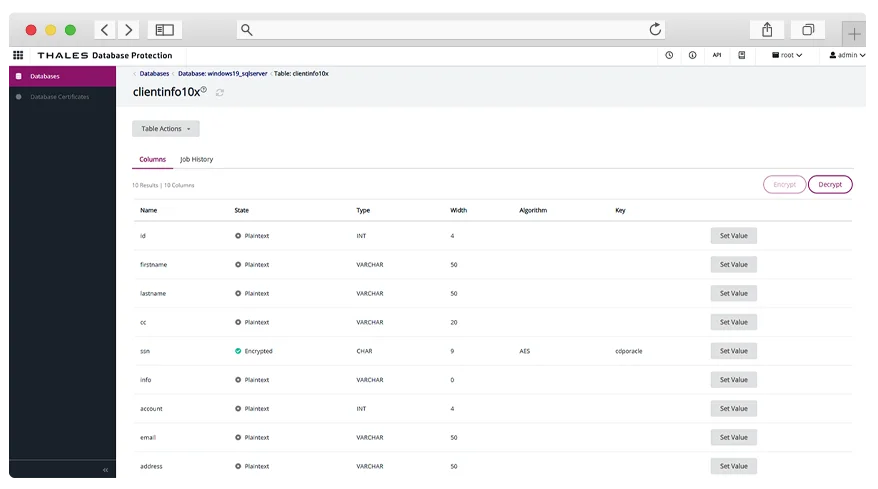
Ciphertrust makes database security easy
Common database security use cases
A major healthcare organization launched a new digital service powered by MongoDB to manage Protected Health Information (PHI). To comply with HIPAA and HITECH regulations, they deployed a database encryption tool and key management, enabling centralized key management, detailed access controls, and encryption at rest, without impacting application performance.
A multinational financial institution uses Microsoft SQL Server and Oracle databases across global regions. By using database security software to centralize key lifecycle management across both environments, they ensure compliance with GDPR and PCI DSS while reducing operational burden.
A utility provider in a highly regulated market can implement CipherTrust Transparent Encryption. a database encryption tool, on SAP ASE and HANA servers with strict role separation, encrypted persistence, and audit tracing. This protects against insider threats, APTs, and ensures only approved roles or processes can access sensitive operational data within their database.
An e-commerce leader using NoSQL database like Cassandra for product and customer data needed to block insider access to sensitive analytics. By deploying CipherTrust Transparent Encryption, a database security tool, and enforcing privileged access controls, they can protect data at rest and prevented DBAs from viewing confidential insights, boosting security and auditability.
A regional bank using PostgreSQL for customer transaction logging faced GDPR and PCI-DSS compliance requirements. Using encryption, they implemented strong at-rest data encryption with privileged user controls, without rewriting applications. A strong tokenization database protection software solution replaced PAN data with tokens, allowing compliance while maintaining query performance.
Thales provides security at scale for more than
30,000 organizations worldwide
$150 Trillion
in interbank money transfers
protected every year
113+ Billion
application attacks
blocked every month
184
countries monitored for threats
every day





Get started today
Ready to secure your databases and simplify compliance?