PCI DSS 4.0 Requirements
The Payment Card Industry Data Security Standard (PCI DSS) is an information security standard that provides a baseline of technical and operational requirements designated to protect payment data and reduce credit card fraud. PCI DSS is intended for all entities that store, process, or transmit cardholder data (CHD) and/or sensitive authentication data (SAD).
The new version of the standard was released on March 31, 2022. Changes from the previous version 3.2.1 include:
- Expansion of Requirement 8 to implement multi-factor authentication (MFA) for all access into the cardholder data environment.
- Updated firewall terminology to network security controls to support a broader range of technologies used to meet the security objectives traditionally met by firewalls.
- Increased flexibility for organizations to demonstrate how they are using different methods to achieve security objectives.
- Addition of targeted risk analyses to allow entities the flexibility to define how frequently they perform certain activities, as best suited for their business needs and risk exposure.
Details about the updates can be found in the PCI DSS v4.0 Summary of Changes document on the PCI SSC website.
What is PCI DSS?
The Payment Card Industry Data Security Standard (PCI DSS) was developed to encourage and enhance payment card account data security and facilitate the broad adoption of consistent sensitive data security measures globally. PCI DSS provides a baseline of technical and operational requirements designed to protect account data and be a part of an overall information security policy.
Who must comply with PCI DSS?
PCI DSS compliance is mandatory for financial institutions, online payment processors, merchants that accept payment cards, and any organization that processes payment card transactions, stores or accesses payment card information, and any service providers that enable business anywhere in the card processing eco-system.
When will PCI DSS 4.0 take effect?
PCI DSS v3.2.1 will remain active for two years after v4.0 is published. This provides organizations time to become familiar with the new version, and plan for and implement the changes needed. The implementation timeline is shown in the image below.
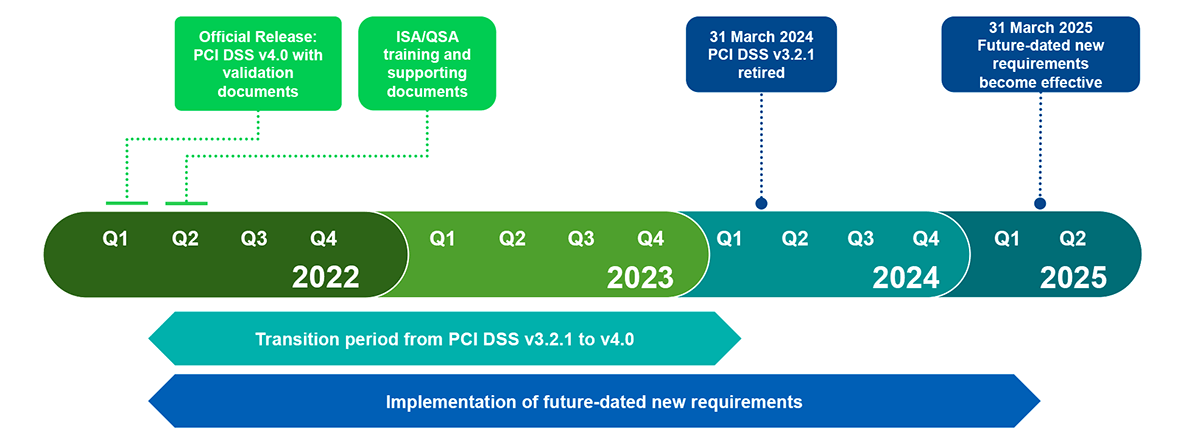
Figure 1: PCI DSS 4.0 Implementation Timeline. Source: PCI SSC
What common obstacles are associated with PCI DSS?
- Failure to comply with PCI DSS compliance requirements can result in fines, increased fees, or even the termination of your ability to process payment card transactions.
- Complying with the PCI DSS cannot be considered in isolation; organizations are subject to multiple security mandates and data protection and privacy laws or regulations. On the other hand, PCI compliance projects can easily be side-tracked by broader enterprise security initiatives.
- Guidance and recommendations linked to PCI DSS requirements include common practices that are likely to be already in place. However, some aspects, specifically those associated with encryption and multi-factor authentication, might be new to the organization and implementations can be disruptive, negatively impacting operational efficiency if not designed correctly.
- It is all too easy to end up with a fragmented approach to security based on multiple proprietary vendor solutions and inadequate technologies that are expensive, complex to operate and create additional vulnerabilities.
- Opportunities exist to reduce the scope of PCI DSS compliance obligations and therefore reduce cost and impact; however, organizations can waste time and money if they do not exercise due diligence to ensure that new systems and processes will be accredited as PCI DSS compliant.
What are the penalties for non-compliance with PCI DSS?
Penalties for non-compliance with PCI DSS can include fines of 5 to 100 thousand dollars per month. Sanctions can also include increased audit requirements and potential shut down of credit card activity by a merchant bank or credit card brand.
Compliance with the Payment Card Industry Data Security Standard 4.0 (PCI DSS)
Learn about compliance with PCI DSS 4.0, the latest update to the Payment Card Industry Data Security Standard, and how Thales can help secure cardholder data across hybrid IT environments.
How Thales Helps with PCI DSS Compliance
Drawing on decades of experience helping banks and financial institutions comply with industry mandates, Thales offers integrated products and services that enable your organization to protect stored cardholder data, encrypt it for transfer, restrict access on a need-to-know basis and protect applications managing payment transactions. In addition, Thales works closely with partners to offer comprehensive solutions that can reduce the scope of your PCI DSS compliance burden.

Addressing PCI DSS 4.0 Compliance Requirements
How Thales helps:
- Discover, analyze and prioritize vulnerabilities.
- Multi-Tenancy and separation of duties.
- Encrypted Non-console administrative access.
How Thales helps:
- Discover and classify cardholder data.
- Encrypt and tokenize cardholder data.
- Protect encryption keys in FIPS 140-2 L3 devices.
- Key and secrets lifecycle management.
How Thales helps:
- Tokenization and encryption of data prior to transmission.
- High speed encryption of data in motion.
How Thales helps:
- Inspect all traffic, detect and prevent web-based attacks with WAF.
- Allow only authorized scripts on payment page.
- Discover, analyze and prioritize vulnerabilities.
- FIPS 140-2 Level 3 root of trust for credentials and keys.
How Thales helps:
- Deny unauthorized access to protected cardholder data and secrets.
- Separation of duties and least privilege access.
- Centrally manage user identities and risk-based authentication policies for cardholder data environments (CDE).
Solutions:
Data Security
Identity & Access Management
How Thales helps:
- Ensure each user is assigned a unique credential.
- Broadest range of authentication methods and form factors.
- Centrally managed policies from one authentication back-end delivered in the cloud or on premise.
Solutions:
Identity & Access Management
How Thales helps:
- Encryption and tokenization of data with destruction of keys.
- Smart cards for physical access control.
How Thales helps:
- Full audit trail of access events to files, keys, secrets sent to SIEM.
- Continuous verification of audit activity 24/7 365
- Machine-learning anomaly detection to identify suspicious behavior.
Solutions:
Data Security
Identity & Access Management
How Thales helps:
- Prevent unauthorized changes to payment pages by allowing only authorized scripts.
How Thales helps:
- Locate structured and unstructured regulated data across the cloud, big data, and traditional data stores.
- Automate data remediation if vulnerable PAN is found outside the CDE.






