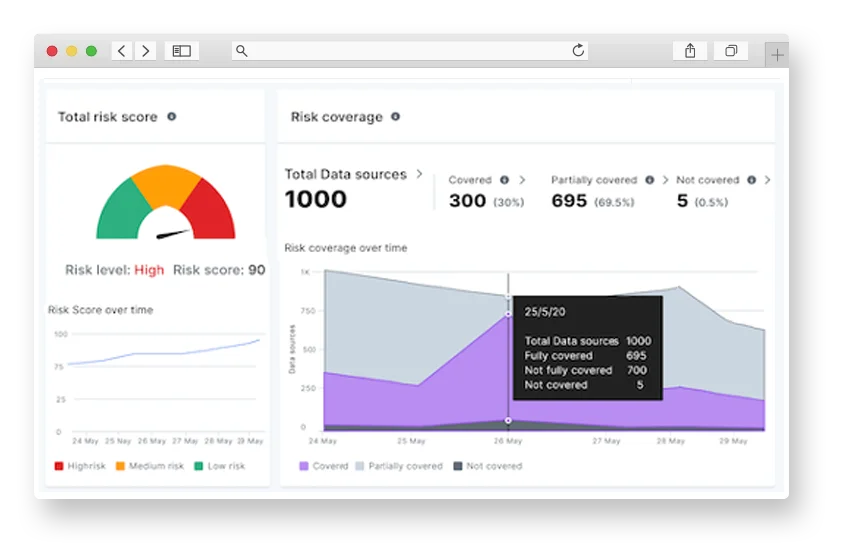
What is Data Security Posture Management?
Data Security Posture Management (DSPM) is a process and framework that helps organizations identify, assess, and manage data security risks across multiple environments, including cloud, on-premises, and hybrid infrastructures.
DSPM protects data across environments, ensuring compliance with data protection regulations. As unified frameworks gain traction, DSPM automates workflows to enhance visibility, protection, and compliance. Unlike other solutions, DSPM simplifies security by providing a clear view of data security and overall risk.

80%
of respondents do not feel highly confident in their ability to identify high-risk data sources
– Cloud Security Alliance: Understanding Data Security Risk 2025
Strengthen your security posture
CipherTrust Data Security Posture Management
CipherTrust Data Security Posture Management precisely identifies the locations of your sensitive data, whether it's in the cloud, on-premises, or within SaaS applications.
Leveraging years of industry expertise, CipherTrust DSPM effectively detects, classifies, protects, and monitors interactions with your most valuable asset: your data.
Data Discovery & Risk Control
- Reign in data exposure due to rapidly expanding and fragmented data.
- Inventory your data estate through data discovery and classification of structured and unstructured data.
- Understand interactions with sensitive data and apply proper security controls.
- Address unknown vulnerabilities like ‘Shadow data’ and unmanaged data flows.
Security & Threat Protection
- Apply data protection, including encryption, and secure the metadata that makes it readable and usable.
- Build post-quantum-ready controls to counter future AI and quantum-powered threats.
- Halt data sprawl by limiting access to authorized audiences.
- Proactively detect external and insider threats through advanced analytics.
Governance & Compliance Automation
- Comply with strict data protection regulations (GDPR, PCI, HIPAA).
- Accelerate data governance with built-in automation.
- Build contextual insights and risk intelligence by integrating tools.
DSPM FEATURES
Gain the visibility, analytics and security needed to face today’s modern risks
Understand your data estate
Know where your data, especially sensitive data, lives and how users and entities interact with it:
- Identify structured and unstructured data across cloud SaaS, and On-premises with database activity monitoring and file activity monitoring.
- Classify data based on sensitivity and business value, while assessing risks.
- Pinpoint which accounts, applications, and APIs access sensitive data.
- Map data flows across repositories to ensure protection and informed decision-making.
Fortify your data security posture
Protect your data from day one and identify where vulnerabilities and exposures exist:
- Implement strong encryption, masking, and tokenization to protect data at rest and in motion.
- Safeguard associated metadata, such as keys and secrets, to align with industry best practices.
- Track data movement through cloud services and monitor access patterns.
- Establish a post-quantum ready foundation to protect data against AI and quantum computer powered threats.
Continuously improve data security operations
Prioritize areas of risk and execute targeted action plans to improve data security:
- Identify exposures and vulnerabilities to mitigate them before cybercriminals take advantage.
- Ensure compliance with international regulations, privacy laws, and compliance frameworks.
- Promote policy-driven data governance.
- Prioritize security measures based on data risk assessments.
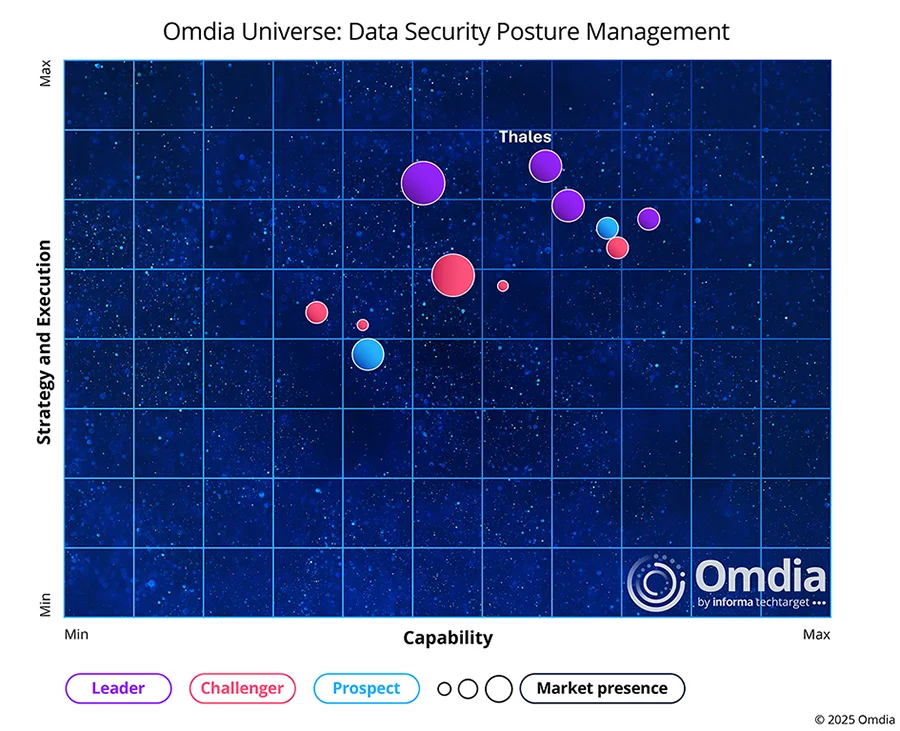
Analyst Research
Thales eclipses other DSPMs
See why we’re a leader in the Omdia Universe Report
Going Beyond DSPM
Organizations must evolve their data protection strategies to incorporate modern DSPM use cases integrating data protection and threat analysis capabilities.
Protect your data and its’ metadata
Implement encryption and safeguard the associated keys and secrets that unlock it to stop malicious access or use.
Reduce data sprawl
Minimize replication and storage outside your environment by preventing unauthorized data sharing through tokenization and data masking.
Prepare for the post-quantum world
Utilize post-quantum infrastructure to combat emerging AI and quantum threats to data protection.
Understand incident relationships
Utilize AI analytics to merge user behavior with application and data context for a better understanding of threats and to combat “low and slow" attacks.
DSPM and DSP working together
By combining DSPM and a Data Security Platform (DSP), organizations enhance how they encrypt meta data, halt data sprawl, identify attack paths to data, and ensure post-quantum readiness.
Thales is ranked as an overall leader in the 2025 Kuppingercole Leadership Compass, Data Security Platforms. Now, with added DSPM capabilities, Thales offers you even more control over data security, as well as the ability to tailor it according to your cloud needs.
IMPROVE Your Data Security Posture
Find Out How CipherTrust DSPM can help your business
Connect with a Thales expert for help tailoring a data security plan to your organization’s needs.
RESOURCES & FAQS
Learn how to discover and protect your sensitive data
Frequently asked questions
How does DSPM work?
DSPM streamlines data protection through a comprehensive, multi-step process:
- Data Discovery and Classification:
Automatically identifies and classifies data across diverse environments, including on-premises, cloud, and SaaS applications, to provide a complete view of your data landscape. - Risk Assessment:
Evaluates data security posture to uncover potential risks like overexposed data, misconfigured permissions, and shadow data, enabling proactive risk management. - Security Posture Analysis:
Analyzes security configurations and vulnerabilities to ensure your data estate remains secure against evolving threats. - Monitoring and Threat Detection:
Continuously monitors data security posture, detecting threats in real-time and providing visibility into emerging security risks. - Remediation and Prevention:
Offers intuitive reporting and dashboards to prioritize vulnerabilities by severity, empowering security teams to address critical issues and enhance overall resilience.
Does CipherTrust DSPM support both agentless and agent-based deployment?
Thales CipherTrust solutions are available in agent-based as well as agentless deployment modes. This allows your security and IT teams to ideally mix and match agent-based and agentless solutions for optimal results, while reducing the total cost of ownership.
What’s the difference between DSPM and CSPM?
DSPM should not be confused with Cloud Security Posture Management (CSPM). While DSPM concentrates on safeguarding and managing data security across various environments, CSPM focuses on detecting and addressing security risks and compliance issues related to cloud infrastructure.
What is unique about CipherTrust DSPM?
CipherTrust DSPM takes into consideration not just identifying risks but also ensuring fundamental protection of data by:
- Deploying industry-leading encryption and protecting the metadata, such as keys and secrets, that keeps the data from being accessed or read by malicious actors.
- Addressing data sprawl through tokenization and masking, keeping data from being shared with unauthorized users, entities, or applications.
- Delivering a post-quantum-ready infrastructure to combat AI and quantum computing-powered threats.
- Connecting AI-powered advanced analytics that merges user behavior analytics with the context of applications, APIs, and data sources.