CipherTrust Batch Data Transformation (BDT) performs high-speed bulk Tokenization/Encryption from source to destination—eliminating the need for Developers (Devs) to create a transformation tool for data migration.
Easy integration with CipherTrust Tokenization/Encryption
Increase Ops Efficiency
- Policy-based configuration
- Remove the maintenance burden across teams
- Rotate keys automatically—easing key lifecycle management
Increase Dev Capacity
- Updates are no longer made in code
- Pass responsibility for data protection to the data security team via simplified APIs
Centralized Management
- No local files -- ensures consistent data protection throughout your environment
- Empowers Data Security Admins to define data policies, update ciphers in realtime
The Forrester Wave™: Data Security Platforms, Q1 2025
Cost savings and business benefits enabled by the CipherTrust Data Security Platform

Thales’ vision for data security is holistic and distinguishing, with market impact resulting from its focus on enabling postquantum preparations and crypto agility. Thales is underway with efforts to combine Thales CipherTrust and Imperva Data Security Fabric into a combined DSP. It boasts an impressive roadmap and robust community strategy for engagement.”
Apply any type of data protection from a single interface
BDT supports tokenization, encryption and data generalization so that organizations can encrypt data in the clear, protect sensitive fields during scheduled ETL jobs and re-protect data to align with new standards.
BDT supports Static Data Masking and Redaction to reveal sensitive data on a need-to-know basis.
- Static Data Masking masks the data that doesn’t need to be accessed, revealing only the data relevant to the group – this is especially valuable for data analysts (pseudonymization) and increased performance for customer service (data is already masked when it arrives).
- Redaction provides an absolute mask that shows a field with redacted data or hides the field.
Centralized Management
Audits become accurate, significantly faster and complete due to visibility of all policies on a single pane of glass showing where Connectors are deployed and the corresponding version numbers.
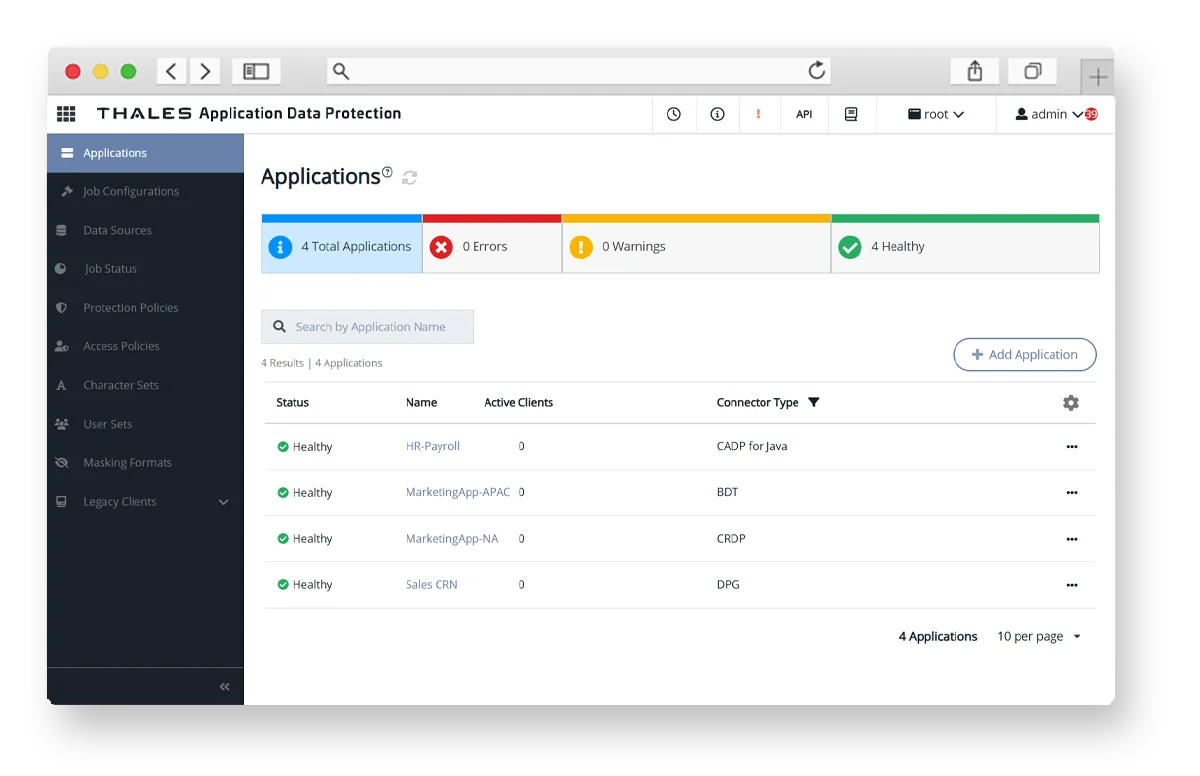
CipherTrust Manager provides a centralized view of every crypto agile Connector’s status—whether operational, offline, or requiring attention, alongside metrics such as health and last check-in time. Data Security Administrators can instantly drill down into individual Connectors for detailed information, configuration adjustments or automated remediation.
We have Tokenization and Encryption solutions to meet your security and infrastructure requirements.
Benefits for each role
With BDT, you have easy integration with Tokenization/Encryption.
- Security
- Efficiency
- High-performance
Reputation is protected, audits are passed, adheres to compliance, does not add to technical debt. IT Operations can easily deploy centrally-managed BDT throughout their environment with containers.
Audits are passed, in compliance, empowered to update data protection whenever needed. They can control the schedule for BDT. They are in full control of the policies, guaranteeing consistency and how the data is protected even when Devs or DBAs use BDT to transform data.
No need to learn crypto or do the data protection updates, does not add to technical debt.



