Why application key management matters
Modern databases rely on encryption, but many organizations still manage encryption keys using native tools, scripts, or application-level storage. This approach creates security, compliance, and operational risk. When encryption keys are stored on database servers or scattered across environments:
- Keys are more easily exposed or misused, increasing the risk of data compromise
- Policies are inconsistent and difficult to enforce at scale
- Auditing key access and usage becomes fragmented and unreliable
- Compliance with standards like PCI DSS, HIPAA, and GDPR is harder to demonstrate
- Key sprawl makes revocation, incident response, and recovery more complex
In cloud, hybrid, and multi-tenant environments, organizations need centralized key control, strong separation of duties, and enterprise-grade auditing to protect sensitive data at rest.
Centralize and simplify your application key lifecycle
Stronger security & separation of duties
Improved compliance & auditability
Unified key lifecycle management
Enhanced cryptographic control & resilience
Centralized monitoring & governance
Scalable for hybrid and multi-cloud environments
Architected for performance, security and scalability
Whether deployed in your data center or consumed as a service, CipherTrust Application Key Management delivers the same trusted security, control, and compliance—without compromising flexibility.
On-premises or delivered as a service with CDSPaaS
- Choose your deployment model: Run CAKM on-premises for full infrastructure control, or consume it as a fully managed service with our NEW CipherTrust Data Security Platform as a Service (CDSPaaS)
- Consistent key management across environments: Manage application and database encryption keys uniformly across on-prem, hybrid, and multi-cloud deployments
- Cloud-native simplicity with CDSPaaS: Eliminate infrastructure management while gaining rapid deployment, built-in availability, and seamless updates
- Centralized visibility and control: A single management interface provides unified policy enforcement, monitoring, and auditing regardless of deployment model
- Enterprise-grade security and governance: Strong authentication, role-based access controls, and separation of duties help meet security and compliance requirements at scale
Key Features at a Glance
- Stronger security & separation of duties
- Improved compliance & auditability
- Unified lifecycle management
- Enhanced cryptographic control
- Centralized monitoring & analysis
- Scalable for large deployments
- Performance & resilience via key caching
- Strong controls with quorum approval
Benefits for Every Stakeholder
- Gains centralized control and visibility over all encryption keys and policies.
- Enforces consistent access controls and separation of duties, reducing risk of unauthorized access.
- Simplifies compliance with standards like PCI DSS, GDPR, and HIPAA through centralized auditing and detailed logs.
- Improves governance, incident investigation, and audit readiness.
- Manages database functions without dealing directly with cryptographic key storage or lifecycle.
- Configures database encryption (e.g., Oracle TDE, SQL Server EKM) through CAKM, ensuring keys are stored externally and securely.
- Avoids manual key handling and potential mistakes, while maintaining database performance.
- Separation of duties reduces exposure to key misuse and insider risk.
- Integrates key management into CI/CD pipelines and infrastructure automation without custom cryptographic coding.
- Ensures consistent application of security policies and automated key lifecycle tasks across environments.
- Reduces fragmentation in key handling across development and operational environments.
CAKM Use Cases
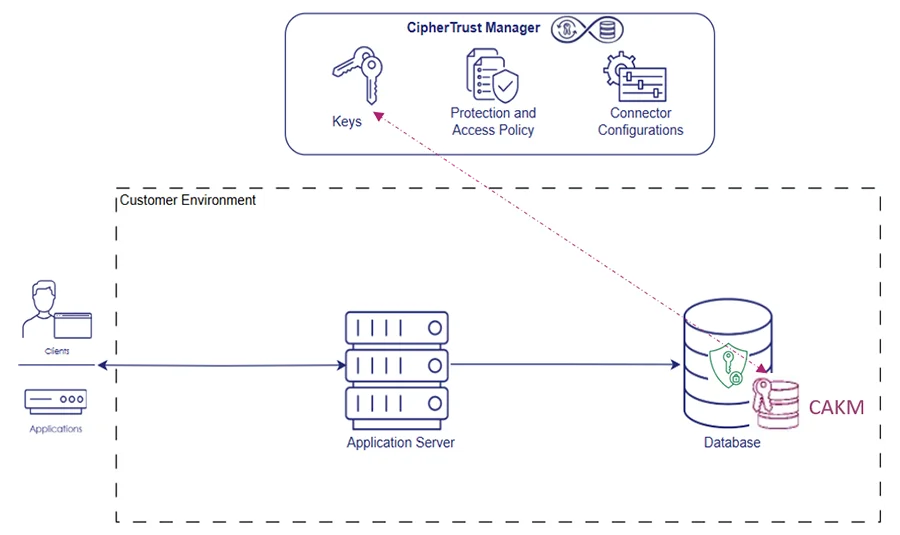
- Centralized key management for database encryption
Externalize and centrally manage encryption keys for Oracle TDE and Microsoft SQL Server EKM to reduce key exposure and eliminate keys stored on database servers. - Regulatory compliance and audit readiness
Enforce consistent key policies, centralized logging, and detailed audit trails to meet PCI DSS, HIPAA, GDPR, and similar compliance requirements. - Separation of duties and insider risk reduction
Prevent DBAs and application administrators from accessing master encryption keys while allowing them to manage database operations securely. - Secure key lifecycle management at scale
Automate key generation, rotation, revocation, and retirement across hybrid and multi-cloud environments, minimizing manual errors and operational risk. - Operational resilience and incident response
Enable rapid key revocation or rotation without database downtime, improve visibility into key usage, and respond quickly to security incidents or key compromise.


