 Scotti Woolery-Price | Partner Marketing Manager, Thales
More About This Author >
Scotti Woolery-Price | Partner Marketing Manager, Thales
More About This Author >
 Scotti Woolery-Price | Partner Marketing Manager, Thales
More About This Author >
Scotti Woolery-Price | Partner Marketing Manager, Thales
More About This Author >
In today’s rapidly evolving digital landscape, data privacy and sovereignty have become top priorities for organizations worldwide. With the proliferation of cloud services and the tightening of global data protection regulations, security professionals face mounting pressure to ensure their data remains secure, compliant, and under their control. The recent Thales and Google Workspace webinar, “Empowering Digital Sovereignty: Google Workspace Client-Side Encryption and Thales CipherTrust,” delivered a wealth of actionable insights for those navigating these challenges.
The Digital Sovereignty Imperative
Digital sovereignty is more than a buzzword. It’s the ability to control your organization’s digital destiny, including the data, hardware, and software you rely on and create. According to the World Economic Forum, over 92% of all data in the Western world is stored on U.S.-owned servers, creating significant dependency and resilience challenges for businesses. New regulations such as GDPR, Schrems II, Gaia-X, and DORA are emerging to advance digital sovereignty for organizations operating in regulated industries.

The Regulatory Landscape: Privacy Laws on the Rise
Over 80% of the world’s population is now covered by some form of national data privacy law, and the pace of regulation is accelerating according to a study by IAPP. Over 260 new global regulations are in the legislative process, with 150 in the EU and U.S. alone. For CISOs and IT leaders, this means that the world’s data is more regulated than ever before, and compliance is no longer optional, it’s a license to operate.
Google Workspace: A Holistic Approach to Sovereignty and Compliance
Google Workspace stands out by offering a cloud-only, zero trust architecture designed to address sovereignty and compliance requirements. Key features include:
- Client-Side Encryption (CSE): Data is encrypted before leaving the client server, and customers have sole control over encryption keys, to enable them to act as arbiters of all access to their data.
- Local Data Storage and Data Regions: Organizations can choose where their data is stored and processed, helping to ensure compliance with geographical regulations.
- Access Controls and Context-Aware Access: Admins can control IP, device, and geographic origin, keeping sensitive data within required regions.
- Zero Trust Secure Architecture: Secure infrastructure and practices inherently reduce risks.
- End-to-End Encrypted Gmail: Secure email for enterprise users.
Key Management and Encryption Approaches in Google Workspace
Organizations seeking to enhance data security and sovereignty in cloud environments often consider several key management and encryption strategies. For example:
- External Key Management (EKM):
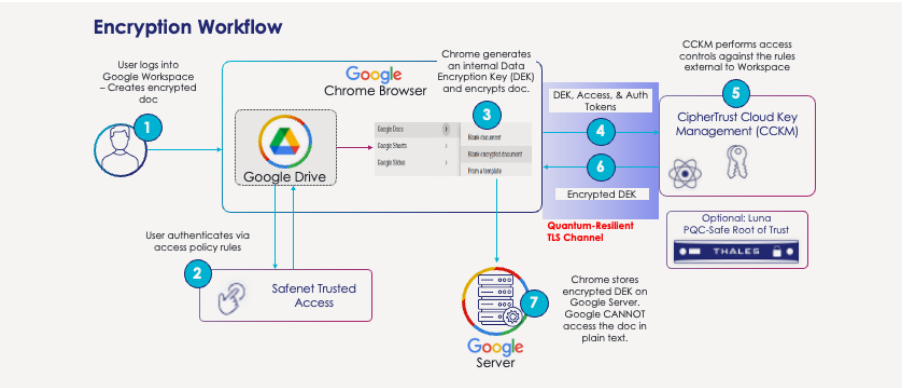
Integrating external key management solutions allows organizations to maintain master encryption keys outside the cloud provider’s environment, often using certified hardware security modules. This approach enables secure creation, control, and storage of encryption keys, separate from where sensitive data is hosted. It can also support a variety of use cases across cloud platforms. - Client-Side Encryption Workflow:
With client-side encryption, documents are encrypted within the user’s browser using internally generated data encryption keys (DEKs). These DEKs are then encrypted with keys managed by an external key manager. Only authorized users can decrypt the DEKs to access documents, helping to ensure that the cloud provider cannot access data in plaintext. Support for multiple identity providers can further enable secure sharing and collaboration across organizations. - Operational and Data Sovereignty:
By maintaining control over encryption keys and access policies, organizations can address regulatory requirements and mitigate risks related to subpoenas, cross-border data access, and privileged user threats. Solutions that enable discovery, classification, and encryption of sensitive data—along with customer-managed key and access controls—can help organizations meet compliance standards and pass security audits. - Quantum-Resilient Data Protection including Gmail:
As quantum computing advances, some solutions are beginning to incorporate quantum-resilient encryption standards to help ensure that sensitive data remains protected against future threats. Google, with support from Thales, offers a cloud productivity suite that protects your data from quantum attacks like Harvest Now, Decrypt Later.
Google Workspace Client-side encryption is foundational to our sovereign collaboration suite. It puts the customer in sole control of their data with in-country encryption keys and zero access for the cloud service provider. For organizations managing highly sensitive or regulated data, CSE for Workspace allows them to balance unparalleled collaboration with granular data sovereignty to unlock productivity gains for all of their employees and even protect their data from quantum computing attacks.
Real-World Impact: Compliance and Resilience
A notable case in France demonstrated the effectiveness of legal and technical safeguards. Thales contributed to a solution that enabled a healthcare client to use public cloud services while retaining control over encryption keys, ensuring compliance with EU GDPR and mitigating risks from foreign access requests. The court’s decision underscored the importance of holding encryption keys in the proper geographic jurisdiction and leveraging trusted third-party key management.
Strategies for Stronger Cloud Control
The webinar outlined several key strategies for securing data in the cloud:
- Native Encryption Services: Managed by cloud service providers (CSPs), offering basic protection but limited customer control.
- Bring Your Own Key (BYOK): Customers generate and import their own keys, gaining more control but still relying on CSP-hosted key management.
- Hold Your Own Key (HYOK): Organizations maintain full control over their encryption keys, even when using third-party cloud services.
- Bring Your Own Encryption (BYOE): Customers manage both keys and encryption outside the CSP environment.
- End-to-End Data Protection (E2EDP): Protects data while in use, in motion, and at rest using confidential computing.
The Shared Responsibility Model
Security in the cloud is a shared responsibility. While providers secure the infrastructure, customers must address defense in depth, anti-malware, network security controls, secure coding practices, and comprehensive logging and alerting. The Cloud Security Alliance (CSA) offers guidance and standards to help organizations prepare for cloud migration and ensure robust security controls.
Take Control of Your Data Sovereignty
As organizations accelerate cloud adoption and digital transformation, the need for robust data sovereignty and security controls has never been greater. Thales CipherTrust Cloud Key Management, in collaboration with Google Workspace, empowers security leaders to take control of their sensitive data, meet regulatory requirements, and build resilient, compliant cloud environments.
Flexible Deployment Options
CipherTrust Cloud Key Management for Google CSE can be deployed in the cloud, on-premises, across hybrid environments, and as a service. To enable a free trial, please visit CCKM as a service from the Thales DPoD Marketplace.
Ready to secure your data?
Explore Thales CipherTrust Data Security Platform solutions and start your journey toward digital sovereignty today.
- Take a self-guided product tour of Thales cloud key management solutions for Google Cloud and Google Workspace.
- Read our integrated solution brief.
- Visit our webpage: Google Cloud Platform Security.