Another day, another data breach. The headlines have come to be all too familiar. Systems that process payments, personally identifiable information (PII), and other sensitive customer and corporate data must be trusted to do so securely. They must be in compliance with government, industry, and corporate regulations, and minimize the impact on operational performance. There are numerous solutions in the market that employ cryptography to protect data end-to-end while in use, in transit, and in storage. But what about the security of the cryptographic keys used within these crypto systems? Their foundation of trust relies on proper safekeeping and management of the keys – and that can be the really tricky part.
Continued attacks on enterprise systems have become more focused and sophisticated, often targeting the keys. Once attackers have access to your keys, they can decrypt past, present and future encrypted data. And they can do this off-site and off-line, where they are less likely to be detected. But not all business applications and data sets require the same level of protection. Only a proper risk and compliance assessment of your critical systems will help you determine which applications need the highest level of protection.
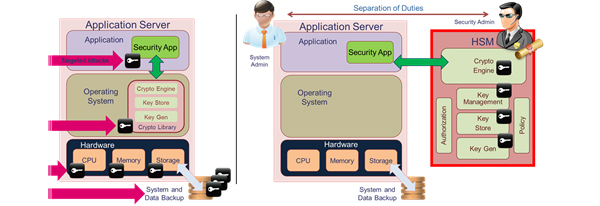
Even relatively low risk situations will require some attention to be paid to key management – controlling the lifecycle of keys from cradle to grave. In general, all keys that are produced by software-based pseudo-random number generators, or used for too long and not retired and replaced, can introduce significant risks. But for your most critical applications you will need to take one big step further and physically protect cryptographic keys and the processes that use them. As shown in the left side of the illustration below, keys that are used and stored on a typical application server are vulnerable in numerous places where they can be exposed to physical and logical attacks.
Specialized hardware security modules (HSMs) remove keys from the host server environment and provide a safe place to generate, store and manage your most sensitive keys. When you integrate an HSM as seen in the right side of the illustration, the keys are now within a dedicated, isolated, and protected device where they can be managed safely under separation of duties and dual control policies – so no single entity is able to subvert the system.
You would be fooling yourself if you installed a strong and expensive lock on your front door, only to hide the key under your doormat. Exposing high value keys in an application server is like hiding your key under your doormat – and attackers will check all the “usual places” to find your keys. The very nature of keys facilitates their discovery. Because keys are created from a random source, they tend to stand out as a result of their high entropy compared with more structured application data.
This brings me back to the systems protecting critical data. As enterprises assess their risks, they are often faced with making trade-offs between security and operational flexibility. Cryptographic processes that protect data either though encryption or digital signing need to be carefully assessed to identify specific authorization requirements and the potential to introduce unacceptable overhead. HSMs not only isolate keys to keep them safe, but they also enforce authorization policies and can provide powerful cryptographic acceleration capabilities to satisfy even the most high performance scenarios.
To learn how good key management is fundamental when protecting your most critical data, view the on-demand Thales/Voltage joint webinar “Protecting Your Sensitive Data Does Not Have to Impact Business Operations.”
