 Haider Iqbal | Director of Product Marketing
More About This Author >
Haider Iqbal | Director of Product Marketing
More About This Author >
 Haider Iqbal | Director of Product Marketing
More About This Author >
Haider Iqbal | Director of Product Marketing
More About This Author >
Workforce IAM has reached a certain level of maturity, but a burning problem lies at its periphery – the problem of managing third-party or partner identities. The complex yet crucial network of partners, suppliers, distributors and other third parties, which forms the extended enterprise, is crucial for delivering strategic outcomes. Efficient supply chains, networked logistics, and distributed channel are essential for an operationally effective and resilient organization; yet we observe clunky, patched up implementations of IAM for these external user constituencies. Today, we’re introducing eXtended Enterprise Access (XEA), powered by the OneWelcome Identity Platform – a modern technology stack tailored to address the needs of third-party users, helping organizations build better collaborations within their extended enterprise and driving the digital transformation agenda forward.
Challenge: Third-party access is now a frontline security and operational problem
Enterprises depend heavily on partners, suppliers, and contractors, but giving them access to internal systems creates risks that organizations often recognize too late. External users need fast access, yet onboarding remains inconsistent and disconnected from security controls. Siloed identity stores, outdated accounts, and unclear ownership create openings for misuse. Attackers target these weak points. Manual processes cannot keep up with modern ecosystems. Organizations need a structured, security-centered model for external access.
Presenting the eXtended Enterprise Access (XEA)
Thales created eXtended Enterprise Access to provide a unified identity foundation for the extended enterprise. Built on the OneWelcome Identity Platform, eXtended Enterprise Access standardizes how organizations onboard, authenticate, authorize, and monitor third-party users. If external collaboration is essential, identity must integrate with the systems that manage those partners and the cybersecurity stack that protects the organization. eXtended Enterprise Access replaces fragmented practices with a predictable, controlled solution to manage the extended enterprise identities lifecycle.
What eXtended Enterprise Access Provides
eXtended Enterprise Access focuses on three requirements that together address the full scope of B2B IAM.
1. Faster and simpler access
Manual provisioning and scattered workflows slow collaboration. eXtended Enterprise Access fixes this with centralized identity management and automated provisioning. Delegated user management enables non-technical partner managers to create, update, and deactivate their own users within defined boundaries without requiring to setup another tenant for each partner organization. Birthright access assigns correct roles automatically based on attributes, reducing delays and removing unnecessary IT involvement.
A simple example is a fictitious insurance provider, InsurCar, which works with brokers, adjusters, repair shops, and assessors. These organizations change constantly, which once created delays and inconsistent access. With eXtended Enterprise Access, InsurCar manages partners through a structured hierarchy.
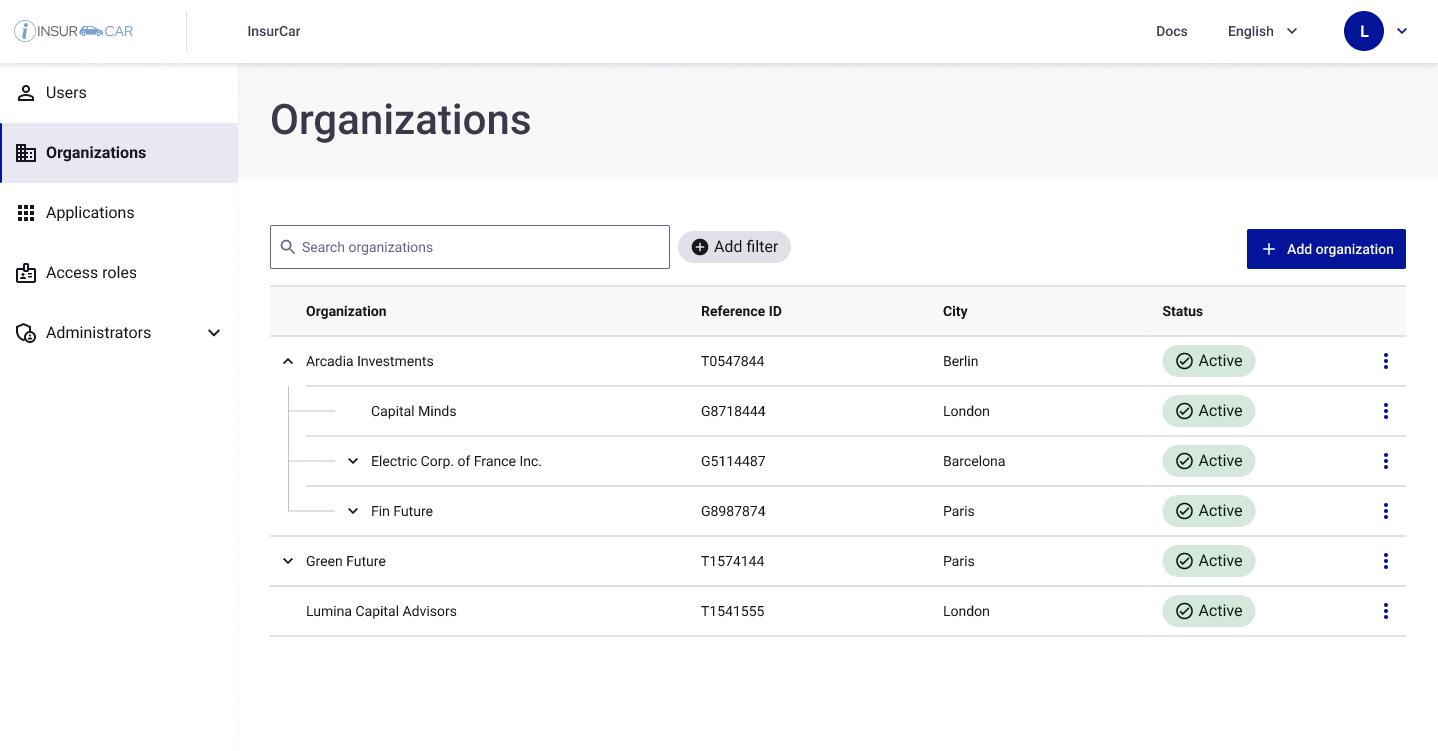
This view shows how an insurance company models complex partner groups. Broker networks, agencies with sub-entities, and regional repair centers are represented cleanly. Each partner manages its own structure, eliminating the manual reconciliation IT previously handled.
2. Reduction of third-party risk
eXtended Enterprise Access strengthens identity assurance through identity verification, multi-factor authentication (MFA), fine-grained authorization among other features – all managed through a single pane of glass for total visibility and control across the boundaries of the extended enterprise. Access aligns precisely to what users need, reducing lateral movement and limiting exposure. This replaces ad hoc decision making with consistent, enforceable controls. For higher assurance use cases, organizations can pair XEA with Thales’s portfolio of phishing-resistant authenticators like the FIDO USB Tokens, or the FIDO Smart Cards that can enable physical access for external users as well.
For InsurCar, external staff rotate frequently. Adjusters work by contract. Repair centers face high turnover. Without clear responsibility, accounts remained active long after staff departed. eXtended Enterprise Access solved this by giving partner administrators authority over their own staff.
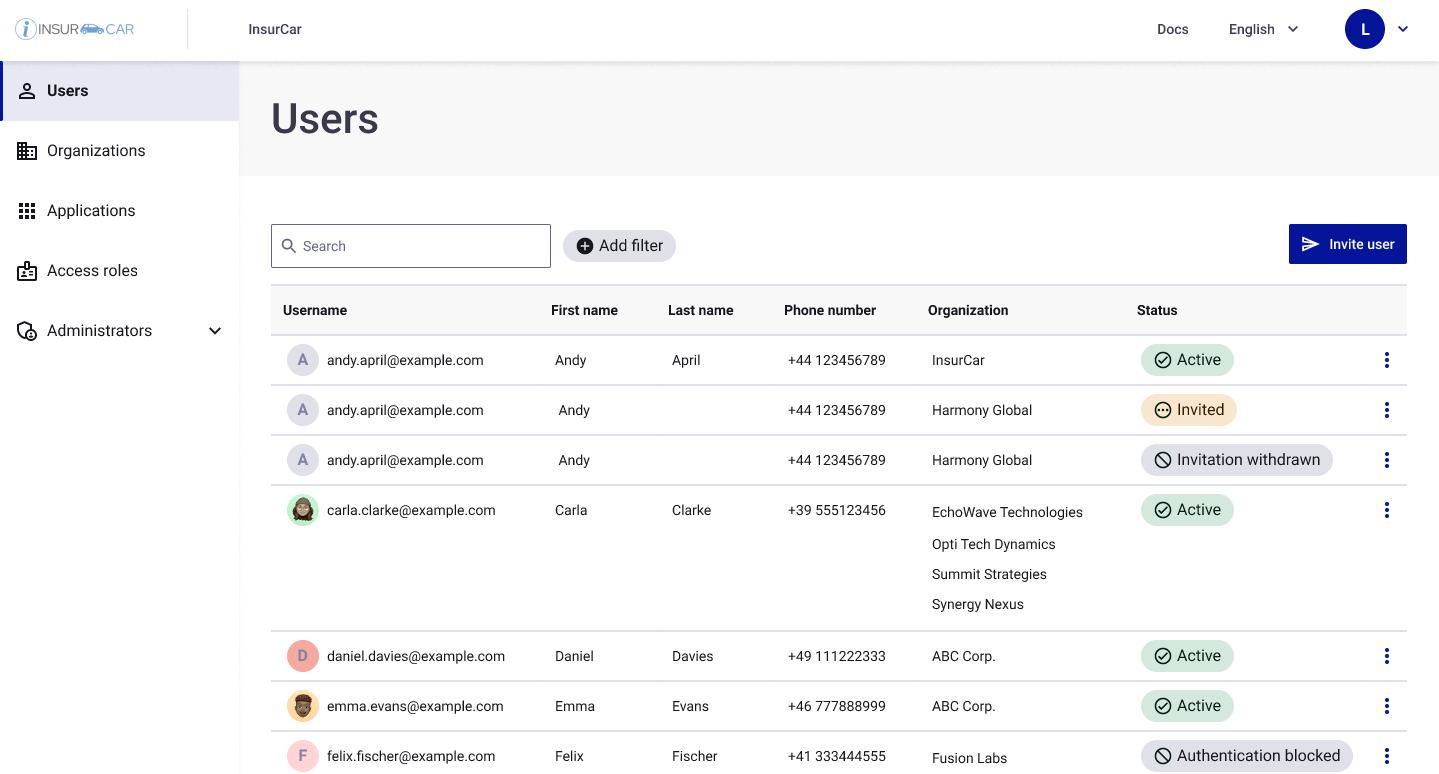
This view shows accurate user states such as Active, Invited, or Invitation withdrawn. Partner administrators invite users, assign roles, and deactivate accounts immediately when personnel change.
3. Lower IT workload through automation and structured delegation
eXtended Enterprise Access moves routine work away from IT. Multitier delegated administration supports partners of any size. Bulk operations simplify onboarding for large populations. Integrations with Partner Relationship Management and Vendor Management Systems automate joiner, mover, and leaver events. IT teams no longer maintain access through spreadsheets or email chains, and support tickets drop significantly.
How eXtended Enterprise Access Enables Real-Time Control
eXtended Enterprise Access connects identity directly to the cybersecurity stack through event streaming and APIs. Identity and access events flow into SIEM, SOAR, monitoring, and analytics platforms in real time. Security teams can track access patterns, detect anomalies, and flag suspicious activity as it occurs. External identity management becomes an active operational function supported by continuous visibility.
Shaping a Safer and More Connected Extended Enterprise
Fragmented external access practices no longer match the speed or scale of modern ecosystems. They slow onboarding, hide risk, and prevent real-time response.
eXtended Enterprise Access (XEA) gives organizations a unified approach to external identities. It improves security, accelerates collaboration, and reduces operational burdens. It also makes real-time monitoring actionable, enabling teams to identify misuse the moment it occurs.
If you cannot detect suspicious partner activity in real time, your current model is leaving gaps. Now is the time to rethink external access and adopt a unified, real-time-focused strategy that matches modern business needs.
eXtended Enterprise Access is available now for new customers.
Attending the Gartner IAM Summit in Grapevine, Texas? Join us at Booth 228 to speak to our experts about eXtended Enterprise Access.