 Lynne Murray | Director of Product Marketing for Data Security
More About This Author >
Lynne Murray | Director of Product Marketing for Data Security
More About This Author >
 Lynne Murray | Director of Product Marketing for Data Security
More About This Author >
Lynne Murray | Director of Product Marketing for Data Security
More About This Author >
In today’s competitive landscape it has become an increasingly important for businesses looking for ways to adapt their data security, governance, and risk management practices to the volatile economy by improving efficiency or reducing costs while maintaining structure, consistency, and guidance needed to manage cyber risks, and ensure compliance.
Application Workload and Sensitive Data on the Move
As organizations increasingly migrate various on-premises applications and data workloads to multicloud environments, the complex and dispersed nature of cloud environments creates significant challenges arising from managing vulnerabilities, controlling access, understanding risks, and protecting sensitive data.
What is Data Security Risk?
Data security is the process of protecting digital information from unauthorized access, corruption, or theft throughout its entire lifecycle. Risks are introduced to the databases, file servers, data lakes, cloud repositories, and storage devices through all the access paths to and from these systems. Most important the data itself, in motion and at rest, deserves the same attention to protection. When properly implemented, a data-centric strategy will protect an organization’s assets and data against cyberattacks, as well as guard against insider threats and human error, which remains among the leading causes of data breaches.
Why does complexity factor into data security risk?
Many factors drive organization’s growth and at the same time security complexity. Complexity inhibits operational stability, and equally impacts security stability. By understanding and analyzing all the sources that contribute to complexity, organizations can implement targeted strategies and effectively automate observability and control to foster a lean and responsive operational team.
In a recent study conducted by Cloud Security Alliance, Understanding Data Security Risk 2025 Survey Report , CSA highlights key areas that organizations are currently addressing:
- High growth with AI-driven innovations and security: As AI accelerates innovation, it also amplifying the threat landscape. Rapid expansion often outpaces the development of needed infrastructures, processes and procedures, leading to ad-hoc measures that increase complexity. Gen-AI also adds a new layer of complexity as it becomes more prevalent in cloud environments that continue to be a prime target due to their complexity and scale.
- Processes and automation:We know that limited staff and inefficient or outdated processes often lead to manual and redundant efforts. This becomes a huge burden on teams who struggle to keep pace resulting in reactive stopgap or workaround actions. All of this to say, manual efforts can be error-prone and time-consuming. At the same time, organizations may experience unnecessary bottlenecks that can exacerbate complexity and interfere with risk identification and security enforcement. Automate as much as possible including data security and risk intelligence to ensure that risks are proactively mitigated therefore reducing escalation of high-urgency incidents.
Only 8% reported that their organization is fully automated, while 54% use semi-automated processes; and 22% rely on manual methods.
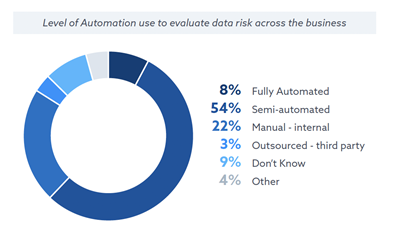
- Standardization: The absence of prescribed security policies, standards, and security tools utilized across processes and systems can lead to inconsistent practices, making governance, security, and posture management execution riskier and more complex. This leads to inefficiencies and conflicting information. Who discerns which alert to prioritize and what action is escalated? It shouldn’t be a judgement call rather an informed investigation based on ongoing contextual integrated insights and severity-level assessment.
Over half of organizations cited they have the tools to identify the number of data sources that are the riskiest but they on average deploy four or more tools to assess and manage risks.
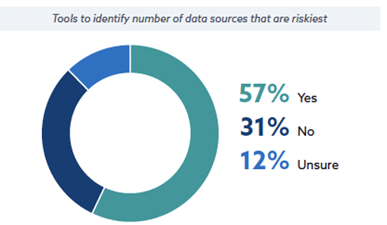
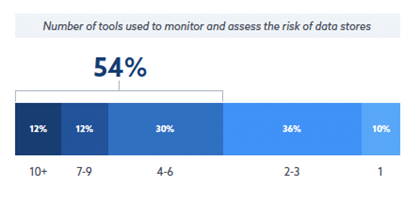
- Regulation and compliance: The need to comply with an ever-increasing array of regulations adds layers of complexity in the form of compliance responsibilities, reporting requirements, and controls. A heavy focus on compliance can leave organizations unprepared for evolving attack surfaces and sophisticated cyber threats. While compliance frameworks like ISO, GDPR, and PCI DSS are essential for establishing baseline security measures, they often emphasize reactive responses and may not cover all emerging threats. For modern data security, organizations need to shift toward a more proactive, risk-based approach featuring continuous compliance monitoring and reporting to meet audit requirements and avoid costly penalties.
- Technology integration: While technology offers solutions for effectiveness and efficiency, the integration of multiple systems without strategic oversight can lead to inefficient security infrastructure, a mismatch of security stack components, creating disconnected silos of security processes. The hidden costs of disjointed tools are fragmented visibility, control, and access enforcement. Traditional compliance and security tools, while essential, often lack the scalability and integration needed for modern and effective risk management.
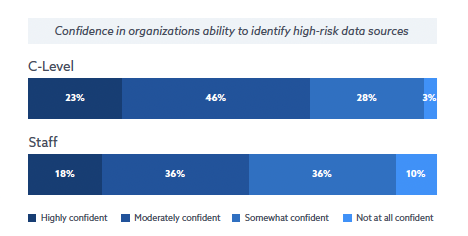
Confidence levels: In a multicloud world, blind spots breed vulnerabilities. We are seeing many organizations lack confidence in identifying high-risk data, even when they have tools in place. Often overlooked are functions that live in different silos such as monitoring, discovery, threat detection, encryption, and access enforcement. This separation or divided approach inevitably becomes hard to maintain a consistent security posture.
The report reveals that management's strategic priorities aren’t compatible with staff's operational realities. For example, 10% of staff reported being “not at all confident” in identifying high-risk data sources, compared to 3% of management.
To help unify disparate security approaches and reduce risk, organizations are investing in comprehensive data security platforms with posture management capabilities that provide real-time visibility into all your cloud activities, from user behavioral activities to data access. Via a single pane of glass to view consolidated logs, alerts, and compliance reports from all data stores to proactively detect threats, risky behaviors, and quickly respond to incidents.
Proactive data security posture management
To enhance security posture, organizations are moving to a proactive, risk-based strategies that involve continuous monitoring, real-time risk assessments, and dynamic actionable workflows. This approach enables the identification and mitigation of vulnerabilities before they are exploited, ensuring a more robust defense against threats.
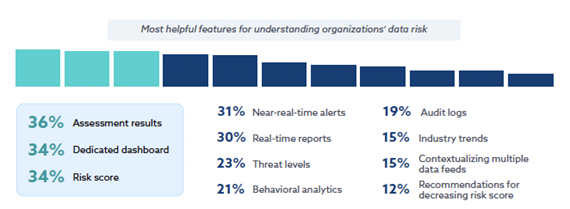
According to the survey results, 36% prioritized assessment results, 34% find a dedicated dashboard is most helpful and 34% are requiring risk scores to understand their organization’s data risk.
Conquering complexity demands a holistic approach, one that combines technology, best practices, and risk awareness. By prioritizing data security throughout your cloud journey, you can ensure your data remains safe, your applications perform flawlessly, and your business thrives in the ever-evolving cloud landscape.
Learn more
Learn more about CSA’s findings and key takeaways and how Thales’ data security portfolio provides a common foundation that enables strategic alignment through insight and prioritization, while delivering operational enforcement bridging strategy and execution. Also, learn how Thales Data Security Posture Management (DSPM) solution simplifies risk management by providing unified visibility with actionable insights that help security teams quickly identify and address the most urgent issues. Thales DSPM protects data across environments, ensuring compliance with data protection regulations.
Get the Report: Understanding Data Security Risk 2025 Survey Report | Resource Library
Visit website: Data Security Posture Management Solutions | Thales
View the Webcast: Data Security Risk Insights for Improving Data Security Posture