What is a Data Security Platform?
A data security platform is designed to protect sensitive information from unauthorized access, theft, and attacks, ensuring business continuity. It secures data across various formats, including databases, applications, and cloud storage, enhancing overall data safety.
Meet the CipherTrust Data Security Platform
The award-winning CipherTrust Data Security Platform is an integrated set of data-centric solutions that remove complexity from data security, accelerate time to compliance, and secure cloud migrations. Thales is proud to have been recognized as an Overall Leader in the KuppingerCole Leadership Compass on Data Security Platforms as well as a Strong Performer in the Forrester Wave and to be featured in Gartner’s Market Guide to Data Security Platforms.
The CipherTrust Platform unifies data discovery, classification, data protection, and centralized management for keys and secrets into a single platform. This results in fewer resources dedicated to security operations, ubiquitous compliance controls, and significantly reduced risk across your business.
CipherTrust Data Security Platform
Discover
Get complete visibility into sensitive data exposure risk across your organization
Protect
Use appropriate data protection mechanisms and guard sensitive data to minimize risk and achieve compliance
Control
Centrally manage encryption keys and configure security policies to retain control of sensitive data on-premises and in the cloud
Monitor
Continuously track data access patterns, user activity, and policy enforcement to detect anomalies, ensure compliance, and strengthen security posture in real-time.
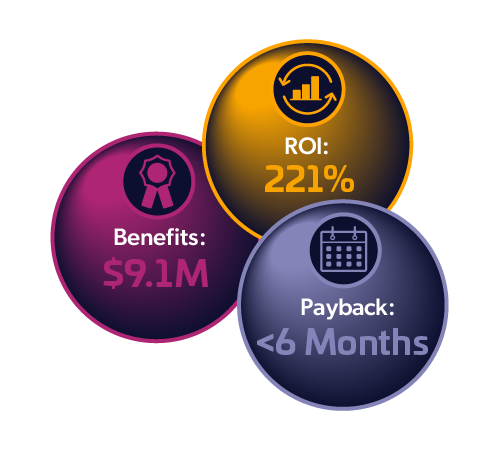
Total Economic Impact™ of Thales CipherTrust Data Security Platform
Thales commissioned Forrester Consulting to interview customers that have implemented the CipherTrust Data Security Platform to assess the benefits and return on investment.
The results: Forrester estimated a 221% ROI over three years from implementing CipherTrust Data Security Platform and payback in less than 6 months.
![]()
How Thales can help
Address data security challenges with CipherTrust
Thales’ CipherTrust Data Security Platform aims to reduce the complexity and risk of managing sensitive data with a broad range of capabilities unifying data discovery, classification, data protection, and centralized management for keys and secrets into a single platform.
Managing compliance and risk
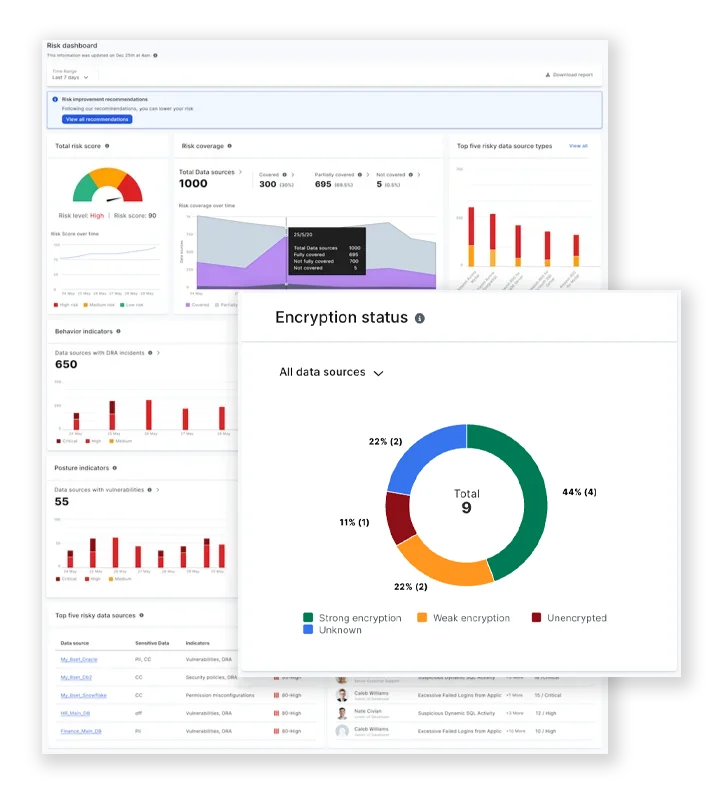
- Data Risk Intelligence: As part of the Data Security Fabric, DRI provides visibility into where your data sources that contain sensitive data are. It identifies the encryption status of each data source and offers recommendations on how to meet encryption goals using the CipherTrust Data Security Platform.
- Meeting regulatory requirements: CipherTrust can help organizations comply with data protection regulations such as GDPR, HIPAA, and PCI DSS.
- Reducing risk: By protecting sensitive data, CipherTrust can help organizations reduce the risk of data breaches and other security incidents.
- File Activity Monitoring: Deliver real-time visibility into file usage, encryption status, and sensitive data access, enabling proactive threat detection and data protection across your organization.
Recommended product
File Activity Monitoring
Gain visibility, meet compliance, and detect threats across all your unstructured data assets with Thales File Activity Monitoring, securing data across servers, cloud services, and file shares.
70%
of enterprises are able to classify only 50% or less of their data.
– Thales Data Threat Report
Robust key management, encryption and tokenization
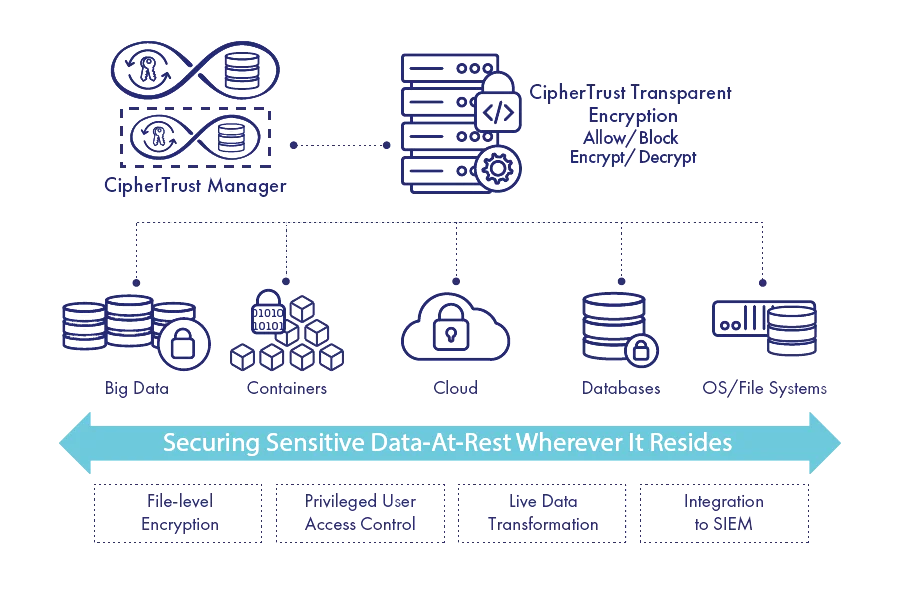
- Protecting data at rest: CipherTrust offers encryption solutions to protect data while it is stored on-premises, in the cloud, or in backups.
- Transparent encryption: The platform supports transparent encryption, which means that data can be encrypted without requiring changes to applications or workflows.
- Key management: CipherTrust provides centralized key management to ensure that encryption keys are securely generated, stored, and managed.
- Replacing sensitive data with tokens: Tokenization replaces sensitive data with non-sensitive tokens, making it difficult for unauthorized individuals to access or misuse the data.
- Dynamic data masking: CipherTrust supports dynamic data masking, which allows sensitive data to be masked or redacted in real time, preventing unauthorized access even when data is in use.
Recommended products
Encryption Key & Management
Streamline encryption key management with CipherTrust Manager for consistent security policies across platforms.
Transparent Encryption
Shield unstructured data from privilege escalation and zero-day ransomware attacks. with CipherTrust Transparent Encryption.
Application Data Protection
Integrate high-level data security into applications seamlessly and protect sensitive data at creation or receipt with CipherTrust Application Data Protection, providing robust.
Database Protection
Secure sensitive data in databases with CipherTrust Database Protection to ensure compliance and protect against unauthorized access.
Discovering and classifying your sensitive data and secrets
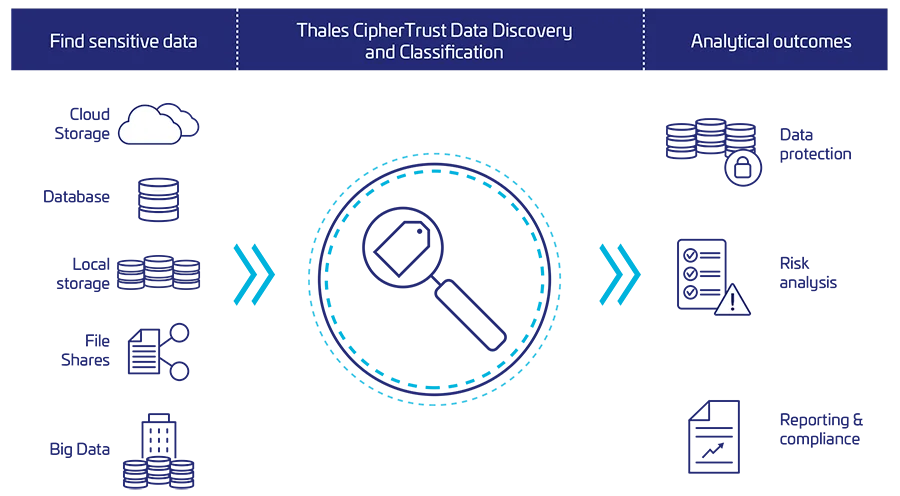
- Identifying sensitive data: CipherTrust can help organizations discover and classify sensitive data across their entire infrastructure, including files, databases, and big data.
- Understanding data exposure: CipherTrust provides visibility into where sensitive data resides and how it is being accessed, helping organizations assess their risk and prioritize protection efforts.
- Secrets Discovery: CipherTrust automatically scans and detects code containing sensitive information (API keys, tokens, passwords, etc.) mistakenly included by developers.
Recommended product
Data Discovery & Classification
Gain visibility into your sensitive data locations to strategize effective migration with CipherTrust Data Discovery and Classification.
70%
of enterprises are able to classify only 50% or less of their data.
– Thales Data Threat Report
Take control of your sensitive data across clouds
- Securing data in the cloud: CipherTrust provides solutions for protecting data in public, private, and hybrid cloud environments.
- Integration with cloud platforms: The platform integrates with popular cloud platforms such as AWS, Azure, and GCP.
- Centralize multi cloud key management for BYOK, HYOK and cloud native encryption keys across any combination of clouds and on-premises with a single UI.
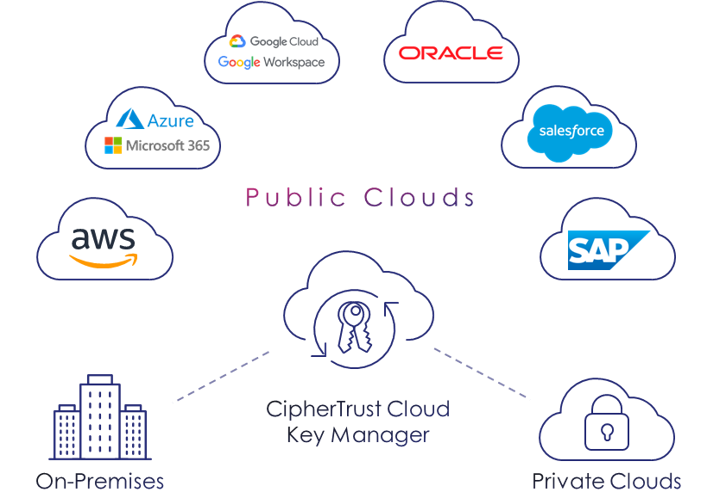
Recommended products
CipherTrust Manager
Retain exclusive control over encryption keys stored in preferred geographic regions with CipherTrust Manager.
CipherTrust Cloud Key Management
Manage the encryption key lifecycle with integrations for BYOK, HYOK, and native cloud keys across multiple platforms.
Integrate Security into Development improving DevSecOps efficiency
- Integrating security into the development process: CipherTrust can be integrated into DevOps workflows to ensure that security is built into applications from the beginning.
- Protecting sensitive data in development environments: The platform provides solutions for protecting sensitive data during development, testing, and deployment.
- Improve Efficiency with Full Separation of DevSecOps Duties: Rapidly secure, deploy and run cloud-native workloads across cloud service providers and speed-up continuous integration and continuous delivery processes.
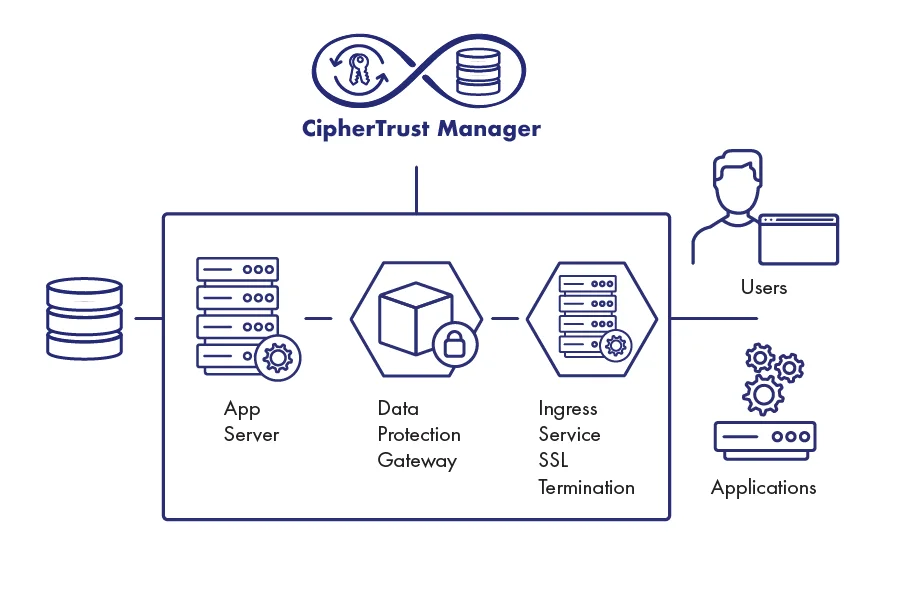
Recommended product
DevSecOps Solutions
DevSecOps helps reduce security risks and bring trust to protect your data within your apps using developer friendly data protection solutions.
Thales GitHub repositories
Get access to sample code, APIs, and open-source solutions.
Manage and automate access to secrets
- Secrets Management: CipherTrust Secrets Management offers a range of capabilities to securely store, manage, and distribute secrets across different developer environments, ensuring that they are protected from unauthorized access and misuse.
- Improve Developer Efficiency: Centralize management for all secret types with a scalable SaaS (Software as a Service).

Recommended products
CipherTrust Secrets Management
Enterprise secrets management solution, powered by Akeyless, protects and automates access to secrets across DevOps tools and cloud workloads.
Data Discovery and Classification
Visualize your sensitive data with efficient data discovery, classification, and risk analysis across data stores.
Enhance your security
See how we can help you discover, protect and control your data
ANALYST RESEARCH
IDC Spotlight: Improving Business Outcomes with Unified Full-Spectrum Data Security
Discover how unified full-spectrum data security improves compliance, reduces risk, and drives business outcomes in this IDC Spotlight Analyst Report.
Explore the CipherTrust portfolio
Recommended resources
Key Features:
- Data Discovery and Classification: Automatically identifies and classifies sensitive data across your organization, helping you understand where your most valuable information resides and assess its risk.
- Transparent Encryption: Encrypts data at rest and in motion, protecting it from unauthorized access and breaches. The platform supports various encryption methods and standards.
- Database Encryption: Secures databases by encrypting sensitive data at the column or row level, preventing unauthorized access and data exposure.
- Tokenization: Replaces sensitive data with meaningless tokens, protecting it from unauthorized use and disclosure.
- Key Management: Centralizes and manages cryptographic keys, ensuring their security and preventing unauthorized access.
- Access Controls: Enforces granular access controls to restrict access to sensitive data based on user roles, permissions, and location.
- Compliance: Helps organizations meet regulatory requirements like GDPR, HIPAA, and PCI DSS by providing tools for data discovery, classification, and protection.
- Cloud Security: Provides solutions for securing data in cloud environments, including cloud-native encryption and key management.
Benefits:
- Enhanced Data Security: Protects sensitive data from unauthorized access, breaches, and data loss.
- Improved Compliance: Helps organizations meet regulatory requirements and avoid fines.
- Reduced Risk: Mitigates the risk of data breaches and their associated costs.
- Increased Efficiency: Streamlines data security operations and reduces the burden on IT teams.
- Centralized Management: Provides a unified platform for managing data security across various environments.
- Scalability: Easily scales to accommodate growing data volumes and complexity.
CipherTrust Platform is managed through a centralized management console. The management console provides a user-friendly interface for administrators to:
- Configure Policies: Define data protection policies, including classification criteria, access controls, encryption settings, and DLP rules.
- Monitor Activity: Track the platform's performance, monitor data access and usage patterns, and identify potential security threats.
- Manage Keys: Generate, store, and manage cryptographic keys used for encryption and decryption.
- Generate Reports: Create customized reports to track compliance, identify trends, and assess the effectiveness of data protection measures.
- Integrate with Other Systems: Connect CipherTrust with other security systems, such as identity and access management (IAM) solutions, to provide a comprehensive approach to data protection.
CipherTrust Platform data is stored in a secure, encrypted repository. This repository can be located on-premises, in the cloud, or in a hybrid environment, depending on your organization's specific needs and deployment model. The exact location of the data repository will depend on the components and features you are using.
CipherTrust Platform is designed to help organizations meet various compliance regulations by providing tools and features for data discovery, classification, protection, and monitoring. Some of the key compliance regulations that CipherTrust can help address include:
- General Data Protection Regulation (GDPR): CipherTrust offers features for data discovery, classification, and access controls that can help organizations comply with GDPR requirements for data protection and privacy.
- Health Insurance Portability and Accountability Act (HIPAA): CipherTrust can help healthcare organizations protect patient data by providing tools for data encryption, access controls, and compliance monitoring.
- Payment Card Industry Data Security Standard (PCI DSS): CipherTrust can help organizations that handle credit card data comply with PCI DSS requirements by providing features for data encryption, access controls, and vulnerability management.
- California Consumer Privacy Act (CCPA): CipherTrust can help organizations operating in California comply with CCPA requirements by providing tools for data discovery, access controls, and data deletion.
CipherTrust Platform installation can vary in complexity depending on specific components, deployment scenarios, and your organization's existing infrastructure. Thales provides detailed installation guides and support.
Factors that can influence the installation complexity include:
- Deployment Model: Installing CipherTrust in a complex, hybrid environment may require more technical expertise than a simple on-premises deployment.
- Integration with Existing Systems: Integrating CipherTrust with your existing infrastructure, such as databases, applications, and network devices, can add complexity to the installation process.
- Customization: Customizing the platform to meet your organization's specific needs may require additional configuration and testing.