 Alex Hanway | Director of Business Development
More About This Author >
Alex Hanway | Director of Business Development
More About This Author >
 Alex Hanway | Director of Business Development
More About This Author >
Alex Hanway | Director of Business Development
More About This Author >
Earlier this year, Oracle and Red Hat announced that Red Hat OpenShift is certified and supported on Oracle Cloud Infrastructure (OCI). It is no surprise that two long-standing heavyweights of the enterprise space are coming together to support customers’ IT modernization efforts given their foundational position in the legacy workloads being updated for the cloud. Now, Oracle and Red Hat offer certified configurations of Red Hat OpenShift, the industry’s leading hybrid cloud application platform powered by Kubernetes, for OCI Compute virtual machines (VMs) and bare metal instances.
The true efficiencies and functional benefits of the cloud depend on using cloud-native technologies. The rush to migrate legacy applications without undergoing a cloud-native transformation led many organizations to incur hefty usage costs. Consequently, many enterprises are now repatriating their workloads to their on-premises data centers. The quandary for many is now whether to rearchitect applications to be cloud- native or to move workloads back on-premises to avoid significant Cloud Service Provider costs. Red Hat and Oracle each address part of this quandary. Red Hat OpenShift makes the cloud-native transformation easier and the jump to the cloud less daunting. Oracle provides one set of cloud services, available in a variety of formats, more cost-effectively than their peers. Together, Red Hat and Oracle are giving large enterprises a reliable path to enjoying real efficiencies in the cloud.
That is still only part of the story for large enterprises. While the technology changes, data security and privacy concerns remain the same. How do they keep their sensitive data safe? How do they comply with regulations governing data protection and privacy for their industries or geographies? And, given a world where large enterprises will often move into the cloud in phases, or permanently keep a hybrid landscape, how can they answer these questions in a highly complex set of environments? Fortunately, Thales, a long-standing technology partner to both Oracle and Red Hat works, with each company to provide answers to these questions to support the cloud journey however that looks.
How to Secure Sensitive Data in Cloud-Native Red Hat and Oracle Environments
Since container-based applications operate far more dynamically than legacy static applications, many DevOps practitioners consider containers’ ephemeral nature to be a barrier against data breaches. However, container-based applications still need the ability to read and write persistent data. Any sensitive persistent data is a target for malicious actors. In cloud architectures, that sensitive data will most likely reside in a cloud provider environment - meaning a third-party data center outside of a customer’s control. The prospect of easily creating data that resides in too many silos, running afoul of regulations, or making a mistake while using or trusting native tools is high.
The Solution: Encryption for Kubernetes
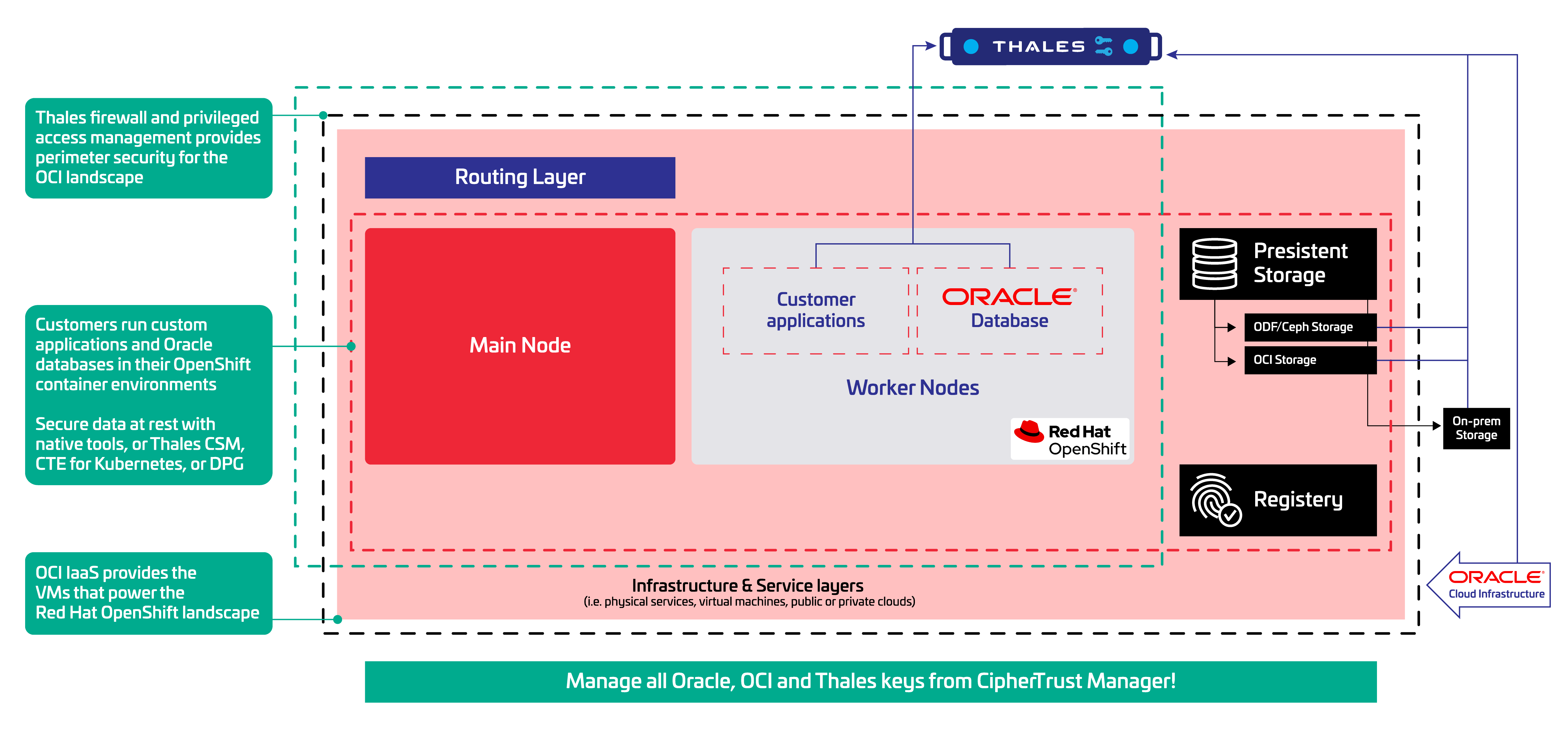
So, how to solve this? The natural place to start any data-centric security conversation is with encryption. Organizations have long used Thales CipherTrust Transparent Encryption (CTE) to secure their sensitive data against privileged users across a variety of landscapes. Its benefit has been its flexibility in securing data without needing to make changes to the database architecture or application code, and the versatility of its policy-based access controls. The wider adoption of Kubernetes prompted Thales to rearchitect CTE to support dynamic container environments.
Similar to the generation of static applications where customers could deploy CTE without needing to change application code, CipherTrust Transparent Encryption for Kubernetes allows customers to secure their data by simply adding a container-based agent to a pod with no coding, SDKs, or architecture changes required. CipherTrust Transparent Encryption for Kubernetes, certified on Red Hat OpenShift, safeguards confidential data on persistent volumes linked to pods operating on Red Hat OpenShift via encryption, process and user-based access control, and data access logging. The large enterprises that run Red Hat OpenShift on OCI can run CipherTrust Transparent Encryption for Kubernetes to keep their data safe irrespective of the storage they are using. Customers can standardize their data-at-rest security rather than accumulating a host of point solutions. And, they protect themselves from risks associated with privileged users, service administrators, and simple, old-fashioned human error. Let’s not forget that the Shared Responsibility Model is the standard practice for CSPs. CipherTrust Transparent Encryption for Kubernetes gives customers the tools to secure their data, address their compliance, and tick all of the necessary boxes associated with the Shared Responsibility Model.
Effective Key Management is Key
Encryption is only half the battle. Organizations must also implement enterprise-level key management to ensure that only authorized users can access the keys to the encrypted data and that it remains safe wherever it resides. In practice, Red Hat OpenShift users will also consume OCI services in the applications running in OCI. OCI’s security-first approach encrypts all OCI data by default. These keys will need managing in order to comply with a range of regulations such as PCI DSS. They also create an additional encryption silo an organization must fit into its overall security management strategy. While Oracle offers key management through its OCI Vault, customers in certain regulated spaces require a greater level of separation than OCI Vault can provide. This is no indictment of OCI Vault or of any of OCI’s security functionality. Rather, these requirements are rooted in the foundational auditing principle of Separation of Duties: no one should ever have access to encrypted data and their keys at the same time. For this reason, Thales worked with Oracle to develop the OCI Vault EKMS service to allow for this necessary separation of duties by using Thales’ CipherTrust Cloud Key Management. Red Het OpenShift users that consume OCI services will be able to manage their encryption keys using the same CipherTrust Manager that protects the certificates and encryption keys in their container-based applications, ultimately simplifying the management of encryption keys throughout the entire lifecycle, including generation, backup/restore, clustering, deactivation, and deletion.
This may sound like an abstract problem, but if you calculate the number of keys generated from the applications, databases, file, and object storage services that comprise a production-level, enterprise-grade application, you’d quickly see that manual management is not a feasible option – especially once you consider the need for things like rotation operations and auditing. Encryption key silos are a very real challenge that consumes time, money. and effort for the large enterprise. Not to mention that when it is done poorly, it presents a critical security vulnerability.
Designed for DevSecOps
Securing credentials that permit access to secured data is just as important as applying the encryption itself. In the cloud-native space, developers must also contend with users who attempt to abuse authorized access granted to specific containers or processes for unauthorized activities. In the cloud-native world, credentials and keys (for containers, APIs, tokens) abound. If left unchecked, the proliferation of these secrets becomes unmanageable and a real security vulnerability. If they are not secured, unauthorized users can take advantage of them, and the access they grant, to access sensitive data – even if it is encrypted.
Centralizing and monitoring these secrets is just as important as ensuring proper encryption key management. By controlling the secrets that developers require, organizations build trust that their applications aren’t leaving open pathways that unauthorized users can take advantage of to breach the organization. Thales through its partnership with Akeyless, protects and automates access to secrets across tools and cloud workloads to ensure dynamic and secure access to credentials such as certificates, API keys, and tokens with CipherTrust Secrets Management (CSM). CSM also enables comprehensive secrets management including static secrets, dynamic secrets, secrets rotation, SSH key management, auditing, and analytics, across hybrid multi-cloud environments, via a scalable as-a-service deployment.
There is a lot to manage for IT security teams, and a lot for developers to incorporate into their DevSecOps practices. Collaborating with Red Hat, Thales is attempting to alleviate that workload. Centralizing key management saves time and money. The container-based architectures for CipherTrust Transparent Encryption for Kubernetes make it easier to deploy. Additionally, Thales CipherTrust Ansible collection allows customers to perform their configurations faster and more efficiently.
When all is said and done, the Thales collaboration with Oracle and Red Hat improves the ability of large enterprises to adopt DevSecOps practices and transform for the cloud. Thales’ CipherTrust Data Security Platform easily plugs into existing Red Hat OpenShift and OCI environments to help DevOps teams secure their data and more efficiently manage their security anywhere. In doing so, it also supports customers as they address the data sovereignty requirements that affect if, when, and how they adopt cloud-based technologies. By storing their encryption keys in Thales CipherTrust Manager and locating those keys in the jurisdiction of their choice, they can remain in control of their data and compliant with sovereignty rules irrespective of where their closest OCI data center is located.
Conclusion
When compliance and data security are off the table as a concern, organizations accelerate their ability to adopt cloud-based technologies. Thales’ ability to secure sensitive data on Red Hat OpenShift and provide customer control for OCI services can enable large enterprises to undertake the digital transformation required to maximize the cloud’s benefit. With the cloud being a fundamental requirement for adopting the next generation of exciting technologies such as AI, accelerating this adoption also means accelerating growth in the bottom line.
Read the solution brief here to learn more about how Thales CipherTrust solutions work with Oracle Cloud Infrastructure and Red Hat OpenShift to secure sensitive data.