 I recently shared two key takeaways from the spate of industry research and surveys released in April: 1) that no organization is immune from cyber attacks; and 2) data-centric security measures are crucial to thwart increasingly sophisticated cyber attacks. In this post, I'll offer a few insights from the 450+ responses we got to our Protect What Matters — Data Security global online survey. I found several of the results eye-opening and thought it would be good to share them with you.
I recently shared two key takeaways from the spate of industry research and surveys released in April: 1) that no organization is immune from cyber attacks; and 2) data-centric security measures are crucial to thwart increasingly sophisticated cyber attacks. In this post, I'll offer a few insights from the 450+ responses we got to our Protect What Matters — Data Security global online survey. I found several of the results eye-opening and thought it would be good to share them with you.
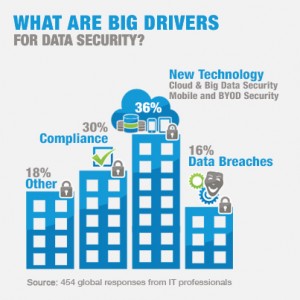
Until about 12 months ago, the vast majority of security conversations centered on compliance. While compliance is still certainly a strong security driver, newer IT trends — like Big Data, Cloud, BYOD and mobile security — accounted for more than a third of our survey respondents' choices, and a full 52% of the respondents named something other than compliance as the primary security driver. It's clear from these numbers that IT professionals have come to recognize (some the hard way, I'm afraid) that compliance doesn't equal security and that new technologies are bringing big security challenges with them.
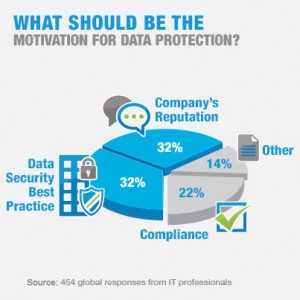
The second insight from our survey was that protecting a company's brand reputation is now an IT imperative as well as a marketing imperative. Nearly two thirds of the survey respondents (64%) felt that protecting the company's reputation and implementing best practice security measures should be the primary motivation for data security. Compliance came in a distant third at 22%. While it's hard to be sure exactly why people respond the way they do, I believe that all the recent data breach headlines we've seen have acted like a big wake-up call for enterprises and government entities alike. Adopting security best practices as a means of protecting the brand has become a pressing boardroom issue.
 And these new threats are getting past legacy protection approaches like perimeter security. While I have no desire to be dramatic, the business value of implementing security best practices cannot be overstated given the cyber threat landscape that's developed. Organizations must find ways to reduce their attack surface and data-centric security should figure prominently because, as I said before, the bad guys are already inside the network, trying to access and steal valuable data.
And these new threats are getting past legacy protection approaches like perimeter security. While I have no desire to be dramatic, the business value of implementing security best practices cannot be overstated given the cyber threat landscape that's developed. Organizations must find ways to reduce their attack surface and data-centric security should figure prominently because, as I said before, the bad guys are already inside the network, trying to access and steal valuable data.
In a few weeks, I'll discuss where IT budgets are being allocated now that everyone's consciousness has been raised. In the meantime, I'd like to hear from you. Does your organization have similar views to those of our survey respondents when it comes to security drivers?

 Tina Stewart | VP, Global Market Strategy
Tina Stewart | VP, Global Market Strategy