We recently performed a small survey where we asked our customers a number of questions around how they were using our data firewall technology. Our goal was to get a sense of how they were using us and what the driver was for choosing Vormetric. Although the sample was small at just 38 respondents, the feedback was fascinating – giving us insight into the decision-making process and the role of security intelligence, privilege user access policies, and a data-centric security approach to those decisions.
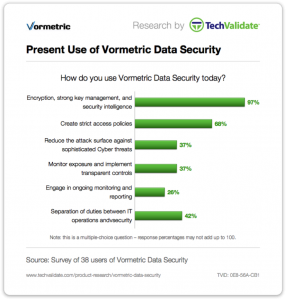
Security Intelligence a Primary Driver?
Clearly, strong encryption, key management, and security intelligence is one of the primary drivers for our customers using Vormetric solutions. The security intelligence technology gives peace of mind by monitoring both real-time events and comparing it to long-term data to identify anomalous usage patterns. By partnering with organizations like Splunk, we’re enabling our users to have immediate results to this information – this ensures they protect what matters – the data. And it does so immediately.
Today, targeted attacks and advanced persistent threats (APTs) are now common occurrences – hackers are actively seeking to steal credit card data, personally identifiable information (PII), critical intellectual property (IP), and other legally protected information to retail to the highest bidder.
Security Information and Event Management (SIEM) solutions monitor both real-time events and a mountain of long term data to find anomalous patterns of usage, qualify possible threats to reduce false positives, and alert organizations when needed. SIEM solutions are strong tools, but can be blind to possible threats to your protected data. By combining SIEM together with Vormetric Data Security products you can identify anomalous process and user access patterns for investigation. Vormetric logs detail the processes and users accessing protected data. If SIEM analysis of log information shows a usage pattern inconsistent with that user or process profile, this could identify an APT attack, or malicious insider action. For example – you might see an administrator or process suddenly accessing volumes of data when their typical usage is light or an auditor accessing portions of a database unrelated to their work.
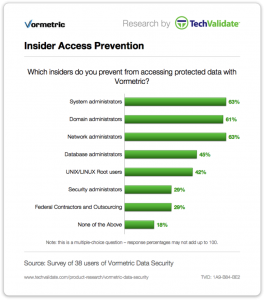
Preventing The Next Edward Snowden
Another serious pain point for our customers is clear: insider access. The recent story of Edward Snowden and the unfettered access he achieved to highly sensitive information at the NSA is a perfect example of this type of access. Snowden was a network admin contractor, yet, due to his role, he retained “super user” administrative access – rights that were simply too broadly assigned. Similar to other roles (system administrators, database administrators) he received access to information he simply didn’t need. The results remain on the front page of major newspapers, even today.
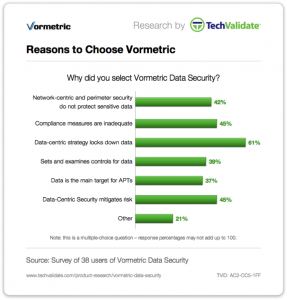
Developers Didn’t Change One Line of Code
Our customers clearly have high confidence of our ability to “lock down data.”
But what was one of the most important validations by our customers was what they had to say about the relative simplicity of our product. Ease-of-use was a consistent message. While anonymous, the content is still quite telling. You can probably guess that my favorite is “Stupid Simple,” but “developers didn’t have to change one line of code” is definitely a close second. Have a look at some of my other favorites below:
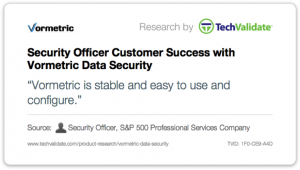


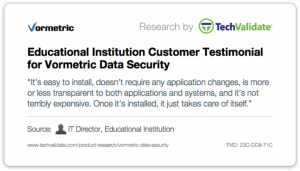

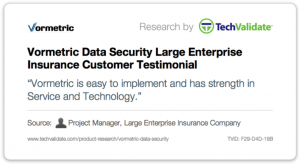 There is much to takeaway from these survey results, but top-line learning is that while the perimeter may not be dead, it maybe on life support. In any event, it’s certainly not keeping the bad guys out, nor is it helping to reduce the attack surface once they are inside. This survey has highlighted the broad swath of organizations, our customers, that are embracing strong data security measures as a key approach to their security. Hearing, in the words of our customers, that our solutions are “stupid simple” really plays to our ethos of delivering the best product we can – both in terms of quality and in terms of ease-of-use. It is important to use that we do anything we can do to make our customer’s jobs - to Protect What Matters – confidential company information as easy as possible. And it is all the better when it doesn’t impact the business.
There is much to takeaway from these survey results, but top-line learning is that while the perimeter may not be dead, it maybe on life support. In any event, it’s certainly not keeping the bad guys out, nor is it helping to reduce the attack surface once they are inside. This survey has highlighted the broad swath of organizations, our customers, that are embracing strong data security measures as a key approach to their security. Hearing, in the words of our customers, that our solutions are “stupid simple” really plays to our ethos of delivering the best product we can – both in terms of quality and in terms of ease-of-use. It is important to use that we do anything we can do to make our customer’s jobs - to Protect What Matters – confidential company information as easy as possible. And it is all the better when it doesn’t impact the business.
If you’d like to hear more directly from our customers, you can find some more success stories here.