 Jose Caso | Product Marketing Manager, IAM
More About This Author >
Jose Caso | Product Marketing Manager, IAM
More About This Author >
 Jose Caso | Product Marketing Manager, IAM
More About This Author >
Jose Caso | Product Marketing Manager, IAM
More About This Author >
Introduction: A messy bowl of terminology
Identity management is no longer just about employees. The B2B IAM – The Hidden Value of Third-Party Identities research revealed that more external identities interact with an enterprise’s cloud, network, and devices than traditional employees. While internal employees remain the largest single group accessing corporate networks (29%), non-employee external identities now represent nearly half (48%) of total users.
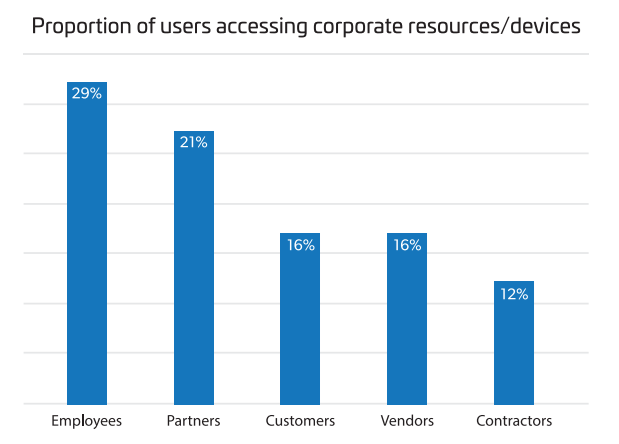
Source: S&P Global Market Intelligence (2024). B2B IAM – The Hidden Value of Third-Party Identities.
Yet, despite the growing importance of managing external identities, the industry lacks a unified definition of B2B IAM. Some call it third-party identity management, others bundle it under CIAM or workforce IAM, while some see it as federated identities or delegated administration. Very recently, Gartner introduced the term partner IAM during their North American Identity & Access Management Summit in December. The lack of consensus makes it difficult for businesses to evaluate solutions and compare their value effectively.
Why can't anyone agree on what B2B IAM is?
There are several reasons why B2B IAM remains a fragmented category:
- It didn’t emerge as a standalone category.
Unlike CIAM (which grew with the explosion of consumer digital services) or traditional IAM (which evolved with internal IT security needs), B2B IAM sits awkwardly between them. It deals with external users who aren't employees but aren’t consumers either – such as partners. - Different vendors define it in their own way.
Some vendors position B2B IAM as a subset of CIAM, others of IGA. Others treat it as an extension of Workforce IAM. Some even consider it a combination of identity federation, delegated administration, and access governance. - The use cases vary widely.
B2B IAM can mean supplier portals, distributor extranets, secure third-party integrations, or even cross-company collaboration tools. Each use case demands different capabilities, making a universal definition even harder. - Enterprise buyers don’t know what to search for: Since an industry-agreed term doesn’t exist, they look for partner access management, third-party identity, supplier login solutions, or other highly specific terms. This further muddies the waters because vendors respond by tailoring their messaging to specific problems rather than defining a cohesive category.
What makes a solid B2B identity solution?
Instead of arguing about terminology, let’s focus on what matters, the capabilities that define a strong B2B IAM solution. Here’s what businesses should look for:
Identity Federation: A necessary but insufficient solution
Identity Federation is a method that allows users to access multiple systems using a single set of credentials, typically managed by an external identity provider (IdP). It is often implemented through standard Single Sign-On (SSO) protocols, such as SAML or OpenID Connect, to enable authentication across different organizations, without requiring each party to maintain separate user accounts.
Identity Federation is one of the few identity terms we have a consensus on, but it is not the solution for all B2B relationships needs. Many vendors claim they provide B2B capabilities simply because they support federation. The reality is:
- Not all of your partners have an identity provider (IdP) to federate with. Think about your local insurance broker or a small medical practice. They probably aren’t running their own IdP.
- You don’t trust every partner the same way. Different external users require different levels of security and oversight.
While federation is useful, a true B2B IAM solution must do more than just connect to an IdP. It must onboard users not only to your platform but also to your policies because your security posture is only as strong as your weakest link.
Delegated management: Not all delegation is created equal
Delegated management allows organizations to distribute administrative control over user access and permissions, reducing the burden on central IT teams. It enables designated individuals—such as business managers, team leads, or external partners—to manage users within their own scope without requiring IT intervention.
Delegated management is a must for B2B IAM, but not all delegation models are created equal. Many vendors claim to offer delegation, but often, it’s limited to IT administrators. This limitation forces IT teams to manually manage external users, defeating the purpose of delegation.
A robust B2B IAM solution should:
- Enable business users (not just IT admins) to manage access for their own teams.
- Offer granular controls, so different types of partners have different levels of access.
- Ensure security without creating bottlenecks.
Externalized authorization: Fine-grained control over access
Externalized authorization allows organizations to manage access policies outside of individual applications, ensuring centralized, scalable and consistent enforcement across different systems. Unlike traditional role-based access control (RBAC), externalized authorization enables dynamic, real-time access decisions based on attributes, risk signals, and contextual factors.
Most vendors rely on RBAC, which assigns users predefined roles with static permissions. While effective for broad access control, RBAC alone often results in over-provisioned accounts, granting users more access than they require. This can increase security risks by expanding the attack surface and limiting the ability to enforce more granular, risk-based access policies. Instead, organizations need fine-grained authorization that allows them to:
- Control access at the attribute and action level, not just by role.
- Define context-based access policies (e.g., restrict certain actions based on location, device, or risk level).
- Reduce the risk of excessive permissions while ensuring users can do their jobs efficiently.
Privacy and consent management: an overlooked requirement
Privacy and consent management is often seen as a consumer IAM concern, but businesses must comply with privacy regulations just like they do for consumer data. Whether dictated by General Data Protection Regulation (GDPR) in Europe, California Consumer Privacy Act (CCPA) in North America, or industry-specific mandates, companies must:
- Allow external users to manage their own consent preferences.
- Provide transparency about how their data is used.
- Ensure compliance with global privacy laws while enabling seamless access.
Identity verification and multi-factor authentication: Protecting against identity-based attacks
With the rise of identity-based attacks, verifying that the person behind the keyboard is who they claim to be is non-negotiable. We’ve seen high-profile breaches where attackers exploited weak identity verification processes to gain unauthorized access.
A strong B2B IAM solution should support:
- Adaptive identity verification, requiring additional proof for high-risk actions.
- Strong authentication beyond passwords (e.g., passkeys, FIDO2, biometrics).
- Integration with fraud detection tools to flag suspicious behavior.
Does it matter that we can’t agree?
Yes and no.
No, because organization just want their problems solved.
At the end of the day, whether we call it B2B IAM, third-party identity management, or delegated administration, the goal remains the same: enabling secure, seamless access for external users at scale.
Yes, because clarity helps decision-making.
Without a clear category, organizations struggle to compare solutions, and vendors waste time explaining what they do instead of focusing on why they solve the problem better.
A call for simplicity
Rather than obsessing over labels, we should focus on solving real challenges in external identity management:
- How can businesses give third parties seamless access without IT bottlenecks?
- How do we balance security with usability?
- How do we reduce complexity for external identity lifecycle management?
Maybe it’s time we stop treating B2B IAM as a rigid category and instead focus on the key capabilities that matter whether we call it B2B IAM, partner or third-party identity management, or something else.
Conclusion
Much like how there’s no one "true" recipe for noodle soup, whether it’s ramen, pho, or pasta, B2B IAM may never have a single definition. And that’s fine. The real focus should be on making external user access work, as seamlessly and secure as possible without overwhelming your IT teams, no matter what we call it.