Data encryption is being embedded across a wide range of applications, accelerated by recent breaches and government revelations. Now the move is on to take control of encryption keys through centralized key management based around a common set of policies and procedures to enforce proper data access and use. Security experts have long recommended a multi-layered security strategy, as a single point of vulnerability is often exploitable. With back-up data being the proverbial “sitting duck” target, it’s no surprise that data-at-rest application vendors are also seeing more demand to offer encryption capabilities in data backup devices.
Although encryption adoption has increased for traditional data center storage—including tape libraries, disk arrays and encrypting switches—the next wave of expansion into big data, cloud storage, and backup appliances is now occurring for an end-to-end approach. With this in mind, Thales keyAuthority can help enterprises more efficiently keep up with compliance and auditing goals across these new, mixed-use environments.
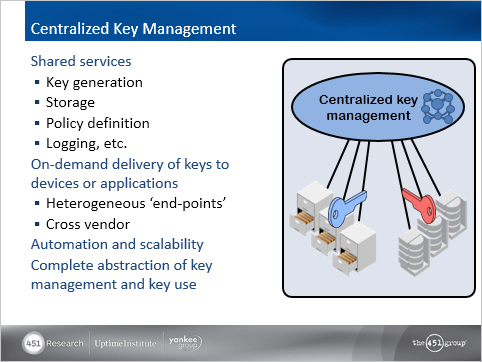
For more insight as to how organizations are solving data-at-rest encryption and key management challenges, Thales and partner Sepaton have joined together, along with The 451 Group, to present an on-demand webinar: “Demystifying Encryption of Data at Rest”. Learn how reliable encryption and centralized key management, based on industry-standard KMIP support, help reduce costs and complexity though a best practices approach to data protection that provides high assurance.
