Regardless of the features, the brand name, the key management system, or the encryption method, network encryption solutions can be classified into two fundamental categories consisting of Microprocessor-based encryption and FPGA-based encryption. Both of these implementation methods are capable of encrypting data, however, the tradeoffs between convenience and performance must be considered when deciding which method is appropriate for a given use case.
Microprocessor-based Encryption
Microprocessor-based (software) encryption is most often found embedded in devices such as routers, switches, and firewalls. These devices are each optimized for their respective main functions and, in an effort to upsell and differentiate, encryption has been added for versatility and convenience. Microprocessor-based encryption solutions are good fits for a variety of data-in-motion security applications, however, convenience always comes at a price. As an example, mobile phones are now the most widely used multipurpose devices.
Designed originally for telephone conversations, mobile phones are also MP3 players, cameras, calculators, and virtually anything else that can be enabled by its microprocessor and software. Although these devices are convenient, you will not likely see a professional photographer using a phone to capture a difficult photograph of, say, an eagle in flight. And performance can be another issue. Take for example your favorite song streaming over Bluetooth and playing over high-end speakers at a party, only to be suddenly paused as the sound of an incoming call is announced to everyone within earshot. Convenience is a valuable aspect of these devices and for those who are neither professional photographers nor discriminating audiophiles, a phone might just fit all of your needs. But for those who require best in class results, single-purpose standalone devices dedicated to the task at hand are always the solution of choice.
FPGA Encryption
FPGA-based (hardware) encryption devices are used in most single-purpose hardware encryption solutions like the Thales Datacryptor. FPGAs are hardware devices that can be programmed to process and encrypt data at very high speeds and with extremely low latency. The difference in performance between a Microprocessor-based encryptor and an FPGA-based encryptor can be astounding. Latency is a key measurement used to determine the efficiency of an encryption device and is generally described as the time it takes to receive a packet, encrypt it, package the data, and send it back on its way. Microprocessor latency is measured in milliseconds while FPGA latency is measured in microseconds. And for those who are counting, FPGA latency is measured as thousands of times more efficient than microprocessor latency. At speeds of 10Gbps and higher, the negative effect of microprocessor latency on performance grows exponentially.
Not All Data Frames Are Created Equally
As previously discussed, Microprocessor-based solutions take longer to encrypt frames than FPGA solutions as measured by latency. To compound the issue, data frames come in a variety of sizes. For example, voice and video data frames are considerably smaller than traditional “file transfer” data frames. In a Voice over IP phone call, small data frames are fast and plentiful and they create a tremendous burden on Microprocessor-based encryption solutions. FPGA-based encryption solutions process each and every data frame at the same low latency which translates into consistent encryption performance regardless of frame size. A similar issue exists with large packets such as jumbo frames. Microprocessor-based encryption solutions struggle with jumbo frames because it takes a longer amount of time to encrypt larger packets. FPGA-based encryption solutions process jumbo frames with the same consistency in performance as small, Voice over IP data streams.
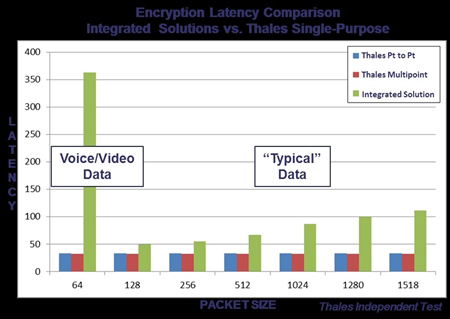
Network traffic is a continuous mix of dissimilar data types and frame sizes. At certain times of the day, VoIP traffic might consume a much larger percentage of your bandwidth than at midnight, when there are fewer employees and large data backups are underway. As your network traffic continues to change, FPGA-based encryption solutions continue to deliver consistent performance regardless of the data types being set into motion whereas microprocessor-based encryption solutions fluctuate in efficiency.
Selecting the Appropriate Tool for the Job
Certainly there are applications in which microprocessor-based encryption solutions embedded into switches, routers, and firewalls make sense. But it is quite clear that these embedded solutions should only be considered when convenience is a priority and performance is not a major concern. A photographer might only get one chance to capture that amazing photograph of an eagle spreading its wings to take flight. You can be certain that the photographer would choose his best camera to seize the opportunity.
