With near daily reminders in the media about how often bad actors are able to penetrate traditionally safe enterprise perimeters and end point security, many of our customers a taking a look at how best to extend their capability to detect attacks in progress and highlight accounts that may be compromised.
With near daily reminders in the media about how often bad actors are able to penetrate traditionally safe enterprise perimeters and end point security, many of our customers a taking a look at how best to extend their capability to detect attacks in progress and highlight accounts that may be compromised.
<ClickToTweet>: Visual Analytics with @Vormetric and @Splunk for #SecurityIntelligence #DefenderOfData http://bit.ly/1BOxBCj
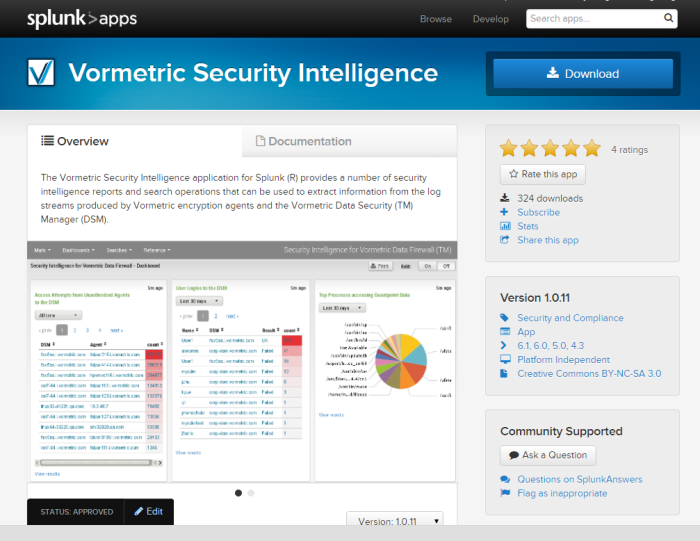
Vormetric provides a great tool for this in for form of our visual analytics implementation for Splunk, as we're highlighting here, but also makes available links for working similarly with HP ArcSight, IBM QRadar, LogRhythm. Visual analytics implementations typically provide an interactive, graphic display set designed to allow for easily identifying insights into the nature of problems or operations. It is an approach that integrates visualization, human factors and data analysis. The resulting visual representations of data analysis for applications involving large, complex data sets results in capabilities for deep pattern based monitoring and auditing. The results are capabilities to detect and discover the unexpected and to create defensible assessments with suggested actions and remediations.
What we're highlighting today - The Vormetric Security Intelligence application for Splunk® provides a number of visual security analytics and security intelligence reports. It enables search operations that can be used to extract information from the log streams produced by Vormetric Transparent Encryption agents (VTE) and the Vormetric Data Security Manager (DSM). When used with the intelligent visual analysis capabilities of Splunk, Vormetric Data Security logs provide information allowing detection of unusual or improper data access that may indicate a threat, including detailed user and process access information. This capability is available as part of the extensible Vormetric Data Security platform providing protection across heterogeneous environments – file systems, databases, big data implementations, VMs, cloud environments, and SAN/NAS devices.
What's the result of this capability? You have a very good chance of catching bad actors in action. Information about accounts and applications trying to access sensitive data without permission can quickly be highlighted for investigation. A system administrator account, trying to access a database that should be of no interest to a person with that role, may well indicated either an advanced attack that has compromised the account's credentials, or a malicious insider incident in process.
Vormetric first made available to customers our free SplunkBase application – Vormetric Data Security for Splunk in March of 2013. In the past two years, it has been updated and improved, and had additional reports added. The latest version is 1.0.11.
Vormetric Security Intelligence for Splunk enables enterprises to improve their security posture and operation intelligence by:
- Identification of anomalous process and user access patterns for investigation. Resulting in accelerated APT and insider threat detection
- Learning of unusual or improper data access, for example that an administrative account may have been compromised.
- Monitoring and auditing unauthorized protected data access attempts
- Receiving consolidated and consistent compliance and audit reporting
For our customers who also use Splunk, this tool is well worth taking a look at. It greatly extends the reach of your capabilities to detect and counter attacks on your sensitive data. For information about our additional connections available to IBM QRadar, HP ArcSight and LogRhythm, but sure and contact us for more detail.

 I-Ching Wang | Senior Director, Engineering
I-Ching Wang | Senior Director, Engineering