 The state of security and data breaches is no song and dance matter. We all know 2014 wasn’t shy of data breaches. We saw companies – once thought of as impenetrable – hacked. In this layout of the World’s Biggest Data Breaches, it’s clear the outlook is meek. While 2014 may have been a whirlwind of security vulnerabilities, just three months into 2015 we’ve already seen breaches at Uber, Anthem, the hotel chain Mandarin Oriental, Thales and others.
The state of security and data breaches is no song and dance matter. We all know 2014 wasn’t shy of data breaches. We saw companies – once thought of as impenetrable – hacked. In this layout of the World’s Biggest Data Breaches, it’s clear the outlook is meek. While 2014 may have been a whirlwind of security vulnerabilities, just three months into 2015 we’ve already seen breaches at Uber, Anthem, the hotel chain Mandarin Oriental, Thales and others.
ClickToTweet: With these 2015 Data Breaches - It doesn't look like a promising year for personal data @SocialITS #DefenderOfData http://bit.ly/1KP48Ni
Taking a closer look at the World’s Biggest Data Breaches chart, data breaches as a whole are not something new. However, the sheer quantity of data breaches provides a completely different outlook. It’s a new era and one where data breaches are becoming the norm. Here is a quick timeline (and the number of individuals effected):
- August 2005 - AOL (92 M) – A former software engineer was sentenced to a year and three months in prison for stealing 92 million screen names and e-mail addresses and selling them to spammers who sent out up to 7 billion unsolicited e-mails. The stolen list of 92 million AOL addresses included multiple addresses used by each of AOL’s estimated 30 million customers.
- January 2007 - TJ Maxx (94 M) – 6 million credit and debit card numbers were stolen. The systems that were broken into, processed and stored information related to payment cards, checks and merchandise returned without receipts. The data breach affected customers of its T.J.Maxx, Marshalls, HomeGoods and A.J. Wright stores in the U.S. and Puerto Rico.
- January 2009 - Heartland (130 M) – Cybercriminals breached Heartland’s network and recorded consumers’ credit- and debit-card data. Heartland suffered what within days would be called the largest-ever criminal breach of card data. The company went public to encourage companies to share information about attacks and band together against cybercriminals who themselves are becoming better organized.
- April 2011 - Sony PlayStation (77 M) – A massive breach in its video game online network led to the theft of names, addresses and possibly credit card data belonging to 77 million user accounts. The data breach prompted Sony to shut down the network immediately.
- March 2012 - Court Ventures (200 M) – Experian-owned Court Ventures sold information directly to a Vietnamese fraudster service. For almost ten months after Experian completed that acquisition, a previous executive at Court Ventures, Hieu Minh Ngo, continued siphoning consumer data and paying for the information via cash wire transfers from a bank in Singapore. After Ngo’s arrest, Secret Service investigators in early 2013 quietly assumed control over his identity theft service in the hopes of identifying and arresting more than 1,000 of his paying customers. Information on Americans, included social security numbers and financial details.
- July 2013 – Massive American Business Hack (160 M) – Five Russians and a Ukrainian used sophisticated hacking techniques to steal more than 160 million credit and debit card numbers, target more than 800,000 bank accounts and penetrate servers used by the Nasdaq stock exchange. The separate and devious operations spanned the globe, resulting in at least $300 million in losses to companies and individuals.
- May 2014 - eBay (145 M) – eBay asked its 145 million active customers to change their passwords as a “precautionary measure” after the company discovered it was breached. Hackers accessed other personal information about users -- including names, dates of birth, e-mail addresses, physical addresses and encrypted passwords.
- December 2013 - Target (70 M) – The breach began around Black Friday and involved the theft of information stored on the magnetic stripe on the backs of cards used at nearly all of Target's stores around the country. Following Target’s massive data breach announcement that saw 46 percent profit loss, CIO Beth Jacob, who oversaw Target’s web site and internal computer systems since 2008 resigned in March that year. Shortly thereafter, the board decided it was time for new leadership and CEO Gregg Steinhafel resigned in early May 2014.
- July 2014 - JP Morgan (76 M) – The breach was detected and stopped mid-August when a routine investigation uncovered signs that customized malware was being used to exfiltrate gigabytes’ worth of data, including some customer information, from the bank’s network. Attackers appeared to have exploited multiple zero-day vulnerabilities in their attack, and to have routed stolen data through multiple countries before finally routing much of it to Russia.
- September 2014 - Home Depot (56 M) – Home Depot led to fraudulent transactions across the United States, draining cash from customer bank accounts. Criminals used stolen card information to buy prepaid cards, electronics and even groceries. The files containing the stolen email addresses did not contain passwords, payment card information or other sensitive personal information.
- February 2015 - Anthem (80 M) – Hackers stole information on tens of millions of Anthem customers. The information stolen from the insurance giant included names, birthdays, medical IDs, social security numbers, street addresses, e-mail addresses and employment information, including income data.
 While breaches aren’t new the recent volume and frequency of data breaches is a different story. All arrows (or in this instance bubbles) point to the need for executives to rethink their security strategy.
While breaches aren’t new the recent volume and frequency of data breaches is a different story. All arrows (or in this instance bubbles) point to the need for executives to rethink their security strategy.
In December 2014 Sony also revealed it had been breached. Here're is a quick mini-timeline of the breach that effected 100 terabytes of data:
- November 21: Anonymous hackers sent emails to Sony’s CEO and other executives with warning of great damage by Sony
- November 24: Sony computers showed “hacked by GOP” message and attackers threatened to release data if demands were not met by deadline
- November 28: Sony blamed North Korea for the attack
- November 29: Sony hack could be related to the release of “The Interview”
- December 3: Second leak contained plain-text passwords stored by Sony, along with the company’s security certificates and other credential data
- December 8: Data including Brat Pitt’s phone number, publicity bibles and budget data for feature films was leaked
- December 9: Hackers warned Sony not to release “The Interview” saying “we are sending you our warning again” to “stop immediately showing the movie of terrorism”
- December 13: Sony canceled film shoots due to inability to process payments
- December 15: Hackers made a terrorist threat against theatres showing “The Interview” alongside releasing data
- December 16: Sony employees filed a class action lawsuit against the company for its failure to secure its networks
- December 17: The four largest theater chains in the US confirmed that they won’t be showing “The Interview”
- December 18: Sony postponed “The Interview” until further notice
- December 19: The FBI named North Korea as the country behind the attacks
- December 20: Sony’s hackers “troll” the FBI with sarcastic message congratulating it for choosing North Korea
- December 21: Sony released “The Interview” for free on its Crackle streaming service
What Sony, alongside other data breaches, taught us is that no longer is it just about digital identity and hackers stealing information from one individual at a time. In businesses, hackers have found the motherland and those hacks are creating physical, real world effects.
In Alan’s March blog post, he pointed out that when it comes to cybersecurity initiatives, the U.S. government has not taken a back seat. Owning to the number of high profile breaches and damaging insider attacks that occurred in the past few years, the White House has taken a stand in protecting companies and individuals from cyber attacks.
Recent efforts include Obama’s White House Summit at Stanford University and speaking on cybersecurity at the State of the Union Address. Although there is no guarantee these initiatives will lead towards diminished cyberattacks and better cooperation between the public and private sector, the federal government’s recognition that cybersecurity is a matter of grave importance is a necessary first step. We have seen the damage successful cyberattacks can have on both the government and businesses from a reputational, financial and legal standpoint.
We recently released our 2015 Insider Threat Report, and despite the current breach state, results from our 2015 Vormetric Insider Threat Report show that insider threat awareness levels have increased:
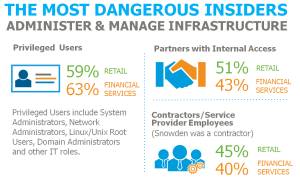
- 55% of respondents globally (59% in the US) believe privileged users pose the most threat to their organization
- Almost half (44%) of U.S. respondents had experienced a data breach or failed a compliance audit in the last year (40% of respondents Global, and 48% in ASEAN)
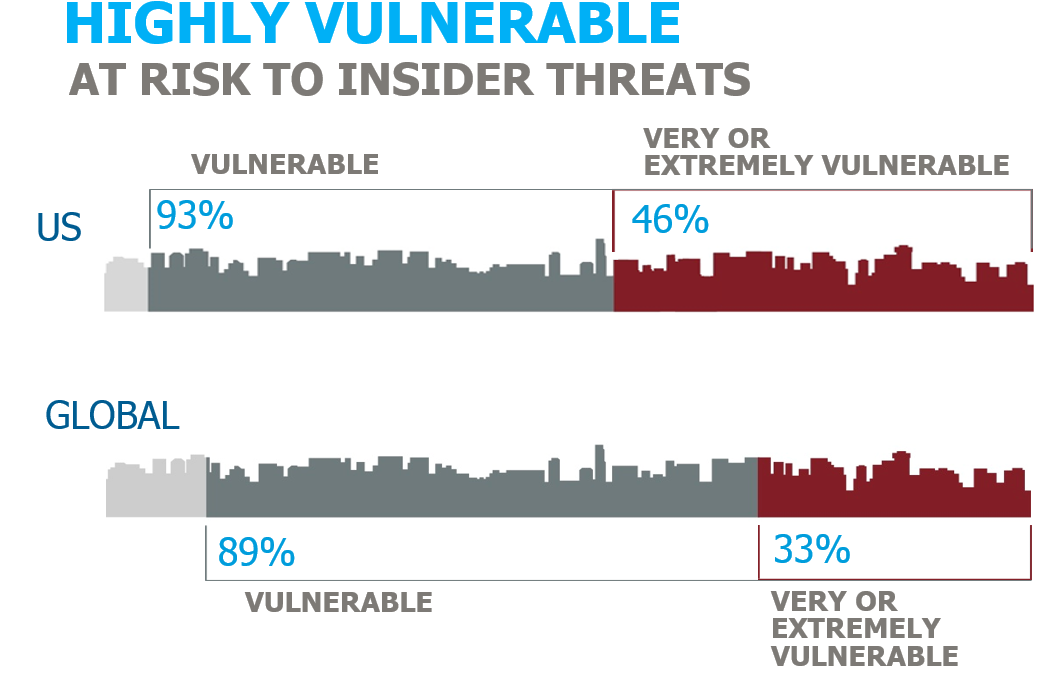
- 89% of Global respondents said they were somewhat or more vulnerable to insider threat – almost 2X the number in 2013 (In the US the number was higher – 93%
 If you take only one thing from this blog remember: keeping company data safe needs to remain the overriding factor.
If you take only one thing from this blog remember: keeping company data safe needs to remain the overriding factor.
The majority of company-sensitive data continues to be stored on-premise on corporate databases and servers. Encryption technology alongside strong access controls and key management is needed for all important data sources and includes the use of database or server, file, and data encryption, tokenization, data masking, application encryption and data on the move encryption.
What is required to keep an organization safe is a unified IT security strategy, incorporating a layered protection approach that adds a new emphasis on data protection as a key element in keeping organizations safe. This is a strategy that leaves security to the CISO and avoids IT becoming a boardroom issue.

 Tina Stewart | VP, Global Market Strategy
Tina Stewart | VP, Global Market Strategy