 Last week, we announced the Cloud and Big Data edition of our 2015 Insider Threat report. Extending earlier findings in the global report with details of what a compromise of cloud platforms and big data environments could be like, it made for some interesting reading.
Last week, we announced the Cloud and Big Data edition of our 2015 Insider Threat report. Extending earlier findings in the global report with details of what a compromise of cloud platforms and big data environments could be like, it made for some interesting reading.
ClickToTweet: UK Cloud Use - 54% keep sensitive data in the cloud http://tinyurl.com/k9hk4y7
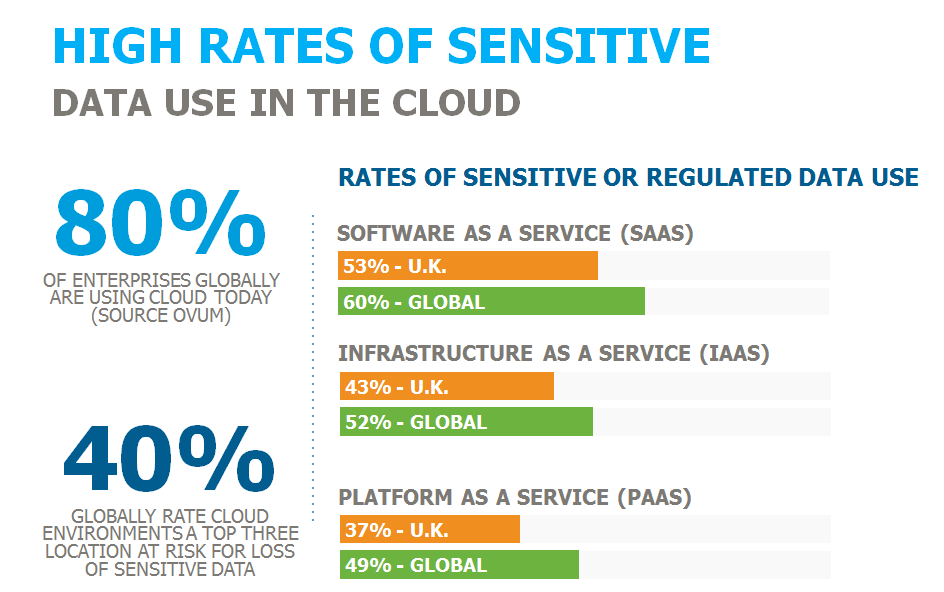
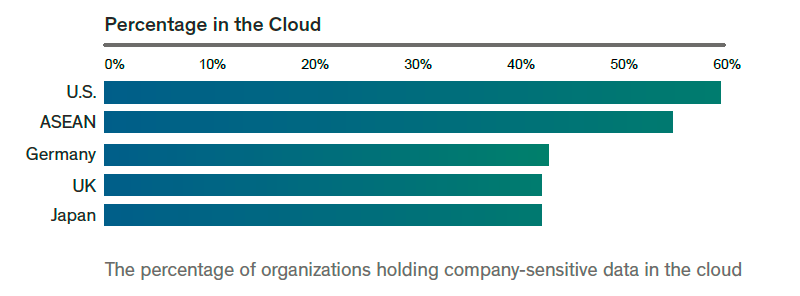
Countless studies have shown us that cloud computing has the potential to make businesses more responsive than ever – imparting the economic advantages that added speed, agility and flexibility bring with them. Indeed, the Ovum research confirmed that almost half (46 percent) of global respondents were using the cloud, in some shape or form, because of ‘market pressures’. However, security remains a genuine concern and a major stumbling block for many. The headline figure of this edition of the report is that, though 80 percent of enterprises are already using cloud environments, only 54 percent reported keeping sensitive information in the cloud. With these numbers in mind, there can be little doubt that fear and a hyper-awareness of recent high-profile data breaches are slowing implementation and adoption of these platforms.
 Interestingly, a new report issued by the European Union Agency for Network and Information Security (ENISA) confirmed that the adoption of cloud computing in the public sector alone across the European Union is being considerably held back by worries over how sensitive data can be secured. Of course, this reticence is echoed in the private sector where even the likes of Volkswagen have openly acknowledged that they will not use the cloud due to these same unresolved issues around data privacy and the associated regulatory headaches they bring.
Interestingly, a new report issued by the European Union Agency for Network and Information Security (ENISA) confirmed that the adoption of cloud computing in the public sector alone across the European Union is being considerably held back by worries over how sensitive data can be secured. Of course, this reticence is echoed in the private sector where even the likes of Volkswagen have openly acknowledged that they will not use the cloud due to these same unresolved issues around data privacy and the associated regulatory headaches they bring.
Another aspect of this report that I found interesting is that in the U.K., cloud environments (39%) are now considered to present more of a risk to enterprise organisations than databases (38%) and file servers (33%). One can assume here that the high-profile server level breaches that took place throughout 2013 and 2014 – affecting the likes of Yahoo!, Ubisoft, eBay and Paddy Power – have served to trigger a change in this area of data security.
Equally, it shows how the incorporation cloud computing technology use has entered mainstream business practices. This is perhaps unsurprising given IDC predicts that, by next year, there will be an 11 percent shift of IT budget away from traditional in-house IT delivery toward various versions of new cloud delivery models.
The time has come to act and to see data security as a business enabler. Fortunately it seems this message is starting to hit home – a promising statistic I took away from the Ovum report is that more than half of the respondents worldwide would be more willing to use cloud services if the provider offers data encryption with key access control. As a data security specialist, we understand that IT departments worldwide face a dizzying array of threats and so to protect data from prying eyes and falling into the wrong hands, choice of solution must be made strategically.
Looking to data-centric security solutions that offer policy-based separation of duties is crucial. Not only do they prevent cloud administrators, root users and other network system admins from abusing their privileged status or falling victim to APT attacks and other sophisticated malware, they also provide visibility into what is happening to sensitive information as it moves throughout the network, and across the various working or storage environments.
