 About a year and a half ago, many stood stunned as Target’s large infrastructure was infiltrated. Shortly thereafter, major retailers like Michaels, T.J. Maxx, Neiman Marcus and Home Depot were breached and many assumed that it was just a ‘retail problem.’ The current forecast is significantly different. While breach shock value has almost entirely eliminated – individuals are realizing that no industry is immune. Just recently seeing breaches around the IRS, OPM, and most ironically, The Hacking Group, we should all take some time to acknowledge that industry immunity is non-existent.
About a year and a half ago, many stood stunned as Target’s large infrastructure was infiltrated. Shortly thereafter, major retailers like Michaels, T.J. Maxx, Neiman Marcus and Home Depot were breached and many assumed that it was just a ‘retail problem.’ The current forecast is significantly different. While breach shock value has almost entirely eliminated – individuals are realizing that no industry is immune. Just recently seeing breaches around the IRS, OPM, and most ironically, The Hacking Group, we should all take some time to acknowledge that industry immunity is non-existent.
ClickToTweet: Marking the #Compliance checkbox won't prevent a #DataBreach http://ow.ly/PoF86 http://pic.twitter.com/jQ0y1RQ3GV
As you read this blog, remember one thing – Target was compliant when it was breached. Beyond obvious data loss, even marking the compliance checkbox can result in bad publicity, law suits, senior management and brand reputation … you know that scandalous picture from Cabo that you just can’t take off the Internet. While compliance is key, here are a few breaches that started with data loss but had significantly larger ramifications:
- Target – In November 2013, Target’s data was compromised including personal information, names, mailing address and phone numbers of 40 million customers who used credit and debit cards at US stores. Criminals infiltrated its system, installed malware on its point-of-sale network, and stole payment and credit card data. It was ultimately announced that 70 million customers were affected in the breach.In January 2014, Target laid off 475 employees at its headquarters in Minneapolis and worldwide and left another 700 positions unfilled. Costs associated with the data breach topped $200 million.Excessively high costs were not the only outcome to this industry changing breach. After 46 percent profit loss, CIO Beth Jacob, who oversaw Target’s website and internal computer systems resigned in March 2014. Shortly thereafter, the board decided it was time for new leadership and CEO Gregg Steinhafel resigned in early May 2014.Target ultimately agreed to pay MasterCard-issuing banks as much as $19 million to reimburse for losses related to the hack. Target also disclosed in a financial filing that it incurred $252 million of breach-related expenses.
- Sony – In November 2014, the image of a skull flashed on all employee’s computers with a threatening message warning, “this is just the beginning.” Hackers warned that if Sony didn’t obey their demands that they would release the company’s top secrets.
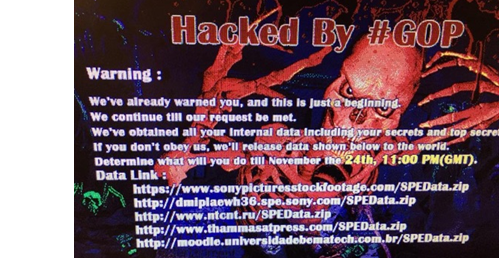 Salaries of the top 17 Sony executives were leaked. Files also contained the salaries of more than 6,000 current and former Sony employees (including celebrities).Hackers also threatened to attack movie theaters that played The Interview. Obama spoke on the matter – stressing that Sony should not comply with hacker demands (easier said than done, am I right?). In the aftermath, Sony eventually announced it would release The Interview as planned in theaters that wanted to screen it.In the end, three class-action lawsuit were filed against the studio by former employees claiming that Sony took inadequate safeguards to protect their personal data and left them in the dark. With ramifications that were so far-reaching, many are seeing this breach as a paradigm shift in the way hackers deal with data.
Salaries of the top 17 Sony executives were leaked. Files also contained the salaries of more than 6,000 current and former Sony employees (including celebrities).Hackers also threatened to attack movie theaters that played The Interview. Obama spoke on the matter – stressing that Sony should not comply with hacker demands (easier said than done, am I right?). In the aftermath, Sony eventually announced it would release The Interview as planned in theaters that wanted to screen it.In the end, three class-action lawsuit were filed against the studio by former employees claiming that Sony took inadequate safeguards to protect their personal data and left them in the dark. With ramifications that were so far-reaching, many are seeing this breach as a paradigm shift in the way hackers deal with data.
While the U.S. has been hit hard by data breaches, America is not alone. Below are a few recent breaches that have occurred outside the U.S.:
- European Central Bank: In July 2014, The European Central Bank had its website hacked, resulting in theft of personal data. Cybercriminals were able to penetrate a database storing information of individuals who registered for conferences and events.Most of the data was encrypted, but the contact information of registrants was not. Approximately 20,000 email addresses and a smaller number of phone numbers and physical addresses were lifted. The theft came to light after an anonymous email was sent to the demanding money in exchange for the data.
- Japan Airlines: In September 2014, personal information of 750,000 members of its frequent flyer club was stolen when hackers breached the airline's customer information management system by installing malware on the system. The data included names, birthdates, genders, home addresses, work addresses, job titles, phone numbers, fax numbers, email addresses, membership numbers, and enrollment dates. Installed malware on 23 company computers was later found to be sending data to a server in Hong Kong.
What’s become abundantly clear is that cyber thieves aren’t going after the small stuff. They are going after public-facing websites or hitting entire servers in search of anything they can sell.
The reality, however, is that not all cyberattacks are financially motivated. Foreign nations frequently shift their focus towards embassies and government agencies to gain access to critical intelligence. Remember how we pointed the finger at Korea following Sony’s breach, China was looked to when The Office of Personnel Management was hacked and Russia was blamed for the IRS breach? Nation-state espionage is not a new phenomenon, but in the last decade, or even few years, new technologies have exposed us to a whole new realm of spying.
Last year in a blog titled, ‘With Great Data Comes Great Legal Consequences – Preparing for the Next Encryption Battle,’ I discussed how we hit a global awakening which prompted law makers and regulators to become increasingly engaged in implementing legal frameworks while defining new obligations for data security. As far as data security law is concerned, the legal obligation is to act reasonably.
While government regulation is a fact of life, in the security space, it’s an entirely different ballgame. Regulators around the world are enhancing existing data security compliance requirements, implementing new legal frameworks and defining new data security regulations to respond to increasing internal and external hazards. But as recent breaches have proven, it remains to be seen how effective guidelines are protecting agencies, citizens and their data at corporations.
Over the past decade, as states have developed expertise on security, they have also updated their laws to address changing technology. According to Slate, more than 30 states require companies to dispose of sensitive data securely, and a number of states are now requiring companies that handle sensitive personal information to develop reasonable data security practices to protect it. Only Alabama, South Dakota and New Mexico do not have laws requiring data breach notification. But this still leaves a problem even the president acknowledges – this inconsistency between states is creating a major discrepancy when it comes to how data breaches are handled. Creating national breach notification laws ultimately has the ability to remove current confusion and inertia that surrounds differing state laws.
As the world progresses from a mere “information age” into an age of “big data,” it’s simple – the volume, granularity and sensitivity of individual data is growing exponentially. With this growth comes severe risks and consequences of losing that data.
In the wake of recent attacks like those at Target and Sony, concerns about data security awareness have drawn significant attention. But we’re not quite there yet. With determined attackers able to breach organizations’ perimeter, compliance can act as a baseline but does not represent security. Clearly, the use of encryption technologies and access control, alongside compliance form part of the answer. Mandatory post-breach transparency, tougher penalties and sanctions, and an increase in regulatory guidance will also provide organizations the ability to reduce risk while preventing future breaches.
Personal records are under attack, and existing state and local legislation is not enough to protect people being affected every day. Reflecting on the trends that developments in data security law have shown to date, we will undoubtedly see the law becoming even more prescriptive over time. Lawsuits against Sony and others that have been breached highlight the problem and are leading to new areas of concern that make protecting data a C-level and board concern.

 Tina Stewart | VP, Global Market Strategy
Tina Stewart | VP, Global Market Strategy
