 We are able to access our data from nearly anywhere in the world, and this an incredible business resource, but this has increased the risk of data being compromised by malicious parties. Now, with data held in the cloud, in data warehouses or being exchanged over multiple enterprise systems, the chance of sensitive information being stolen or jeopardised has rocketed. Unfortunately, data has no natural defences – and while this wasn’t a cause for serious concern when strong perimeter barriers were enough to defend it, this is simply no longer the case. The result - IT needs to catch up to changes in how the world of cybersecurity has changed, or leave their organisation open to serious cyber threats.
We are able to access our data from nearly anywhere in the world, and this an incredible business resource, but this has increased the risk of data being compromised by malicious parties. Now, with data held in the cloud, in data warehouses or being exchanged over multiple enterprise systems, the chance of sensitive information being stolen or jeopardised has rocketed. Unfortunately, data has no natural defences – and while this wasn’t a cause for serious concern when strong perimeter barriers were enough to defend it, this is simply no longer the case. The result - IT needs to catch up to changes in how the world of cybersecurity has changed, or leave their organisation open to serious cyber threats.
ClickToTweet: A Quick Guide to the Enterprise Encryption Ecosystem http://bit.ly/1FkiC0c pic.twitter.com/xfYjkuiPMf
Data encryption has long been part of the information security arsenal, protecting data both in storage environments and while it’s on the move. However, despite its long history and deep value, up until recently, adoption inside data centres and applications has been worryingly low. This is perhaps down to a lack of understanding, so let’s review the basic concepts underlying encryption systems; these will guide decisions on which encryption options to use.
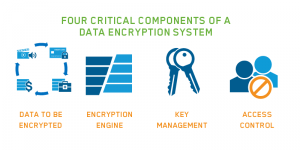
Components of a Data Encryption System
When encrypting data in applications and data centres, knowing how and where to place this technology is incredibly important. Understanding our data exposure points is key, as is understanding where the encryption components reside, and how they tie together. These all determine how much actual security we end up with. Three major components define the overall structure of an encryption system and then a forth component - access control - is needed to make the solution effective.
- Data: The object or objects to encrypt
- Encryption Engine: This component handles actual encryption (and decryption) operations
- Key Manager: This handles keys and passes them to the encryption engine
- Access Control: Policy-based access control tied to application and/or directory services roles and groups limits access from within applications and at the OS level
In a basic encryption system all three encryption components are likely located on the same system. As an example, take personal full disk encryption - ‘FDE’ - the built-in tools you might use on your home Windows PC or Mac. With FDE, the encryption key, data, and engine are all stored and used on the same hardware. Lose that hardware and you lose the key and data. But FDE doesn't have access control capabilities available - if you have access to the system, you have access to the data. For data centres, the encryption components are likely to reside on different systems, but should have a common management framework or system for key management and access policy control.
Building an Encryption System
All data encryption systems are defined by where these pieces are located – which, even assuming everything works perfectly– control how well the data can be protected. At a high level they are: in the application where you collect the data; in the database that holds the data; in the files where data is stored and on the storage volume (typically a hard drive, tape, or virtual storage) where the files reside. If you want to get into this in more detail, you can read this report or get in touch with one of the team.
All data flows through that stack – sometimes skipping applications and databases for unstructured data. So, simply, by including encryption and access controls at the top, then the data is protected all the way down. Understanding your requirements almost always naturally leads you to select a particular layer, which then determines where to place the components.
Okay, I get it, now – but is it for me?
Most likely! If you think the operational impact of data security can be too much of a burden for your business, you need the kind of security that fulfills compliance requirements without a struggle, security that’s virtually transparent to users and has little or no drag on your daily business operations. A single platform with multiple encryption technologies, access control capabilities and centralized policy and and management capabilities relieves many of these problems. Hardware based encryption capabilities (using the accelerated encryption speeds available by using encryption capabilities built into modern CPUs and other devices) relieve the loading on applications, so that implementations have very minimal impacts on performance and throughput.
Encryption, in whatever guise, like most security, is adopted in response to business need. It may be a need to keep corporate data secret, protect customer privacy, ensure data integrity, or satisfy a compliance mandate that requires data protection – but there is always a motivating factor driving companies to encrypt.
When push comes to shove, organisations most often invest in encryption solutions because of:
- A compliance requirement driven by an industry standard or regulation (PCI DSS, for instance)
- Government laws and regulations (financial account protection, data residency laws, customer information protection)
- A contractual requirement from a customer or partner
- A mandate to protect information to prevent a data breach of private customer information
Ultimately, though, the principal use cases have changed over the years, the encryption and access control solutions that are required are driven by achieving an understanding of these critical factors:
- Know why you are encrypting
- Know where you can potentially encrypt
- Know how to position the encryption components within the framework of a well rounded, layered approach to data security specifically and IT security in general
- Don't forget the access control - For both OS and application level
Understanding these critical components will help you to achieve your security objectives.

 Louise Bulman | AVP of EMEA
Louise Bulman | AVP of EMEA