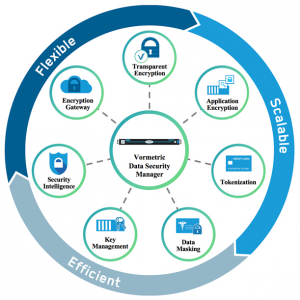
 Earlier this week, we announced a major expansion of the Vormetric Data Security Platform. Our latest updates expand protections for sensitive data within datacenter, cloud, Big Data and application environments. More specifically, they offer encryption and access control options for Docker, Hadoop, NoSQL and SQL as well as enhanced automation capabilities to help organizations minimize data breaches and meet compliance and regulatory requirements.
Earlier this week, we announced a major expansion of the Vormetric Data Security Platform. Our latest updates expand protections for sensitive data within datacenter, cloud, Big Data and application environments. More specifically, they offer encryption and access control options for Docker, Hadoop, NoSQL and SQL as well as enhanced automation capabilities to help organizations minimize data breaches and meet compliance and regulatory requirements.
ClickToTweet: Need #DataSecurity for #Docker? #NOSQL? @Vormetric has it http://bit.ly/1MsJTRp pic.twitter.com/MBEJOSrEEq
Pretty useful stuff, especially in our daunting cybersecurity environment. Rather than provide a run-down feature-by-feature, I’ve expand on how our latest launch further supports a couple of Vormetric’s core values:
Innovation with new technology
This launch underscores our commitment to providing security innovation for disruptive, high-growth technologies. In this case, those technologies are Docker, Hadoop and NoSQL.
For example, environments like Hadoop hold sophisticated and sensitive data that is often used for analytics purposes. Additionally, the results stemming from those analytics may also prove quite sensitive, especially if they involve personal information (such as one’s healthcare history).
Rather than swim against the tide, we’ve acknowledged the power and popularity of these new technologies – and the fact that they’ve introduced new security complexities. In turn, we’ve evolved our Data Security Platform to reflect today’s reality.
Ongoing platform improvements
Automation, orchestration and enterprise-scale operationalization are absolutely key for enterprise-class organizations. Speaking in layman’s terms, essentially we want our (quite big) customers to stay secure, but help them do so in a way that is easy and intuitive for them.
Along with helping our customers to deploy more easily, the latest updates help them protect data more completely, in more environments, and with minimal business impact. Our goal is never to disrupt operations or force our customers to implement costly new security infrastructure sets. Our goal is to empower them to drive new levels of scale, efficiency, and productivity – all the while protecting critical data.
Conclusion
These benefits, coupled with our support of the technologies mentioned above, put us in a position to accommodate for even larger and more sophisticated environments. We’ve been playing in the big leagues for a while now, so this isn’t an entirely unique position we find ourselves in – but we’re excited nonetheless.
We’re not stopping here, either. You can expect even bigger product updates in 2016. Stay tuned!
