 In the cybersecurity industry, data breaches and digital based offenses are considered especially damaging. In San Jose, the dedicated encryption experts who investigate and stop these vicious hacks are members of an elite cybersecurity company known as Vormetric. This is their report.
In the cybersecurity industry, data breaches and digital based offenses are considered especially damaging. In San Jose, the dedicated encryption experts who investigate and stop these vicious hacks are members of an elite cybersecurity company known as Vormetric. This is their report.
--
It used to be a simpler time, when you could log in to the Internet without thoughts of what happened to your data – but now the threat landscape has increased exponentially. And as we issue the fourth edition of our report, we’d like to take a few moments to look back at a few recent data breaches.
ClickToTweet: Security and Order for Data: #2016DataThreat Report @socialtis http://bit.ly/1P8CrzB pic.twitter.com/ehtrmJeMdg
Breached in December, Hello Kitty (Sanrio) and VTech indicated that hackers can easily access any and all user data they can lay their hands on. There was a time where payment card data seemed to be all that mattered to cybercriminals, but those days are over. In both these recent breaches, the data stolen did not include financial information like credit card details, rather it was personal details, including email addresses, passwords, names, home addresses, genders and birth dates.
Also check out my recent blog post where I laid out the 12 major breaches of 2015, including The Hacking Team which leaked 400 GB worth of emails and that famous time criminals hacked into the IRS website and gained access to approximately 100,000 tax accounts.
Those are just the larger attacks. Since the publication of our last report, we have been exposed to a seemingly endless string of data breaches that have awaken enterprises and consumers alike when it comes to protecting data. It’s no longer just an IT problem and the mainstream public is now on board. As we have been painfully reminded, it’s no longer just insider threats, but nation-state attacks, hacktivists and cyberterrorists that use stolen credentials to access all types of data, whether that be personal health information, intellectual property, or personal identifiable information.
As we continue relationships with third-parties to handle our core-business, we have collectively expanded data access ten-fold. As a result we changed up our report this year. We still believe in the value of strategies that keep insider threats out, but we also have added external actors as that line between insiders and outsiders gets finer and finer.
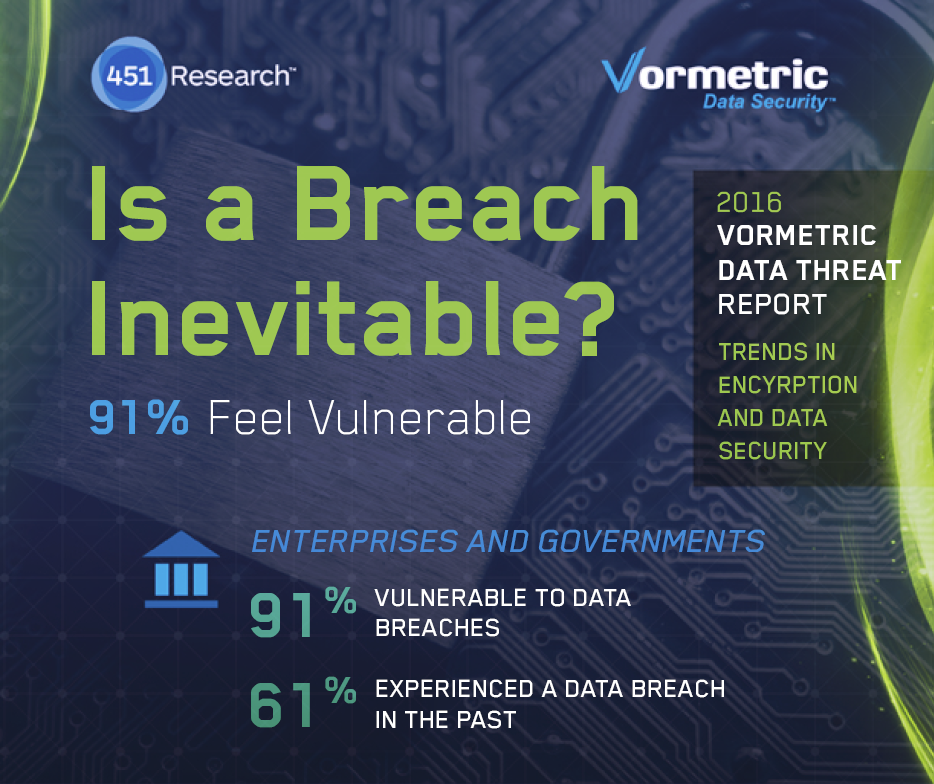
We’ve released the 2016 Vormetric Data Threat Report, alongside 451 Research – with polling and results from 451 and written by leading security analyst Garrett Bekker. Here are a few encouraging and not-so encouraging results:
- 61% of respondents indicated that their organization had a data breach in the past year, a single question this year
- 58% said their spending to protect against data threats would be either ‘somewhat higher’ (46%) or ‘much higher’ (12%) up from 56% last year
- More respondents (91%) were feeling vulnerable to data threats up from last year (87%) and one-third were feeling either ‘very vulnerable’ or ‘extremely vulnerable’
Does data lie? Thought we exhausted that old compliance argument? Organizations are still equating compliance with security in the belief that meeting compliance requirements will be enough, even as data breaches rise in organizations certified as compliant. Investments in IT security controls were also shown to be misplaced, as most are heavily focused on perimeter defenses that consistently fail to halt cyberattacks. Here are some of the results on compliance:
- Rates of data breaches are up, with 61% experiencing a breach in the past (22% within the last year, and 39% in a previous year)
- 64% believe compliance is effective at preventing data breaches, up from 58% last year
- At 46% overall, compliance was also the top selection for setting IT security spending priorities. Industries particularly focused on compliance include healthcare (61%) and financial services (56%) organizations
What do we think about compliance? In a Federal News Radio article, When cyber compliance is not enough my colleague Sol Cates discussed how compliance remains a baseline standard for protecting information and should never be confused with security. As cybersecurity risks increasingly threaten both corporate and public well-being, lawmakers and regulators around the world are enhancing existing data security compliance requirements, implementing new legal frameworks and defining new data security regulations to respond to increasing internal and external hazards. But it remains to be seen how effective guidelines are protecting agencies and citizens.
For additional insight on compliance, check out a few of our blog posts:
- Compliance: Fighting Today’s Battles by Yesterday’s Rules?: Alan Kessler discusses how lawmakers and regulators around the world are enhancing existing data security compliance requirements, implementing new legal frameworks and defining new data security regulations to respond to increasing internal and external hazards. His assessment: compliance is only somewhat helpful in addressing data security concerns. Cyberattacks change daily and hourly, but compliance regimes are updated only over many months and years. This leaves compliance mandates requiring organizations to use protection methods that may already have been eclipsed by the attackers.
- The Data Breach Forecast Shows Signs of Failure in Compliance: I discuss how Target was compliant when it was breached. Beyond obvious data loss, marking the compliance checkbox resulted in bad publicity, law suits, senior management and brand reputation.
It’s been a challenging year with eye-opening breaches grabbing headlines and demonstrating how easily data can be attained. Clearly there is still a disconnect between what we are spending our security budget on and what’s needed to ensure our data remains secure.
In the wake of recent attacks, concerns about data security awareness have drawn significant attention. But we’re not quite there yet. Personal records are under attack, and existing state and local legislation is not enough to protect people being affected every day. With determined attackers able to breach organizations’ perimeter, compliance can act as a baseline but does not represent security. Clearly, the use of encryption technologies and access control, alongside compliance form part of the answer. Mandatory post-breach transparency, tougher penalties and sanctions, and an increase in regulatory guidance will also provide organizations the ability to reduce risk while preventing future breaches.
While the report didn’t indicate that results have gotten significantly worse the problem is that they have also not gotten significantly better. In some cases data theft exposure remains alarmingly high. If you take anything from our report or this blog, remember that clearly our old ways of securing is no longer working. The best thing security executives can do is take the time to understand data protection and do their due diligence in researching and understanding solutions that best fit their needs. It’s my hope that we continue to focus on providing improved guidance and tools to protect U.S. data and infrastructure. For now, we’re heading in the right direction so that ultimately companies can be both compliant and safe.
