If you are already developing on Docker, you already know why interest is so high. The combination of faster application delivery and evolution that it makes possible, easily scalable microservices, reusable standard images, and the possibility of reducing system licensing and management costs is nearly irresistible if you’ve adopted a DevOps strategy. And a compelling reason to adopt one if you are not.
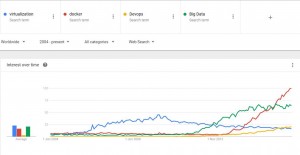
For a look at just how hot Docker is, take a look at the Google trends search I captured in November comparing searches on Docker, Virtualization, DevOps and Big Data since the introduction of Docker in March of 2013. It’s a telling story, with Docker searches far exceeding even combined searches around Virtualization and DevOps from late 2014 on.
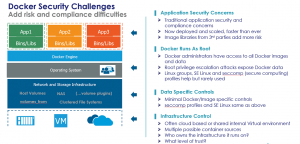
But every new technology platform comes with new risks and potential exposures and Docker is no exception to the rule. Let’s break down the major exposure areas related to data and take a look at each.
First off are application security concerns
For the most part, the concerns around application security for data are the same ones that you’d encounter with other deployment methods, but with some new twists. The first of those – the potential speed and scale of deployments make possible can amplify any traditional application security errors as development, deployment and implementation happen much faster, and can scale at much greater speed. The second twist is brought on by the use of third party Docker images. The risk in using these third party images from a library is that you don’t know exactly how they were architected and implemented. If there is a vulnerability introduced intentionally or otherwise, even a fairly intense review may not find the single line of backdoor code that could be embedded there.
Next – Docker runs as root
The Docker process on the host runs with root privileges. Read up on the documentation and you’ll find it’s a necessary evil to be able to do task such as add and remove volumes and file systems from Docker. But as a result Docker administrators have access to all Docker images and linked data sets. A result that goes with this is that a root privilege escalation attack on the host has the capability to expose any sensitive data stored in Docker environments. Along with that, compromise of Docker Administrator accounts create many of the same risks.
There are things you can do to ameliorate this without third party security controls – but they don’t seem widely used. Linux groups, SE Linux as the deployment platform and seccomp profiles can be of help, but seem rarely used at this point.
Data specific controls are few
Again, seccomp profiles and SE Linux can help here, but are often seen as difficult to implement and manage to. For the most part Docker image and data specific controls are minimal.
Last – challenges based on the deployment environment infrastructure
Often Docker is implemented in the cloud or in a shared virtualization infrastructure. With Docker hosts in these environments potentially hosting images from multiple customers or sources, this brings in one level of potential exposure. And the fact that you may not own or control the underlying hardware and software environment brings in questions about trust, legal access by third parties and other traditional cloud security problems.
To keep exposures to a minimum, some enterprises are actually using Docker clusters with only a single Docker image per VM, and within their own internal or hosted virtual environments. This has got to make it hard to realize the benefits that come with Docker.
What’s the best way to solve the problem?
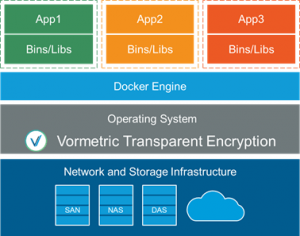
Let’s switch now to talking about the problem. Just released by Thales is Vormetric Transparent Encryption Docker Extension, which is designed to address many of these problems with a single solution.
Before we introduced the Docker Extension, we already had the capability with our standard Vormetric Transparent Encryption product to protect and control access to Docker container images and instances by policy. This includes:
- Encrypting containers
- Limit container access and use by policy to Docker (even limiting root and Docker administrator access)
- Limit use of containers to only authorized environments
- Limit access to data resources used by containers to Docker only (and even only a specific, signed Docker process if necessary)
And we were able to do this with no impact on the Docker environment (just install the agent on the Docker host, configure and deploy data security policies and go), no changes to Docker containers, and even with the capability to report unauthorized access attempts to protected data. That’s a pretty good story all by itself.
But now, we’ve added the capability to do much more. The Docker Extension directly enhances our existing controls so that they reach data inside of Docker containers, users and roles within Docker on a container by container basis, and even underlying data sets that existing on underlying SAN, NFS and other storage infrastructure accessed by applications within the containers.
Not only that, but it’s just as non-intrusive to Docker as Vormetric Transparent Encryption.
- Just install the agent on the Docker host
- Configure policies and manage from our secure Data Security Manager environment
- And no Docker container or application changes are required
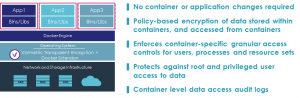
This gives you:
- Policy-based encryption of data stored within containers, and accessed from containers
- Container-specific granular access controls for users, processes and resource sets
- Protection against root and privileged user access to data inside and outside the container
- Container level data access audit logs
It’s simple, and extremely powerful.
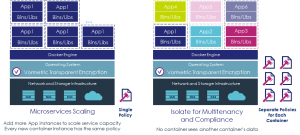
Last, the solution is great as supporting the most common deployment models for Docker environments – scalable microservices shared infrastructure sets. For the first, policies can be locked to images used for microservice deployment. In this scenario, every deployment of the image gets access to the same resources and infrastructure, making it easy and safe to scale deployments when needed. The other scenario for shared infrastructure allows for easy isolation of resources to meet multi-tenancy needs and compliance requirements.
Be sure and contact us for your Docker data security requirements – we’ll take you from Zero to Hero in no time flat.