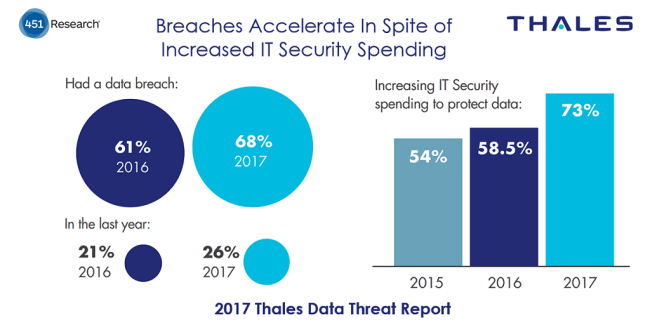
Just released today, is the Global Edition of the 2017 Thales Data Threat Report - Written by 451 Research's Principal Analyst for Information Security, Garrett Bekker. Today, I'll focus on just one of the stories found in the data set - the disconnect between enterprise's increasing investments in IT security tools, and the fact that last year was a record year for data breaches .... Again.
Click to Tweet: The Big Disconnect: Why is the #databreach rate up AND IT Security Spend? #2017DataThreat bit.ly/2jo8j9O pic.twitter.com/LR9UksgQJJ
There is strong evidence in the data for three key points that can help to explain why this disconnect is happening.
The wrong defenses: Increases in spending are concentrated in defenses that are no longer as effective as they once were at keeping the barbarians outside the gate - a new approach is needed.
An over reliance on compliance: Relying on compliance requirements to provide everything that's needed to safeguard organizations from data breaches.
Implementing new, advanced technologies without the tools to protect data: Organizations are increasingly implementing Cloud, Big Data, IoT, Containers and other advanced technologies without putting in place the IT security controls needed to protect data.
In this blog, we'll walk through the data and the reasons behind the numbers, and then take a look at what Garrett suggests are the right approaches to reduce your exposure, and get the most out of your IT security dollar.
Problem number 1 - The wrong defenses
The 1100+ IT Security pros at large enterprises that we surveyed worldwide consistently believe that they network and end point defenses are very or extremely effective at deterring data breaches. And there is simply no disputing, that these defenses are required. The problem is that these defenses are now more porous than ever before due to the sophistication level of today's cyber attacks.
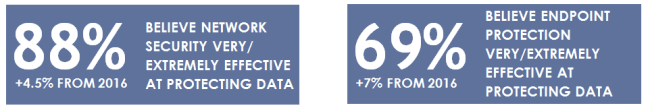
With spear phishing attacks regularly successful, clicks to contaminated sites are inevitable when a determined adversary wants in. Zero-day malware undetectable by current anti-virus is readily available on black sites (for a price), allowing those clicks to result in compromised systems that are truly hard to identify. And then there are tried and true methods of looking for net-facing systems that are miss-configured or behind in their security updates and profiles.
But organization's are having trouble internalizing that things have changed. For people who've worked for years to safeguard their organizations with great firewalls, network security tools and end point protections it can be a hard shift to make. Here's what Garrett had to say on this in the report:
"…organizations keep spending on the same solutions that worked for them in the past but aren’t necessarily the most effective at stopping modern breaches”
"… spending on securing internal networks from external threats is less and less effective – and relevant – as both the data and the people accessing it are increasingly external.”
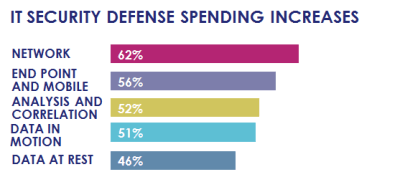
It really shows up in the numbers for planned investments too - Data-at-rest security tools, consistently rated as the best way to protect data once attackers are inside the walls consistently get the lowest levels of IT security defense spending increases (44% this year) while network (62% increase in spending this year) and endpoint (56% this year) get the most emphasis in the budget.
Problem number 2 - An over-reliance on compliance
I can't think of a better way to put it, so let's quote Garrett from the the report again.
“Compliance is a minimum table stake for regulated enterprises ... But being compliant does not mean you won’t be breached”
When we looked at what organizations are spending those increased IT Security dollars on two things came through clearly - Lots of IT security pros believe that compliance is very or extremely effective at preventing data breaches (59%) and their spending is geared to match. It's hard to fault anyone for spending on compliance given that many heavily regulated enterprises must meet the regulations or get out of the business. It's easy to sell to management too - spend the money or the consequences can be very high.
The problem is that compliance requirements are now a minimum table stake given the nature of attacks, but evolve slowly compared to threats, and are typically designed to safeguard only specific pieces of information covered by the regulation or compliance regime. And the evidence is there that this approach just isn't working too - In spite of years of prioritizing compliance first, and investing to meet compliance requirements, the rate of data breaches keeps rising. Time after time, enterprises that were compliant have been breached.

Problem number 3 - Implementing new, advanced technologies without the tools to protect data
All right, true confessions time - I've brought at least six 1.0 products to market as a product manager for large organizations and startups, so I can directly speak to the temptations faced when you REALLY want to get to market fast. It's extremely tempting to leave out the security, and just get the product or service done. I've had to fight that temptation personally. What the data shows, is the enterprises still believe they have to make the same tradeoff - and are often shorting data security investments when they use new technologies. Here's what Garrett had to say:
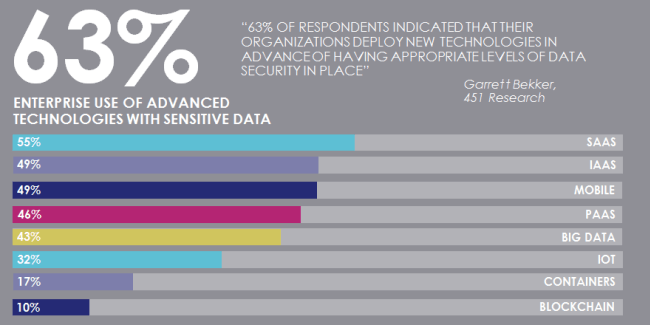
"63% of the IT security pros we surveyed say that their organizations are deploying new technologies in advance of having appropriate levels of data security in place"
That's almost two out of three organizations.
And these organizations are definitely using these advanced technologies with sensitive data - SaaS leads the pack at 55% using sensitive data there, but IaaS, Mobile, PaaS and Big Data aren't far behind.
So what's the solution?
Read the report for more detail, but here's a great summary of where to get started - Again, from Garrett Bekker with 451 Research:
Re-prioritize your IT security tool set
Cloud and SaaS break legacy IT Security models – Data security with encryption and access controls across environments is required. Service-based solutions and platforms that include automation are preferred for reduced costs and simplicity.
Discover and classify
Get a better handle on the location of sensitive data, particularly for Cloud, Big Data, Containers and IoT
Don’t just check off the compliance box
Global and industry regulations can be demanding, but firms should consider moving beyond compliance to greater use of encryption and BYOK, especially for cloud and other advanced technology environments.
Encryption and access control
Encryption needs to move beyond laptops and desktops for stronger data security
Data center: File and application level encryption and access controls
Cloud: Encrypt and manage keys locally, BYOK enables safe SaaS, PaaS and IaaS
Big Data: Encryption and access control within the environment
Containers: Encrypt and control access to data both within containers and underlying data storage locations
IoT: Use secure device ID and authentication, as well as encryption of data at rest on devices, back end systems and in transit to limit data threats
Want a look at the full report? - Visit us at http://dtr.thalesesecurity.com and get your own copy.
