 Releasing today is our 2017 Thales Data Threat Report - Advanced Technology Edition. In this edition of the report, we extend the findings from our "Global" edition with the details of how enterprises are adopting and using Cloud, Big Data, IoT and Containers (like Docker) with an emphasis on their use of sensitive data within these environments.
Releasing today is our 2017 Thales Data Threat Report - Advanced Technology Edition. In this edition of the report, we extend the findings from our "Global" edition with the details of how enterprises are adopting and using Cloud, Big Data, IoT and Containers (like Docker) with an emphasis on their use of sensitive data within these environments.
Click to Tweet: 93% using #Cloud#IoT#BigData #Containers without Data Security #2017DataThreat bit.ly/2mCQgMY pic.twitter.com/5xueeNA2jr
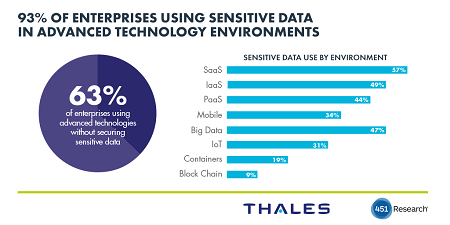
The top finding from the report? The way that many enterprises are moving forward with their implementations is putting our sensitive data at risk. There is tremendous business pressure to enable business and government with digital transformation that both allows new opportunities and reduces costs. Enterprises are adopting these environments wholesale to help transform their businesses - 93% are using these technologies this year with sensitive data.
The problem? They are moving forward without the data security controls required to help make that sensitive data safe – according to 63% of the IT security pros that we polled. It's common in new technology implementations to move ahead as quickly as possible to get to market, and so many organization seem to be moving ahead with usage, and worrying about the security if their data later. However, it's also much easier to secure those environments if data security is a required element from the start - rather than added later as an afterthought.
IoT
IoT is the poster child for this problem - with hardware manufacturers often implementing poor or minimal security, and never updating device firmware for more recently found vulnerabilities. People seem to buy the devices anyway based on cost and functionality - and worry about the possible problems later. Early problems came up years ago with routers and switches as well as HP printers being used as landing sites for intrusions into organizations networks, and is illustrated with more recent DDOS attacks run from internet connected video cameras, and even the revelations from Wikileaks that the CIA can listen to you through your Samsung TV. Even children's internet connected toys are part of the problem.
Still there are things that can be done to help with IoT even given the reluctance of device manufacturers to support security patches and updates. Most based on using cryptographic technologies:
- Give each device a secure, unique identity with a "digital birth certificate" that uniquely identifies the device. This can then be used as a baseline for secure communications and code. (identities are created using encryption technologies)
- Require only properly signed code to run on the devices (another encryption technology) - this eliminates the problem of attackers installing and running code that isn't authorized once they've found a vulnerability that allows them to gain access to the device
- Always use secure, encrypted communications to back end systems and infrastructure - with identity secured on both sides. Public key/private key encryption even as simple as https communications links help make this possible.
- Secure the volume of data on the back end using encryption and access control technologies - Allow only authorized users and processes access to data, and collect information about unauthorized access attempts and the patterns of use of allowed users to identify potential compromises before they reach the epidemic stage.
What did the study find?
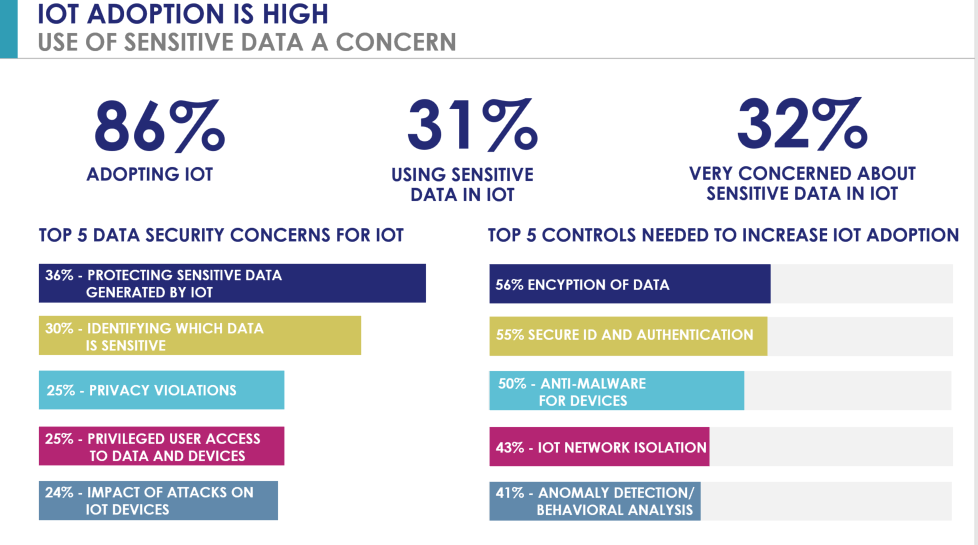
- We found that 86% of enterprises are in some stage of adopting IoT.
- The top concern of the IT security pros in their organizations?
- Protecting the sensitive data generated buy these devices (36%)
- Identifying which data is sensitive (30%)
- And privacy violations (25%).
- The top security controls needed to increase use? Not too suprisingly:
- Encryption of data (56%)
- Secure ID and Authentication (55%)
Cloud
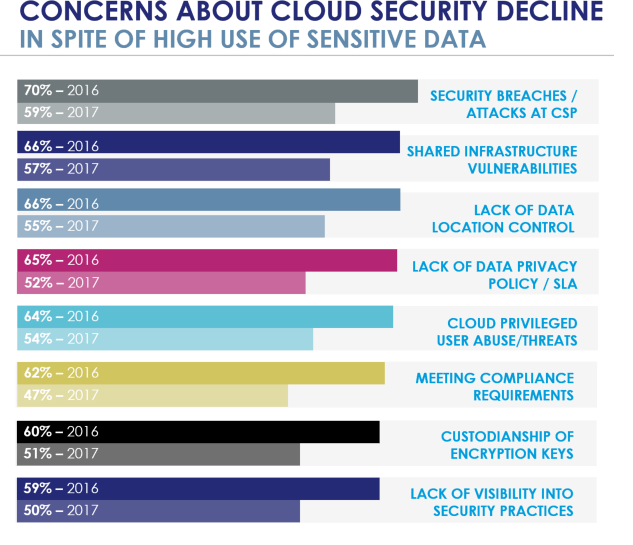
We found this year that concerns about using cloud environments are still quite high, but have dropped somewhat from a year ago - typically in the range of 8-12% from last year. Perhaps this is because we have yet to have the big cloud provider breach for a corporate oriented site (I'm not counting the Yahoo breach as that seems more consumer oriented). Most reported problems for cloud environments have stemmed from a compromised credential or account at the enterprise level, not the cloud provider. In addition, there is the fact that a large cloud provider typically has a much larger and deeper pool of IT security talent than all but the largest enterprises can field to protect their organizations.
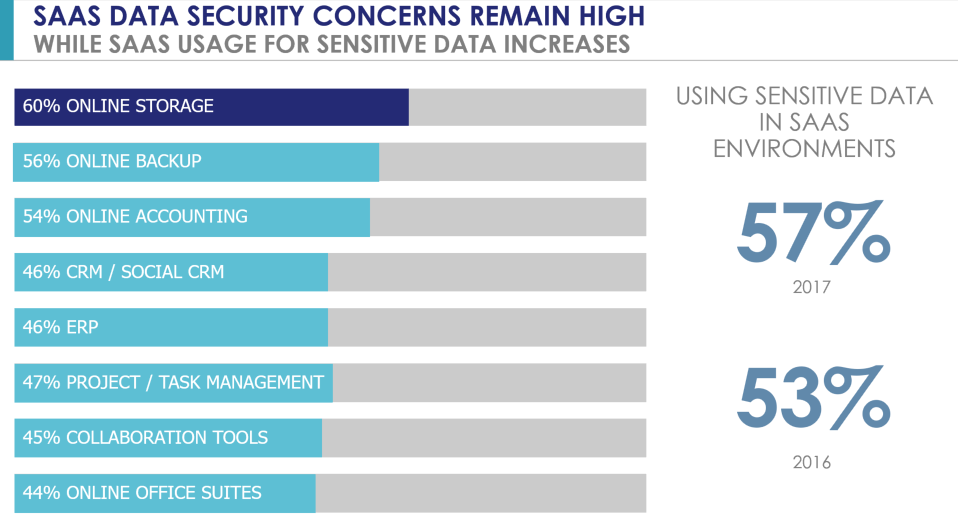
Nevertheless, use of sensitive data in these environments is up - with SaaS as an example with 57% using sensitive data within these environments versus 53% elsewhere.
What about Big Data?
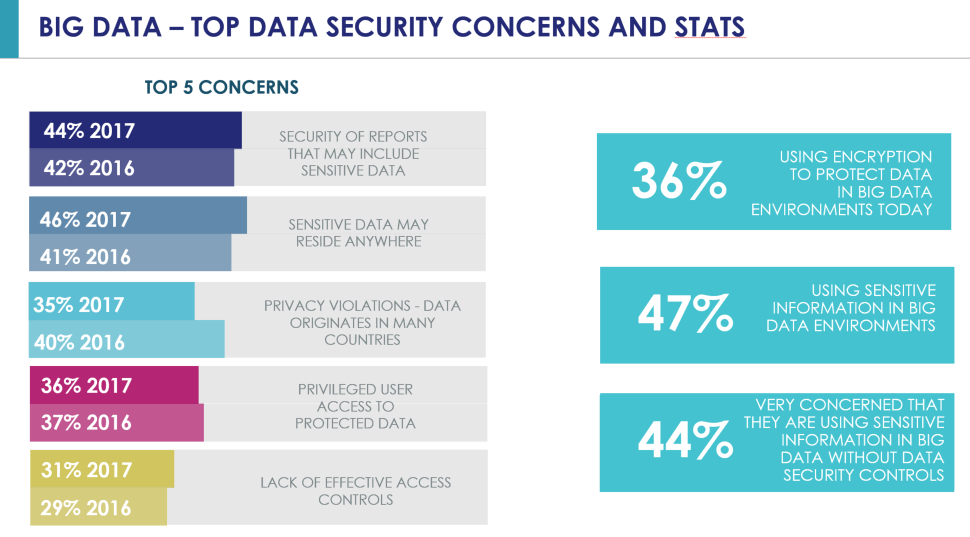
The big surprise in Big Data was the level of usage with sensitive information – it’s rapidly closing on cloud environments at 47% of our total sample. And it would seem that most of those (at 44% of the total sample) are also very concerned about this sensitive data usage.
Containers (like Docker) usage high
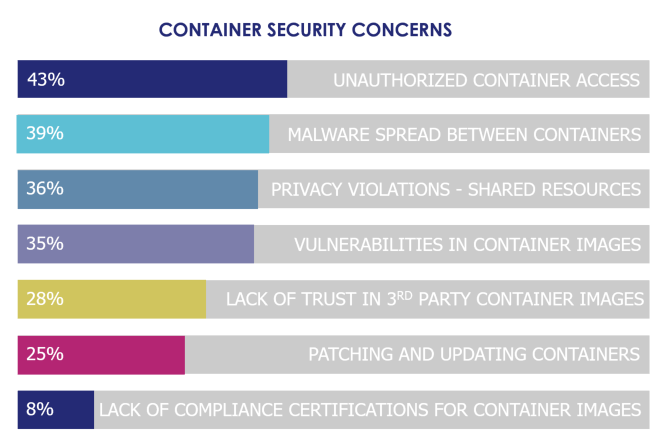
We were also surprised that usage of containers was so high - just four years after the introduction of Docker almost 40% were in production and 87% have plans for using containers this year. But security concerns are also high, with security the top barrier to introduction at 47% and concerns unique to these environments. Top of the list? Unauthorized container access at 42% of respondents.
The Rise of Encryption
When we looked at what enterprises wanted most in order to drive their digital transformation through expanding their usage of these advanced technology platforms, repeatedly the answer was "encryption". Here's how that breaks out:
- Cloud – 60% would increase use if CSPs offer data encryption in the cloud with enterprise key control
- Big Data – Encryption with access controls offset the top three data security concerns – sensitive data everywhere (46%), security of reports (44%), privileged user access (36%)
- IoT – Data Encryption (56%) and Security Digital Identities (or digital birth certificates) using encryption technologies (55%) are critical controls needed to enable further safe deployments
- Containers – Encryption (54%) is the top security control needed to increase adoption
Overwhelmingly, encryption technologies are what enterprises need to expand their use of these environments - and we'd love to help them with exactly the solutions they need here at Thales.
