Cyberattacks continue to grow more sophisticated and persistent. To combat threats and keep data safe, IT teams must employ robust encryption, key management, and access controls. This is especially true for information held in storage environments, which can contain an organization’s most vital assets.
To secure storage, many organizations have been leveraging native encryption offerings from their storage vendors. However, the growing trend with all-flash storage array deployments in enterprises poses challenges when encrypted data from host servers are stored in these arrays.

Security Versus Efficiency with Flash Arrays
Flash storage arrays offer high performance and capabilities like compression and de-duplication for storage efficiency. However, flash storage arrays – and most storage systems – typically only provide simplistic encryption that fails to deliver the requisite levels of security.
On the other hand, many enterprise applications now offer native encryption capabilities. This means storage arrays will receive encrypted data streams from the file, application or database server. These encrypted data streams affect the storage efficiency of the storage arrays.
Enterprise customers are demanding better security without giving up on storage efficiencies or the performance offered by flash arrays. Fortunately, meeting the customer requirements is possible using a key sharing paradigm but requires close collaboration between the application and storage array vendors. Key sharing implies the storage array and the application use the same encryption key for encrypting and decrypting data at the application layer and in the array.
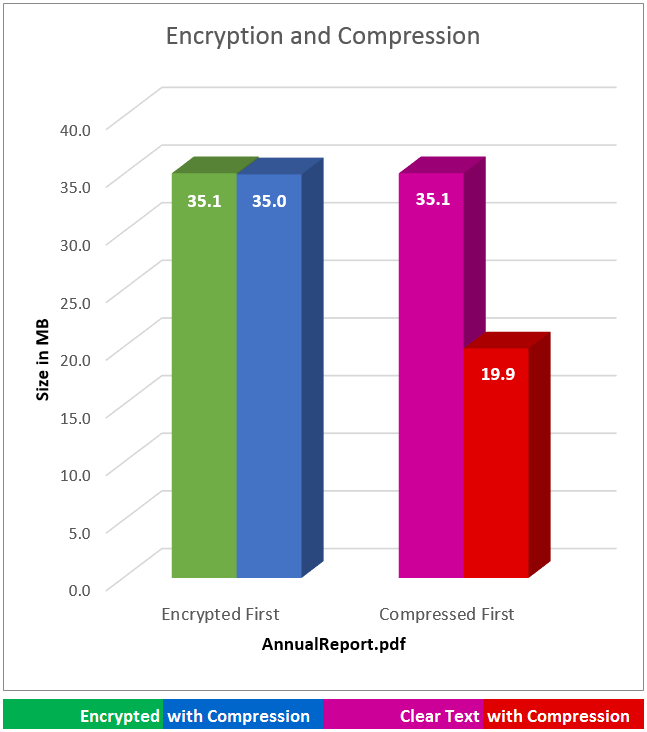
The following diagram illustrates the loss of efficiency when an encrypted file is compressed. Compression efficiency depends on the type of data and in this example, a PDF file was used for compression.
The Best of Both Worlds – Better Data Security with Great Storage Efficiency
Security is stronger when implemented and enforced at the application layer. This includes access controls, encryption at different levels of granularity (e.g. file, folder, file system) or encryption of specific elements of structured data (e.g. columns of database).
Storage arrays that are designed to receive encrypted data streams from an application, file or database server can maintain the storage efficiencies by using a key sharing paradigm. The following diagram illustrates key sharing paradigm between a collaborating storage array and a file or database server.
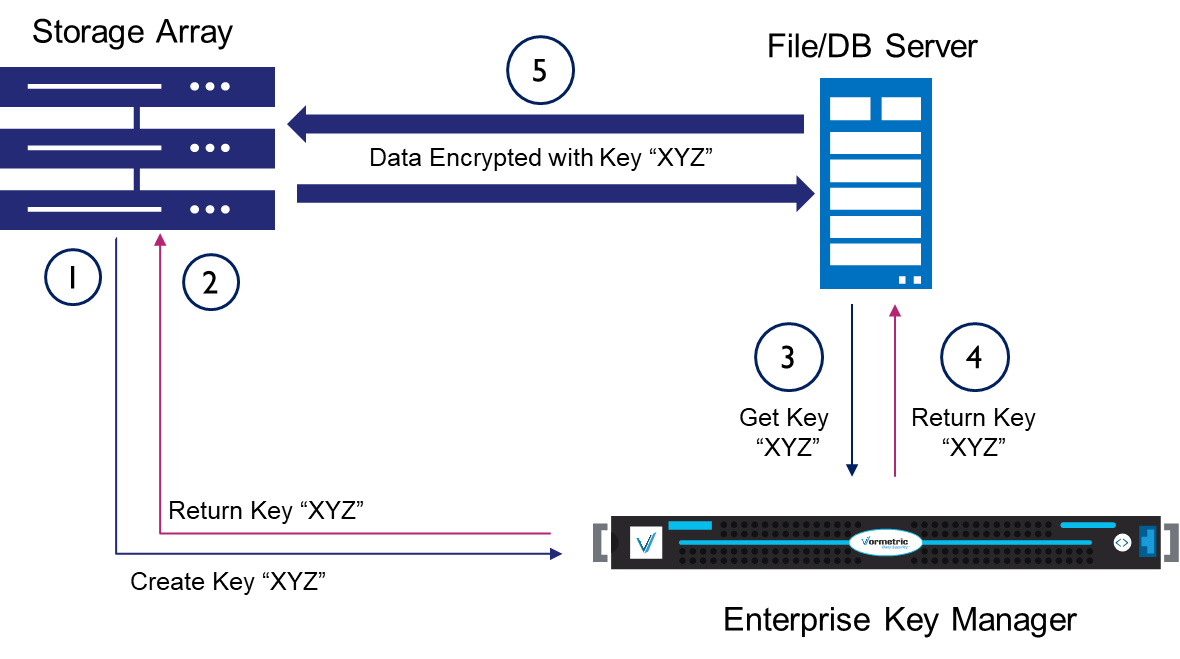
Using a pre-defined “hand shake” protocol, both the storage array and the file server request the same data encryption key (in this example the key is called “XYZ”) from an external key manager. This key is used by the array as well as the file server to encrypt and decrypt data streams.
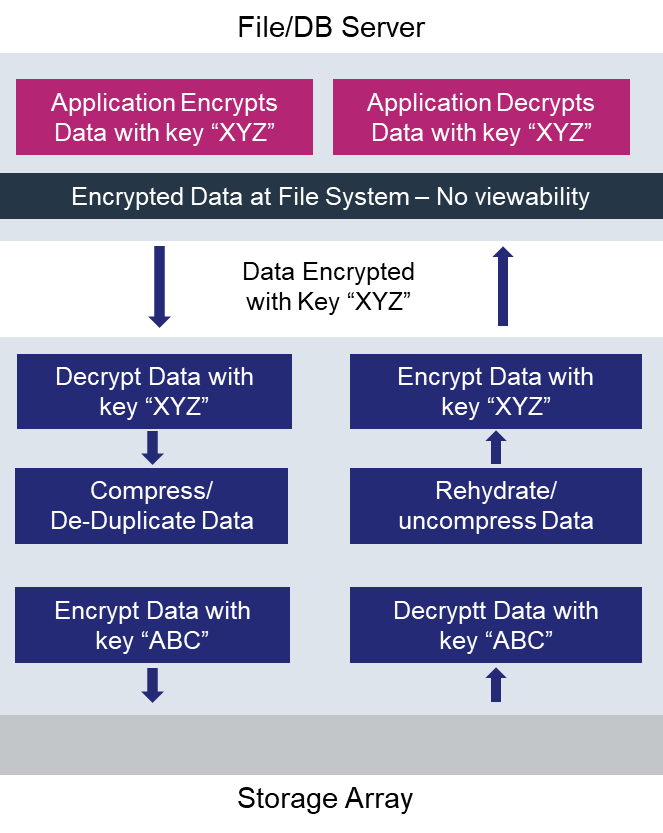
The next diagram illustrates the workflow between an application and a storage array using the key sharing paradigm. The application encrypts the data with data encryption key “XYZ” and sends the encrypted data to the storage array. The storage array, configured to receive encrypted data streams, decrypts the data using the data encryption key “XYZ”, compresses/de-duplicates the data (to realize the storage efficiency), re-encrypts the data and stores the data on the storage medium. When returning data to the application, the storage array does the reverse, i.e. decrypt the data on the storage, un compress/un de-duplicate the data (also known as rehydration) and re-encrypt the data with the data encryption key “XYZ”.
Conclusion
Data encryption in an array offers minimal to no data protection and most storage arrays do not have robust encryption key management that meets enterprise standards. Better, stronger security can only be achieved at the application layer.
In order to take full advantage of the storage efficiency of all-flash storage arrays, while also bolstering data protection, I recommend using an external encryption key manager and a standards-based key management protocol such as the OASIS Key Management Interoperability Protocol, or KMIP. With an external key manager, encrypted data streams can be decrypted from the host first, then compressed and de-duplicated. The data being read by the host can then be re-encrypted, helping organizations securely realize the full potential of all-flash arrays.
To learn more about unified key management solutions from Thales, click here.
