Todd Moore | Global VP of Data Security Products at Thales
More About This Author >
Todd Moore | Global VP of Data Security Products at Thales
More About This Author >
 Todd Moore | Global VP of Data Security Products at Thales
More About This Author >
Todd Moore | Global VP of Data Security Products at Thales
More About This Author >
Data Security Posture Management (DSPM) is quickly becoming a centerpiece in modern security strategies—and for good reason. As sensitive data sprawls across clouds, apps, endpoints, and third-party ecosystems, organizations are under increasing pressure to understand their risk exposure and tighten their security posture.
The truth is that no company can posture its way out of a breach. Organizations that are not actively protecting their data—encrypting it, containing its sprawl, and managing access—are leaving the door wide open.
While DSPM brings much-needed visibility and insight into where data lives, who’s accessing it, and how it’s being used, posture management without protection is like building a fire escape but never installing smoke alarms. Both are critical.
In this blog, we will look at why data protection is a crucial ingredient of DSPM.
Why Visibility Alone is Not Enough
Most DSPM tools do an excellent job of helping entities inventory their data and highlight misconfigurations, permissions issues, or suspicious behaviors. This is a crucial first step—but it is not the last one. Knowing data is vulnerable and actually securing it are two very different things.
Think of it this way: if DSPM is the radar, data protection is the shield. Threats cannot be intercepted with visibility alone—proactive defenses that are baked into the posture strategy itself are key. This is particularly true in a world where cyberattacks move faster, insider threats are harder to detect, and regulations demand provable safeguards, not just alerts.
Businesses Cannot Protect What They Cannot Control
It is easy to underestimate how quickly data can escape its boundaries—a customer record duplicated for testing, an analytics report emailed outside the business, a backup left exposed in a misconfigured cloud bucket. Multiply that by the number of users, platforms, and third-party tools in use—and data sprawl moves from an inconvenience to a major risk vector.
This is why controlling where data lives is a core pillar of DSPM, not an afterthought. Posture cannot be managed if sensitive data is floating untethered across the business environment.
To truly reduce risk, organizations must combine posture management with concrete protections:
- Encrypting sensitive data and metadata so it is unreadable even if exposed
- Replacing high-risk data with tokens to prevent misuse
- Managing secrets and keys with strong access control
- Monitoring behavioral patterns to pinpoint anomalies and potential abuse
Companies who are not doing this are not doing DSPM—they are merely watching and hoping.
DSPM Demands a New Approach to Data Protection
The security perimeter has all but dissolved—the real perimeter is now data itself. That’s why forward-thinking entities are embedding data protection deep into their DSPM strategies, focusing on encryption, tokenization, and resilience to new threats like GenAI and quantum computing.
The idea is not to lock everything down—it is to protect data in motion, at rest, and in use across every environment where it may live. After all, posture is about readiness, and firms are not ready if their most sensitive information is unprotected.
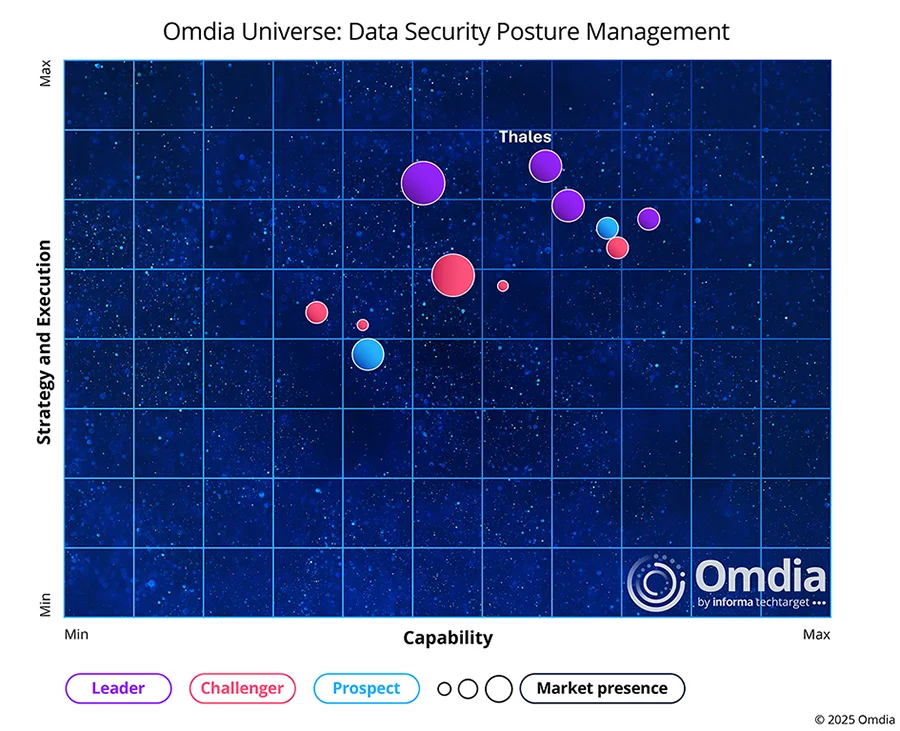
Analyst Research
Thales eclipses other DSPMs
See why we’re a leader in the Omdia Universe Report
How Thales Can Help
Thales brings a powerful layer of protection to DSPM programs, helping businesses not only see their data, but secure it. At the heart of the offering is the CipherTrust Data Security Platform, which delivers modern, scalable data protection capabilities to meet evolving DSPM needs.
Thales sets itself apart in many ways:
Protecting Data and Metadata With Encryption
Thales protects both data and metadata with strong encryption across cloud, on-premise, and hybrid environments. It also provides centralized key and secret management, helping firms maintain control and limit the risk of unauthorized access—even should data be exposed.
Reducing Data Sprawl Through Tokenization
To limit where sensitive data lives (and reduce compliance scope), Thales supports data tokenization—replacing real data with tokens that are ineffective outside of their intended system. This helps organizations keep data secure while maintaining business agility.
Preparing for Post-Quantum Threats
The Quantum threat is pending; it is not a science-fiction problem anymore. With quantum-safe encryption and crypto-agile frameworks, Thales is helping customers prepare for the next wave of threats by adopting algorithms resilient to future decryption techniques.
Understanding Relationships Across Security Incidents
Thales does not protect data alone—it helps teams understand how incidents unfold, correlating access events and behaviors across systems. This gives security teams a clearer picture of what happened and where to focus their response, whether it’s insider misuse or an external breach.
DSPM is Essential—But Not Enough
DSPM is essential—but it’s not enough on its own. No business can manage its data security posture if its data is not properly protected. Encryption, tokenization, and control over data sprawl are foundational to any cybersecurity strategy.
With Thales, organizations can move beyond visibility and into actionable protection, reducing their risk today and preparing for tomorrow's threats. When visibility meets protection, posture becomes powerful.
Choosing the right DSPM solution is critical to building a resilient, future-ready data security strategy. Learn more about Thales' CipherTrust Data Security Platform to discover, protect, and control sensitive data across your hybrid and multi-cloud environments. Download our eBook to understand the 5 questions you need to ask before selecting a DSPM solution.
Choosing the Right DSPM Solution
Learn five things you should never overlook when selecting a DSPM solution.