This morning we announced, in tandem with our partner 451 Research, the Global Edition of the 2018 Thales Data Threat Report. It’s abundantly clear that medium to larger enterprises (the focus of the report and underlying survey) are finding it harder than ever to protect their sensitive data.
The twin drivers of the problem are increased threats and the drive to digitally transform how organizations deliver value and revenue. This year’s report documents these twin drivers, what organizations are doing about the problems and best practice recommendations for how IT security stances should change to meet both needs.
First – The breaches
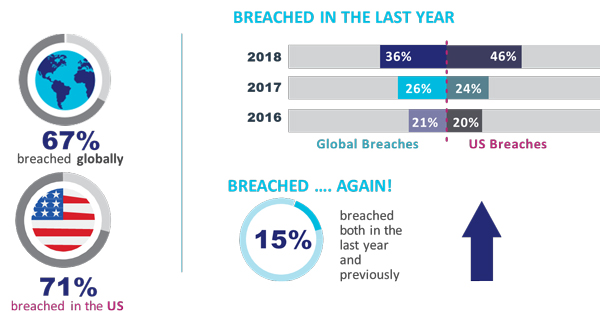
It’s probably no surprise to anyone reading this that organizations are experiencing record data breaches; we hear about the breaches almost daily even in mainstream media. What we capture as part of our data is a bit different, however. We’re measuring the percentages encountering breach incidents, rather than how many records were compromised. And it’s not good news. Not only has the percentage of organizations who have ever encountered a data breach increased again this year (67% this year, up from 56% last year), but over half of those breaches happened in the last year (36%) and almost half of those breached in the last year, were breached before (40%).
Not only are there record high rates of breaches, but organizations are being breached again, and again.
Why does this keep happening? The answer is probably twofold:
- The rate at which digital transformation is driving change
- A failure to adopt modern data security methods for existing data sets
Digital transformation drives massive change
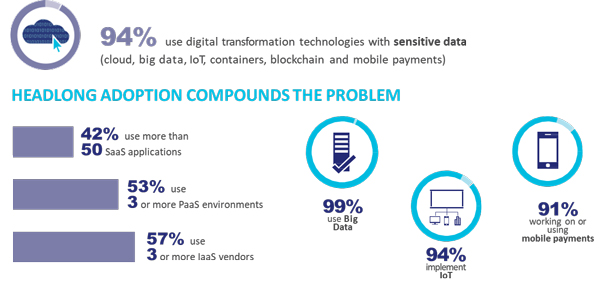
Digital transformation inherently drives organizations into a data driven world – and each technology used for digital transformation (cloud, big data, IoT, blockchain, mobile payments and more) requires its own unique approach to protecting data. What we found is that 94% are using sensitive data within these environments.
Adoption levels are high across the board for these technologies. A good case in point is that it’s not just retailers adopting mobile payments or the financial industry using blockchain, it’s every segment we measured.
- Cloud – now universally used (100% of our sample)
- Big Data – 99%
- IoT – 94%
- Blockchain – 92%
- Mobile payments – 91%
What did our respondents say they needed to further adopt these environments? For each technology area, encryption or encryption-related technologies were the requirement.
The failure to adopt modern data security methods
To turn back the data breach tide, organizations must change how they are protecting their data-at-rest. The below recommendations apply for both data sets stored within the databases and file systems of a traditional data center, and for those used with digitally transformative tool sets.
- Encrypt the data
- Control access to the data so that only those with a “need to know” can access it
- Watch data usage and access patterns
- Unauthorized access attempts to data sets can be an early warning of an attack that has already penetrated other security controls, and is now working to get access to data
- Patterns of access by privileged users and other accounts that show anomalous usage patterns can be another clear indication that someone is after your data
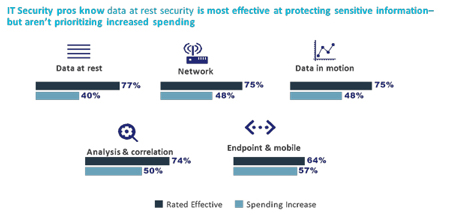
And, we found that people know that’s what’s needed. Encryption was rated as the most effective tool for protecting data (77%). Nevertheless, end point and mobile defenses are getting the biggest increases in spending (57%) while data-at-rest security (which includes encryption) is dead last at 40%.
So what needs to be done?
I invite you to read the report for all the detail on the results and Garrett Bekker’s best practice recommendations (Garrett is Principal Analyst for Information Security at 451 Research, and author of the report). You can find it here. With Data Privacy Day conveniently approaching, it’s an especially good time to get informed.
