Healthcare’s IT evolution has brought numerous security challenges including regulations, the use of digitally transformative technologies that have created huge amounts of data to store and protect, and the extraordinary value of electronic personal health information (ePHI) to cybercriminals.
In this blog post, I’ll discuss how healthcare enterprises can not only meet these challenges, but go beyond compliance to best practice to secure their data and their reputations.
Regulations
HIPAA and the HITECH Act and Omnibus Rule stimulated the digitization and protection of patient records. The Meaningful Use portion of the HITECH Act provided healthcare organizations a carrot to encourage the adoption of electronic health records. That carrot turned into a stick, when in 2015 the incentives switched to penalties. As a result, the proportion of American hospitals with an electronic health record went from just 9% in 2008 to 96% in 2015.
In addition, the health information exchanges tied to the HITECH Act provided financial awards to build out exchanges, which has driven further digitization of patient records.
But for healthcare, HIPAA HITECH is just the tip of the regulation iceberg. The list of mandates affecting the industry includes a plethora of country- and industry-based regulations for all kinds of sensitive data.
The Role of Digitally Transformative Technologies
In an effort to meet compliance requirements – and with an eye toward cutting costs – the healthcare industry has turned its attention toward embracing digitally transformative technologies, including cloud, big data, Internet of Things and containers. These technologies allow organizations to better create and manage data, as well as, store critical information more efficiently.
According to the Thales 2018 Global Data Threat Report, Healthcare Edition, 95% of U.S. respondents reported using these technologies with sensitive data. With each new technology comes unique data security challenges that must be addressed, as they increase the attack surface available. Among some of the more notable findings from this year’s report:
- All (100%) U.S. respondents surveyed are leveraging cloud technologies
- Almost all (96%) of U.S. respondents are using big data; 90% are working on or using mobile payments, and 92% have a blockchain project implemented or are in the process of implementing one
- 92% are leveraging IoT devices, which may include internet-connected heart-rate monitors, implantable defibrillators and insulin pumps
Consequently, these organizations have emerged as a prime target for hackers, putting valuable medical data at risk. While a stolen credit card has a time-limited value, PHI and electronic medical records (EMR) are packed with immutable data that can, and do, fetch hundreds of dollars per stolen record on illegal online markets.
Healthcare Data Prized by Cybercriminals
Garret Bekker, principal analyst, information security at 451 Research, writes “The double-edged sword of digitization is that individual healthcare data is exposed to more people, in more places and on more devices,” and “Electronic health records contain a trove of personal data, making them an ideal target of one-stop hacking for cyber thieves.”
According to the 2017 “Cost of Data Breach Study” by the Ponemon Institute, in partnership with IBM Security, healthcare is the most breached industry with nearly 60% of all leaks in 2017 at an estimated cost of $1.2 billion.1
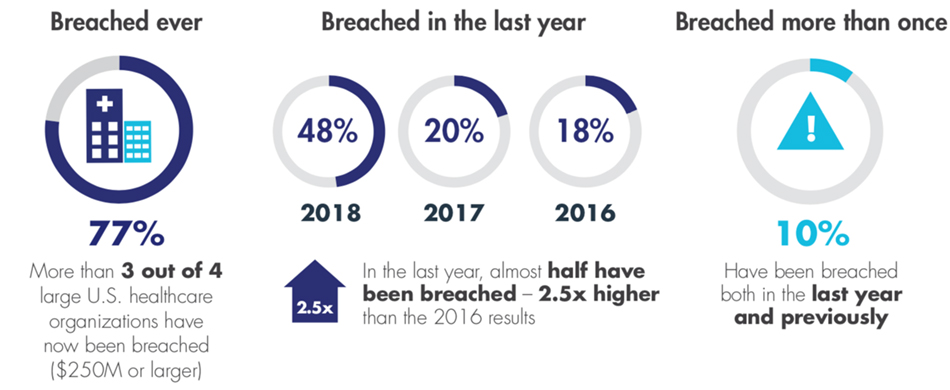
Our Healthcare Edition backs this up. Nearly half (48%) of U.S. healthcare respondents reported getting breached in the last year alone – more than 2.5X the rate from only two years ago – and 56% report feeling either ‘very’ or ‘extremely’ vulnerable to data breaches. Further, more than three-fourths (77%) of U.S. healthcare respondents reported at least one breach at some time in the past. This is the highest percentage among all U.S. vertical industries polled in this year’s report.
Protecting Your Sensitive Data
Unfortunately, data cannot protect itself. Today senior management understands that to protect the reputation and financial assets of the enterprise, they must protect patient, employee, and other sensitive data. This means going beyond compliance to best practice. As Mr. Bekker writes: “Global and industry regulations can be demanding, but firms should consider moving beyond compliance to greater use of encryption and BYOK, especially for cloud and other advanced technology environments.”
Thales Recommendations
Best practice (and compliance with the most stringent regulations) calls for:
- Data encryption and/or tokenization for data at rest and in motion to render sensitive data unreadable or indecipherable to unauthorized individuals so that if breached, it’s useless to the cybercriminal, and you won’t need to report the breach
- Control of data user access and encryption key management to make sure only those authorized to do so can access encrypted data as clear text
- Logging user access, so your organization can identify and respond to attacks when they occur.
- The use of FIPS 140-2 certified hardware security monitors (HSMs) to provide root of trust, authentication, certification, and a hardened environment for encryption and key management
Consequently, we at Thales recommend you to adopt an enterprise-wide data protection strategy based on encryption:
- For structured and unstructured data at rest
- For data in motion and in use
- Across devices, processes, platforms and environments
Thales provides products and services that do all this and more. Let us know, if we can help.
As always, feel free to leave comments below. Alternatively, you can also find me @vikramesh or in person at this year’s HIMSS Conference. On Tuesday, March 6, from 3:30-3:50pm, I’ll expand on data security in my Titian Ballroom session “Fit for HIPAA? Patient data protection is top priority”. More information about Thales at HIMSS may be found here.
1https://www.fastcompany.com/40527767/these-industries-are-the-most-vulnerable-to-data-breaches-in-the-united-states?utm_source=feedly&utm_medium=webfeeds

 Thales | Security for What Matters Most
Thales | Security for What Matters Most