Originally Featured in Global Military Communications Magazine’s June/July Issue
With more than 65,000 employees in 56 countries, Thales is a global leader in technology solutions for the aerospace, transport, defence and security markets. Its unique capabilities include the design and deployment of equipment, systems and services to meet complex security requirements. Amy Saunders spoke with Nick Jovanovic, VP Federal of Thales Federal (a division of Thales Defense & Security, Inc.), to discuss the findings of the 2018 Thales Data Threat Report, Federal Edition.
Question: Can you provide an overview of the 2018 Thales Data Threat Report, Federal Edition, and elaborate why it’s needed today more than ever?
Our 2018 Thales Data Threat Report, Federal Edition, issued in conjunction with analyst firm 451 Research, polled U.S. federal IT leaders about data security, data breaches, spending practices, and a gamut of other security-related issues.
This year’s report is especially relevant because it tells us federal agency data is under siege. Seventy-one percent of respondents report their organization was breached sometime in the past. Of those organizations, 57 percent have been breached in the last year – a number that is three times the rate of just two years ago (in our 2016 report, 18 percent reported a breach within the last year, and in our 2017 report, 34 percent reported a breach within the last year). The 57 percent rate statistic is the highest of all verticals we measured in this year’s report (others include the healthcare industry, the retail industry, and the financial services industry) or any region surveyed.

These statistics indicate data breaches remain pervasive within the federal government, and that the current methods being used to secure agency data are not working as effectively as they could. There also appears to be some confusion over how to best protect critical data. Respondents cite data-in-motion and data-at-rest solutions as being the most effective at preventing breaches, but their spending decisions don’t align with this sentiment. While 73 percent are increasing spending, 56 percent are spending that money on endpoint and mobile defenses, and only 19 percent are spending it on data-at-rest security.
Question: According to the report, in the past year, 57 percent of federal respondents experienced a data breach, compared with 34 percent in 2017 and 18 percent in 2016. What can you tell us about these breaches, and why are they becoming so prolific?
There are some obvious reasons: Criminal hackers want valuable citizen PII; nation-state hackers with their own agendas seek to infiltrate agency databases; chronic funding and staffing issues remain a problem; and most federal agencies are stuck with some of the oldest systems and software found anywhere. But, that’s not the whole story. Security spending decisions are also playing a sizable factor. As I noted in my answer above, federal agencies are not spending their IT security dollars on solutions that will most effectively protect data. Endpoint and mobile solutions are seeing the biggest spending increase (even though they’re rated at the bottom in terms of effectiveness) and data-at-rest security is seeing the lowest spending increase (even though it’s cited as highly effective).
Additionally, initiatives pushing for IT modernization within the federal government mean more data is being stored in the cloud; in big data repositories; being used for IoT purposes; and being stored in containers. This digital transformation is creating new risks, because each environment, and each vendor within these environments, requires a unique approach to protecting data.
I think it’s worth further expanding on our cloud technology findings. More so than commercial enterprises, government agencies are making a massive shift to the cloud. This bears out in the stats:
- Nearly half (45 percent) of U.S. federal respondents used more than five Infrastructure-as-a-Service (IaaS) vendors
- Forty-eight percent used more than 100 Software-as-a-Service (SaaS) applications
- Over two-thirds (72 percent) of respondents expressed concerns about increased vulnerabilities from shared infrastructures, followed by custodianship of encryption keys (62 percent) and security breaches in the cloud (68 percent)
Even though federal agencies have strong compliance standards (NIST 800-53; FedRAMP; and the Federal Risk Management Framework), it appears agencies are not able to catch all of the non-compliant usage. Look at how frequently we hear about AWS S3 buckets left out in the clear with sensitive information for hackers to mine.
There’s also the issue with keeping control of keys in the cloud. A basic security maxim is that those who control the keys control access to the data. Yet, federal agencies have a preference for the cloud provider to control the keys (34 percent) over local key control (32 percent). Interestingly, this is a potential violation of the same compliance standards I cited earlier.
Question: In a world where some 68 percent of U.S. respondents believe they are ‘very’ or ‘extremely’ vulnerable to a data breach, why are more people not taking action sooner to safeguard their networks? What are the challenges involved?
Many people still think data security (especially encryption) is complex and has a performance problem. As noted in the report, the top two perceived barriers to data security deployment are complexity (49 percent) and performance impacts (41 percent). This long-standing, dated, and increasingly inaccurate notion needs to be put to bed. Performance concerns tend to be a relic of the early days of encryption solutions, when software-based encryption was the rule, and performance impacts were real.
Fortunately, data security platforms like ours, and SaaS-based data security applications, are making complexity in deployment, management, and operation a thing of the past.
There is also a perception among federal agency IT personnel that management of enterprise encryption keys will be overly challenging, which further complicates an IT environment fraught with budget and staffing limitations. But, federal government agencies can simplify encryption key management and secure their data by selecting encryption and key management technologies that offer smart, centralized approaches and work across clouds, on-premises and in data centers. Many federal agencies are already exploring this approach, as illustrated by the 47 percent of respondents who plan to implement ‘bring your own key’ solutions to remotely manage their cloud deployments. This security strategy will assist them in better protecting and controlling their data.
Question: The use of commercial cloud services is booming right now, but some 72 percent of report respondents expressed concerns about increased vulnerability from shared infrastructures. What are the risks associated with cloud-based services, and how can a data-centric security approach help?
Agencies are responsible for the security of their data both on-premises and in the cloud. As their workloads migrate to multiple cloud providers, they must be confident in the security of their data. Agencies must be in compliance with internal and industry data protection mandates. Their data must be protected in the event a subpoena is issued to their cloud provider. They should also be able to move data quickly from one cloud provider to the next.
To better understand how a data-centric security approach can help, check out the below cloud computing ‘shared responsibility’ graph.
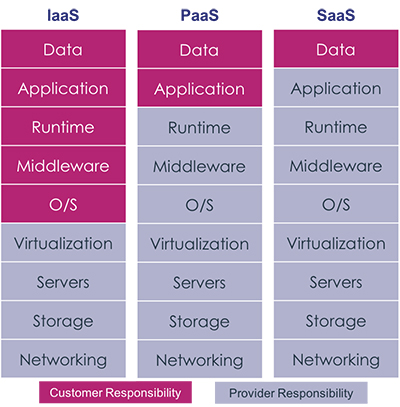
See the common theme? That’s right, it’s data. While there is a shared responsibility between the cloud provider and its customers, the customer is always on the hook for ensuring it has the means to protect its data.
Some solutions to meet the shared responsibility model might include:
- Bringing your own encryption for physical or virtual servers running from your premises to multi-cloud environments
- Using tokenization with dynamic data masking to make it easy to protect sensitive data and to add policy-based data masking to applications
- Leveraging a centralized key and data access policy management solution to provide customer controlled key management and data access
Question: The 2018 Thales Data Threat Report, Federal Edition, found that 93 percent of respondents plan to increase spending this year. Why isn’t this as good as it first seems?
Despite 78 percent of respondents citing data-in-motion security and 77 percent citing data-at-rest security as being most effective at preventing breaches, agencies are prioritizing increases in data-at-rest security spending dead last. Endpoint and mobile defenses spending is increasing for 56 percent of respondents and data-at-rest security spending is increasing for only 19 percent.
Unfortunately, we’re not spending our IT security dollars where it will protect data best.
Question: What does the future landscape of the cybersecurity sector look like to you? What steps need to be taken to ensure data security?
According to the Report to the President on Federal IT Modernization we need to reduce the federal attack surface through enhanced application and data-level protections:
“…agencies should shift their focus to placing protections closer to data, specifically through improved management and authentication of devices and user access, as well as through encryption of data – both at rest and in transit. This approach curtails an attacker’s likelihood of gaining access to valuable data solely by accessing the network, and it has the potential to better block and isolate malicious activity.”
We agree. Organizations need to adopt a defense-in-depth approach, move away from an over-reliance on network and endpoint security, and create a comprehensive data-centric approach to securing their agencies.
With increasingly porous networks, and expanding use of external resources (SaaS, PaaS and IaaS most especially) traditional endpoint and network security are no longer sufficient. When implemented as a part of the initial development (for ease of implementation versus retrofitting at a later date), data security – most especially, encryption – offers increased protection to known and unknown sensitive data found within advanced technology environments.
The alternative? Federal agencies will continue to suffer, and we will see even higher breach rates next year.
For more information about Thales eSecurity’s federal government security solutions, visit here. You can also leave a comment below, or follow Thales on Twitter, LinkedIn, and Facebook.

 Nick Jovanovic | VP, federal, for cloud protection and licensing activity at Thales
Nick Jovanovic | VP, federal, for cloud protection and licensing activity at Thales