
The unexplained and seemingly paranormal are actually a year-round phenomenon in IT Security. This year has been no exception. The shrieks and screams coming from CISOs and their staffs over malware has led to zombie-like stares. Because the never-ending battle against the evil forces of the dark web continues with regard to ransomware and its ghoulish close cousins – leakware and scareware.
Actors on the dark web, hiding behind their dark masks of anonymity, continue to brew their devilish ransomware potions. Not every ransomware potion is alike and the recovery from the electronic equivalent of a slash-and-gash malware attack can vary, depending on exactly how an attack decomposes.
Encryption is... a panic room for your data and means you’ve treated your data well by preparing for those smash-and-grab attacks in advance.
Let’s take a brief look in our cybersecurity crystal ball at all three. Then we’ll see if we can devise a quick and basic enterprise blueprint that can serve as our magical IT Security dagger, sending those wearing their dark cloaks back howling from whence they came.
Ransomware
Occurrences of ransomware of late have seemingly died down. Those wearing electronic Jason masks have recently stalked other avenues of enterprise torture such as crypto-mining. Yet ransomware hasn’t completely lost its criminal appeal nor its potency. There were plenty of knocks on enterprise doors and tricks meted out against organizations this year that were plain and simple ransomware.
Ransomware essentially comes in two icky flavors: file encryption or cryptolocker. Either way, the goal is to quickly overwhelm and immediately kill your business operations through encryption, then panic you into immediate payment. Our enterprise blueprint is intended to surprise such fiendish criminal minds and help you avoid handing out any enterprise candy in the form of payments.
Leakware
Leakware can often look like ransomware, but the way it creates panic is downright dastardly. Leakware essentially crashes through the windows and grabs sensitive information you should be protecting through encryption and strong access controls. Leakware threatens to scrape and then sell or make that sensitive information public unless you treat in payments. With leakware, the trick and its bone-jarring implications is on you and your enterprise, leveraging your own obligation to protect data against you.
Leakware is entirely preventable as all data should be protected the moment it’s born – from cradle to grave (eg. data redaction). Hold on to your IT Security shopping bags because our dagger of choice, which we will discuss faster than you can say “Boo!”, will stop any leakware attack right in its tracks.
Scareware
Ransomware, Leakware, Scareware… oh my! The Frankensteinian variants won’t stop coming, will they?! Scareware is exactly what it means. It exists to scare you into dropping the payment into the extended bag of Bitcoin. But not so fast, my little enterprise cybersecurity gremlins! Scareware is basically a harmless ghost whose threat doesn’t actually exist. It’s pure vapor.
Scareware usually just makes a minor incision (eg. hack) of some sort in an infected system to simply disable it, grimly inform you that it is “ransomware,” and simply scare you into making payment. Whaa-haaa-ha-ha… It’s a neat trick, but no need to panic. Often your data hasn’t been grabbed or even touched at all. It’s all an electronic apparition designed to look like ransomware, when in fact, it’s not ransomware at all.
Encryption with strong access controls that disallows privileged access often negates all three variants of ransomware in addition to many other forms of attack
An Enterprise Blueprint
It’s important to realize these grim threats are real and represent a lot of inconvenience at least for a very scary period of time. It could mean a real rake to the face of your brand, reputation and bottom line if you aren’t prepared for thwarting such attacks. In some cases, consequences can run even deeper and can lead to deep sixing your brand and even your organization. RIP!
The first step in building our enterprise dagger is preventing these attacks in the first place. The most common vectors or cracks through which evil hands come groping through your oaken enterprise doors are:
- Email phishing & malware links
- Email attachments
- Internet Ads (also known as “drive by attacks”)
- Malicious web sites
- System vulnerabilities
The above is a great checklist for stopping 99% of these fiendish attacks on your enterprise. Make sure you check off in addressing each one.
The Dagger of Choice: Encryption with Strong Access Controls
For ransomware and its variants, enterprises can bar their electronic windows best by encrypting data the moment it’s born and wrapping that data with strong access controls that don’t break down through the nefarious hijacking of privileged access. Eighty percent of all attacks on data take place through privileged access whether welded by malicious insiders or those who break through the doors welding the axe of criminal intent.
Devise [an] enterprise blueprint that can serve as [your] magical IT Security dagger
But beware! Encryption alone won’t stop ransomware as encrypted data can simply be re-encrypted or doubly encrypted. Strong access controls that deny unintended access to data is your strongest defense against the horror of real ransomware.
In the case of scareware and especially leakware, encryption will yield very high value as data you have encrypted means no real information could possibly have been leaked outside your organization. Encryption is essentially a panic room for your data and means you’ve treated your data well by defending against those smash-and-grab attacks in advance.
Overall, encryption with strong access controls that disallow privileged access often negates all three variants of ransomware in addition to many other forms of attack.
Going Beyond Prevention & Further Preparing For a Hit
If you’ve done all you can to prevent the terrifying experience of ransomware and its variants, you should still look for advantage by preparing your organization in advance for any actual hits.
Briefly:
- Assess Your Risk: Understand your market and your risk for specific attacks, understand the value of your data, comprehend the types of ransomware and pre-assess how you would react to the common types taking an “if this, then that” approach to the common variants.
- Formulate Your Plan of Response: A basic plan should be formulated around Assess (what hit us?), Scope (how big is it?), Isolate (keep the attack contained), Pay or No Pay, and Execute (execute the plan you’ve made in advance for recovery).
- Practice Business Continuity (BC)/Disaster Recovery (DR): Ransomware is a ferocious, full-frontal attack intent on killing your business operations and continuity. Practice BC and DR! This includes building and executing an appropriate communications plan.
- Listen & Reassess: Subscribe to and listen on common channels where news about ransomware tends to travel. Social media such as Twitter and LinkedIn can help your organization understand in advance what is popular and up and coming in the ransomware arena. Then reassess your plan at least twice a year.
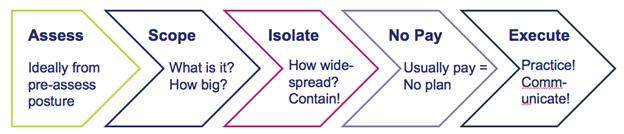
Figure 1 - Basic Enterprise Response Plan once attacked by ransomware or one of its variants
Pay or No Pay?
Often answering the question of whether to pay or not pay is solely based on lack of preparedness as any lack of preparedness is exactly what attackers are counting on.
Handing out the treat of payment isn’t completely out of the question, but often it can be completely avoided by being prepared. Know that if you do pay, your chances of gaining back your data or your data not being leaked is only about 80%.
Conclusion
Ransomware still exists as a horrifying reality for many enterprises. Acquire some peace this season using the IT Security dagger of encrypting your data the moment it’s born, wrapping that encrypted data with strong access controls and denying the welded axe of your own privileged access used against you.
Finally, build an enterprise plan, in advance, akin to the blueprint above. This will help guide you to safety and through the chaos of ransomware and its variants in the event your enterprise is still infected by one of these malevolent potions still being brewed on the dark web.
Leave a comment below, or find us Twitter, LinkedIn and Facebook.

 Chris Olive |
Chris Olive |