Numerous attacks due to compromised mobile devices
Mobile device usage has become crucial to business agility and productivity for years but the number of compromised devices is growing too, as shown by the Verizon Mobile Security Index 2021 Report:
- 40% of respondents said that mobile devices are the company’s biggest IT security threat
- 53% said the consequences of a breach they suffered were major
This is especially relevant to an organization’s security posture. Not only are mobile devices used as end points to access corporate mail and other enterprise applications, they are also frequently used as authentication devices. Authenticator apps that enable Push notifications and OTP (one-time passcode) generation are one of the most prevalent forms of two factor authentication in use today.
Limited visibility on users’ devices can undermine authentication integrity
In ongoing discussions with our customers, we received feedback from those who are concerned about letting end users authenticate to sensitive IT resources using a device that could be compromised - for example a jailbroken or rooted device. We frequently hear from IT security professionals that “the risk associated with the mobile device is something we care about. If a device is jailbroken or rooted we may preferably want to block the authenticator app
SafeNet Trusted Access helps ensure authentication integrity on devices
Thales is now enabling IT security professionals who use SafeNet Trusted Access, its access management and authentication platform, to detect at-risk mobile and desktop devices when also used for authentication.
SafeNet Trusted Access can detect risks on devices equipped with the SafeNet MobilePASS+ authenticator app. The state of the device is checked, and detected risks are reported and displayed in the SafeNet Trusted Access management console.
Each mobile and desktop platform comes with its own security and the means of avoiding that security. That’s why we have implemented a tailored approach that detects different types of risks depending on the platform:
- Debug: the Android or Windows device is running in a debugging environment
- Hook: a hook function was detected on the device
- Jailbreak: the iOS mobile device is jailbroken
- Root: the Android mobile device is rooted
This new risk detection capability is provided on top of the existing best-in-class security framework that SafeNet MobilePASS+ offers to protect against attacks, including DSKPP encrypted token enrollment.
Continuous Risk Detection
To improve protection against compromised devices, the risk detection is activated regularly. For example at initial activation, each time the authenticator or device OS is upgraded and each time the user launches the application.
Help IT Professionals to mitigate risks
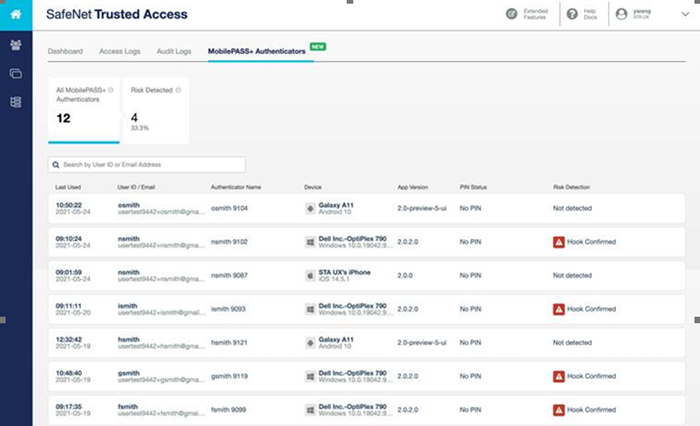
Thanks to a dedicated dashboard and log, SafeNet Trusted Access administrators can quickly see which devices are at-risk, and can then follow up in a timely manner with mitigation actions, for example blocking the authenticator on a user’s device.
Learn how SafeNet Trusted Access can ensure authentication integrity for your users.
Frequently Asked Questions
What is a jailbroken device?
Jailbreaking is the process of exploiting the flaws of a locked-down electronic device to install software other than what the manufacturer has made available for that device. Jailbreaking allows the device owner to gain full access to the root of the operating system and access all the features. It is called jailbreaking because it involves freeing users from the ‘jail’ of limitations that are perceived to exist.
What is a rooted device?
Rooting is a process of unlocking Android smartphones and tablets to attain higher administrative privileges. A rooted device is an Android gadget that has been jailbroken to install unapproved apps, update OS, delete unwanted apps, under clock or overclock the processor, replace firmware and customize anything else.
What is a Hook?
Hooking is a term for a range of code modification techniques that are used to change the behavior of the original code running sequence by inserting instructions into the code segment at runtime.
If a device is jailbroken, rooted or has hooks installed, a malicious actor could gain control of the device and authenticate to an enterprise resource, instead of the legitimate user.
What is a debug?
Debugging allows a device to communicate with a computer that may be running a program in order to use advanced operations. When a device is in debugging mode, a computer connected to the device can read all data, and control the apps. The security of the device could be compromised and make it open to attacks.

 Philippe Allard | Product Manager
Philippe Allard | Product Manager