Bruce Schneier recently blogged:
A bunch of networks, including US Government networks, have been hacked by the Chinese. The hackers used forged authentication tokens to access user email, using a stolen Microsoft Azure account consumer signing key. Congress wants answers. The phrase “negligent security practices” is being tossed about—and with good reason. Master signing keys are not supposed to be left around, waiting to be stolen.
But “negligent security practices” are not a new concern for the US Government. In March, John Sakellariadis wrote in Politico:
The White House worries that the cloud is becoming a huge security vulnerability. So it’s embarking on the nation’s first comprehensive plan to regulate the security practices of cloud providers like Amazon, Microsoft, Google and Oracle, whose servers provide data storage and computing power for customers ranging from mom-and-pop businesses to the Pentagon and CIA.
And in February the Treasury Department released “a report on the potential benefits and challenges associated with the increasing trend of financial sector firms adopting cloud services technology.”
We at Thales applaud the report and its intent, but as the hack of US Government networks demonstrates, the cloud security challenges it raises apply not just to the financial sector but to any organization storing sensitive data in the cloud.
The report advocates a zero-trust model for security and notes: “From the perspective of the financial institutions interviewed for this report, the security capabilities for public cloud services generally match or exceed their on-premises capabilities.” However, the report also notes some financial institutions interviewed “had challenges [assessing] the security capabilities provided by CSPs based on the current level of information supplied by the CSPs.”
As we know, the CSPs use the Shared Responsibility model for data security, which means cloud users and CSPs divvy up responsibility as shown in the graphic below from the Treasury’s report.
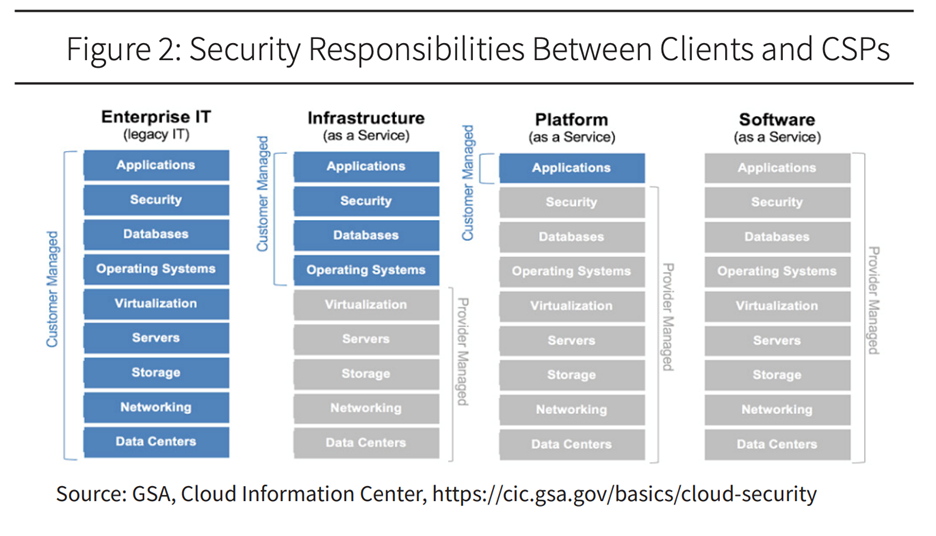
The report lists the following six challenges it feels financial institutions must address:
1. Insufficient transparency [on the part of CSPs] to support due diligence and monitoring by financial institutions.
2. Gaps in human capital and tools to securely deploy cloud services.
3. Exposure to potential operational incidents, including those originating at a CSP.
4. Potential impact of market concentration in cloud service offerings on the financial sector’s resilience.
5. Dynamics in contract negotiations given market concentration. The limited number of CSPs may give CSPs outsized bargaining power when contracting with financial institutions.
6. International landscape and regulatory fragmentation.
Thales can help any organization address issues 2, 3, 5, and 6 above when dealing with cloud security, and our theme is consistent.
The CSPs may offer a shared model, but the more responsibility your organization takes for securing your data, the safer it will be. The major CSPs do a great job securing their customers’ data. But it is nevertheless true that the best way to keep a secret is to tell it to no one. And that includes the CSPs.
In my next blog, I will address how Thales thinks about and can help you address these four security issues through more secure key management.

 Krishna Ksheerabdhi | VP, Product Marketing
Krishna Ksheerabdhi | VP, Product Marketing