Our recently released 2024 Data Threat Report showed a direct correlation between compliance and cyber security outcomes. 84% of organizations that failed a compliance audit reported having a data breach in their history. By contrast, for those that passed compliance audits, only 21% have a breach history. This correlation between passing audits and having fewer data breaches has increased over the years, with half as many organizations reporting a breach after passing audits as four years ago.
A big reason for this is better, stricter, and more detailed regulations, leading to improved, more stringent, and increasingly detailed audits that uncover vulnerabilities before they can be exploited. Very soon, a long-anticipated cyber resilience regulation comes into effect, promising to raise the compliance bar once again. On 17 October 2024, European Union Member States must adopt and publish the measures necessary to comply with the Network and Information Security Directive (NIS2). They start enforcing those measures the very next day.
Evolving from NIS to NIS2
Initially adopted in 2016, the original Network and Information Security Directive (NIS) relied heavily on the discretion of individual member states and lacked accountability. In response to growing threats posed by increasing digitalization and the surge in cyber-attacks, the EU adopted NIS2 to strengthen security requirements and cyber resilience.
NIS2 expands the original NIS Directive to cover more industry sectors, with additional risk-management measures and incident reporting obligations. It also provides for more robust enforcement. NIS2 adds to the initial directive in four key areas:
1. Expanded Scope
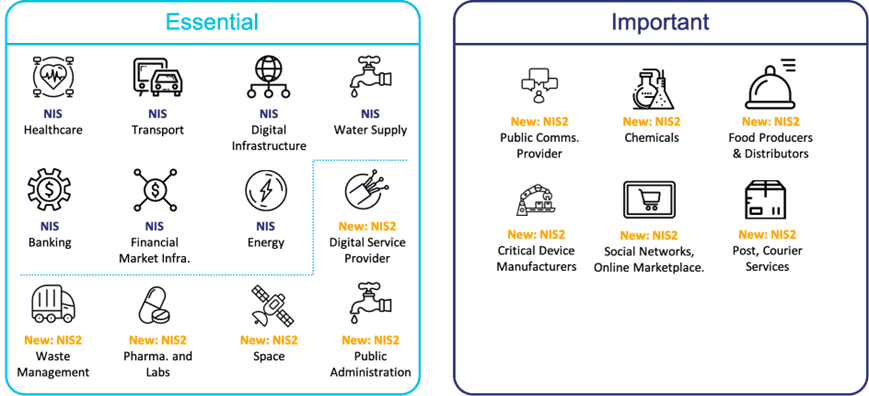
The original version of NIS identified only healthcare, transport, digital infrastructure, water supply, banking, financial market infrastructure, and energy as essential sectors. NIS2 adds digital service providers, waste management, pharmaceutical and labs, space, and public administration to the ‘Essential’ sectors category.
NIS2 also adds an ‘Important’ sector category, including public communications providers, chemicals, food producers and distributors, critical device manufacturers, social network and online marketplaces, and courier services. The image below shows the original NIS sectors, the expanded NIS2 sectors, and the designation of essential or important.
2. More stringent security requirements
The goal of NIS2 is to protect network and information systems and the physical environment of those systems from incidents. Article 21 of the Directive details the security requirements organizations must adhere to, including at least the following:
- Risk analysis.
- Incident handling.
- Business continuity/crisis management.
- Supply chain security.
- Network and information systems security.
- Cybersecurity risk management.
- Cybersecurity hygiene practices and training.
- Cryptography and encryption.
- Access control policies and asset management.
- Multi-factor authentication or continuous authentication solutions.
3. Mandatory incident reporting with specific timeframes
NIS2 requires organizations to report significant cybersecurity incidents, which are those incidents likely to adversely affect the provision of the organization’s services. Organizations must provide an “early warning” report using a standardized format and a shortened reporting timeframe of 24 hours, followed by an Incident Notification within 72 hours of first becoming aware of the incident, as well as a Final Report within 30 days.
4. Enforcement through penalties:
The NIS2 Directive imposes more severe penalties for non-compliance, including increased financial penalties.
- For essential entities, administrative fines can be up to €10,000,000 or at least 2% of the total annual worldwide turnover of the company to which the essential entity belongs, whichever amount is higher.
- For important entities, administrative fines can be up to €7,000,000 or at least 1.4% of the total annual worldwide turnover of the company to which the important entity belongs, whichever amount is higher.
How Thales Helps with NIS2 Compliance
The expanded Thales portfolio resulting from the acquisitions of Imperva and OneWelcome gives us the platform to help our customers increase cyber resilience, reduce the complexity of cyber security, and simplify compliance with regulations such as NIS2.
Thales can help Essential and Important entities address key cybersecurity risk-management requirements under Article 21 and help organizations produce complete, accurate, and timely reports to meet Article 23 requirements. We achieve this by providing solutions in three key solution areas of cybersecurity: Application Security, Data Security, and Identity & Access Management.
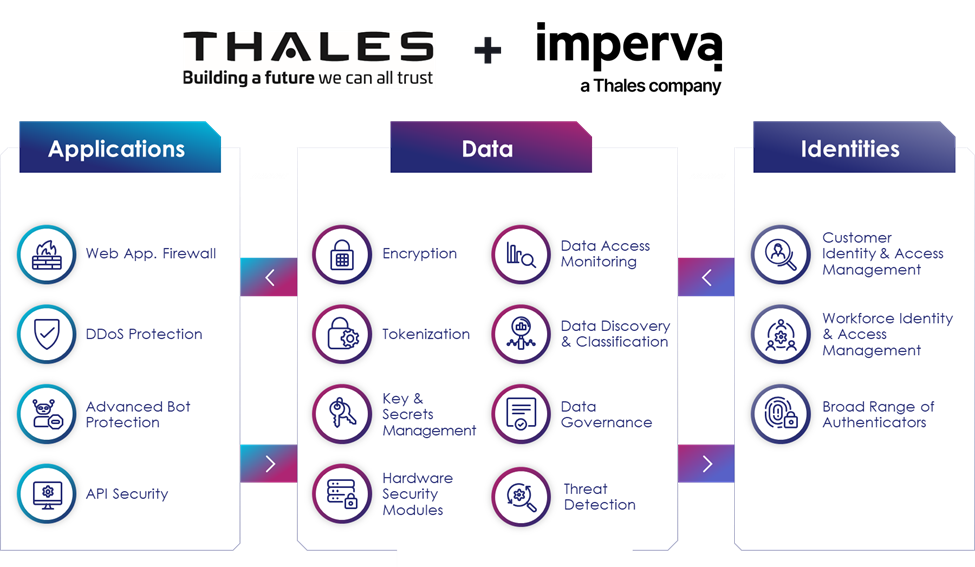
- Application Security: Protect applications and APIs at scale in the cloud, on-premises, or hybrid models. Our market-leading product suite includes a Web Application Firewall (WAF), protection against Distributed Denial of Service (DDoS) and malicious BOT attacks, security for APIs, a secure Content Delivery Network (CDN), and Runtime Application Self-Protection (RASP).
- Data Security: Discover and classify sensitive data across hybrid IT and automatically protect it anywhere, whether at rest, in motion, or in use, using encryption tokenization and key management. Thales solutions also identify, evaluate, and prioritize potential risks for accurate risk assessment, as well as identify anomalous behavior and monitor activity to verify compliance, allowing organizations to prioritize where to spend their efforts.
- Identity & Access Management: Provide seamless, secure, and trusted access to applications and digital services for customers, employees, and partners. Our solutions limit the access of internal and external users based on their roles and context with granular access policies and Multi-Factor Authentication that help ensure that the right user is granted access to the right resource at the right time.
If you want a detailed explanation of how Thales can help you comply with the NIS2, read our white paper on the Network and Information Security Directive 2 (NIS2). To learn more, go to our dedicated NIS2 web page.

 Marcelo Delima | Senior Manager, Global Solutions Marketing
Marcelo Delima | Senior Manager, Global Solutions Marketing