5G is changing the security landscape. The need for security increases to effectively address a growing number of new use cases, new devices, going well beyond consumer mobile broadband to industries and enterprises. The Ericsson Authentication Security Module integrates the Thales 5G Luna Hardware Security Module to enable communication service providers (CSPs) to provide premium security for markets and use cases that have more strict security requirements.
The need for enhanced authentication in 5G ecosystems
Customer privacy and security are becoming an essential factor for CSPs in the 5G era. New use cases, diverse access types (i.e., 3GPP, non-3GPP, Wi-Fi, 3G, 4G and 5G), and the evolving infrastructure are increasing security demands across the network domain. Hence, protecting the authentication process of the millions of 5G users is important for securing innovation.
While security has always been a hot topic in mobile networks, the security focus is intensifying with 5G. This is because 5G will result in billions of new devices being connected to mobile networks. These devices will increase network exposure by having different characteristics, different types of access points and different security mechanisms.
Mobile network services are increasingly being delivered as virtual workloads running on cloud-based platforms, making network operations and valuable user data more exposed to attackers because same tools and tactics can be used towards telecom as for other industries. Attacks against mobile networks have increased in number and sophistication, which illustrates that the risk landscape is rapidly changing.”
A growing concern surrounding user authentication is the increasing number of privacy and security laws, regulations and standards that mandate strict requirements for data protection and network access controls. 5G networks are becoming a core part of many countries’ critical infrastructure and the adoption of new deployment scenarios like network slicing adds complexity to the authentication use cases that must be protected.
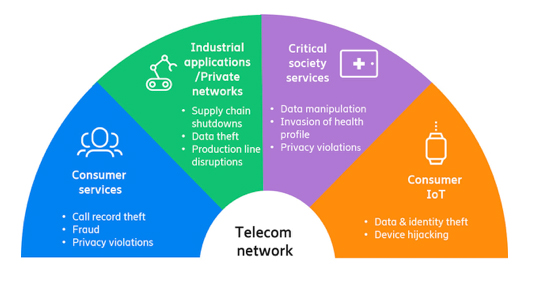
Figure 1: The need for enhanced authentication security
To mitigate the increased vulnerability risks in the wider 5G ecosystem, Ericsson is integrating the Thales 5G Luna Hardware Security Module to the 5G core. The Ericsson Authentication Security Module is providing CSPs with a stronger cryptographic key protection in a tamper-resistant hardware.
How the Ericsson – Thales integration addresses the new security challenges
The Ericsson Authentication Security Module is a premium security offering that includes a physical dedicated module for central management of authentication procedures in 5G Core networks. It offers:
- A single solution with multi-access support (3G/4G/5G)
- HSM for crypto operations and storage of sensitive encryption key material
- Compliance with standards and governmental regulations
- Pre-integrated to Ericsson’s dual-mode 5G Core for reliable deployment efficiency and flexibility
The Ericsson Authentication Security Module comprises the Authentication Credential Repository and Processing Function (ARPF), which centralizes all authentication procedures in the core network. It’s powered by the 5G Luna HSM component provided by Thales, the industry leader in the HSM market and a global presence in multiple sectors.
It provides the highest level of security through a tamper resistant hardware platform, certified FIPS 140-2 Level 3, that meets compliance requirements and a wide array of regulations.
With one combined solution, the Ericsson Cloud Core Subscription Manager provides highly secure authentication mechanisms to enable premium protection of the users’ privacy.
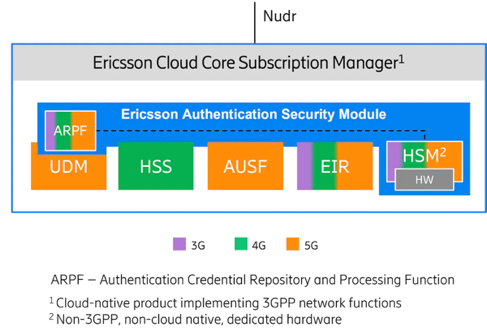
Figure 2: Ericsson Authentication Security Module overview
Benefits of the Ericsson Authentication Security Module
The Ericsson Authentication Security Module benefits CSPs in the following ways:
- Centralizes and consolidates authentication vector generation for 3G, 4G and 5G accesses in a seamless integrated solution into the Ericsson 5G Core offering.
- Provides a premium level of security in 5G networks, allowing the storage and management of all crypto keys and algorithms combining the strengths of Ericsson’s 5G Core Subscriber Data Management solution and Thales market leading HSM.
- Is compliant with major security standards in the industry and adds a compliance stamp to CSPs who are operating in markets with stricter regulatory requirements.
- Enables a safer industry ecosystem for use cases innovation in 5G by addressing the needs of verticals with very strict security requirements – from developers to consumers in the ecosystem chain.
- And finally, as part of Ericsson’s CCSM offering, it secures all required integration quality and support within one TCO.
You can find an in-depth analysis of how Ericsson provides HSM-based authentication in my article for the Ericsson blog.
At Mobile World Congress 2022, Thales, is showcasing its 5G security solutions that ensure the integrity of sensitive data across 5G network infrastructure. For more information or a demonstration For more information or a demonstration of the solution explained in this blog visit Chen Arbel, Associate VP, Business Development, 5G at Thales in Hall 2, Stand 2J30 or visit the 5G solutions page.
