To safeguard their users and infrastructure from sophisticated and ever-evolving cybersecurity threats, businesses of all sizes and across all sectors rely on robust encryption solutions that reduce these attack vectors. The advent of quantum computing will pave the way for many exciting new developments, but it also poses an unprecedented risk to data security and privacy and security teams must begin building appropriate resilience today to protect their business from a rapidly approaching threat.
Cybersecurity for a post-quantum era
The impact of a breach of sensitive health, financial and operational data will substantially increase due to the approaching quantum threat, whereby digital document integrity and security will be questioned. This risk is intensified by the fact that bad actors are acquiring and storing encrypted data today in anticipation of the day when quantum computing will render most current popular public key encryption schemes obsolete. Given the sensitive nature of the underlying data, this "harvest now, decrypt later" cyber-attack vector is a rapidly growing security concern for many firms. A recent Deloitte poll found that just over half of the security professionals surveyed believed that their organization was at risk of this type of attack, but only 27% of organizations had completed a relevant risk assessment.
In fact, governments and corporations have started making active plans to implement cybersecurity measures for a post-quantum world in reaction to this new and real danger. The US government’s announcement that all Federal agencies must have conducted and submitted an assessment of cryptographically vulnerable systems by 4th May 2023 is one of many examples where governments are pushing to build resilience. A quantum-secure security posture requires a holistic approach that encompasses the use of quantum-secure algorithms, cryptographic keys and key management systems. Migrating across to a quantum-secure posture is a long term project and will require organizations to operate a hybrid approach to their cryptographic measures so that they can maintain secure operations whilst testing and deploying new quantum-safe algorithms. Support for both pre- and/ post-quantum cryptography methods are a crucial part of current-day readiness initiatives.
The challenges of key strength and protection
Cryptographic keys are the backbone of standard encryption technology. To remain secure, they must be unpredictable and originate from a trustworthy source. Unpredictability is the foundation of a strong encryption key. A cyber system is vulnerable to attack if even a single bit of a key can be predicted in advance.
This unpredictability, especially in the face of cutting-edge technology like quantum computers, becomes increasingly important as attacks become more complex. Even state-of-the-art and highly standardized methods, such as NIST's Dual Elliptic Curve Deterministic Random Bit Generator, have been exposed as having flaws that can be exploited in cyberattacks by hackers or nation states.
Key generation is an essential part of the encryption layer in any cybersecurity implementation, but organizations must also consistently and reliably safeguard their cryptographic assets, including keys, certificates, and other cryptographic tokens. Hardware Security Modules (HSMs) such as the Thales Luna HSM offer an appealing solution in this case.
Vulnerabilities in cyber defense could result from neglecting either the generation, management, or protection of cryptographic keys. Even if a company puts significant thought into the security of its procedures and products, these vulnerabilities may still result in compromises and put the enterprise at risk.
How can Thales and Quantinuum build a quantum-computing resilience?
A plug-and-play integration between Quantinuum and Thales allows businesses to greatly enhance cryptographic key generation without requiring any modifications to existing infrastructure or applications from the end user. The collaboration combines the cutting-edge key generation technology of Quantum Origin with the peace of mind of Thales Luna HSMs.
Quantum Origin generates the strongest cryptographic keys through a fully verifiable process that uses Quantinuum’s own quantum computer. Not only does the platform generate provably unpredictable cryptographic keys, but it also ensures through a verifiable process the quality of the output, resulting in a security uplift when compared to keys issued with true random number generators (TRNGs) and first-generation quantum random number generators (QRNGs).
Using a Luna Functionality Module (FM,) Quantum Origin plugs seamlessly into the Thales Luna HSM. The FM extends the HSM’s native API, for Quantum Origin to seed into the Luna HSM’s existing deterministic random bit generator (DRBG). This integration of Quantum Origin enables the generation of quantum-computing hardened cryptographic keys directly from Thales Luna 7 HSM.
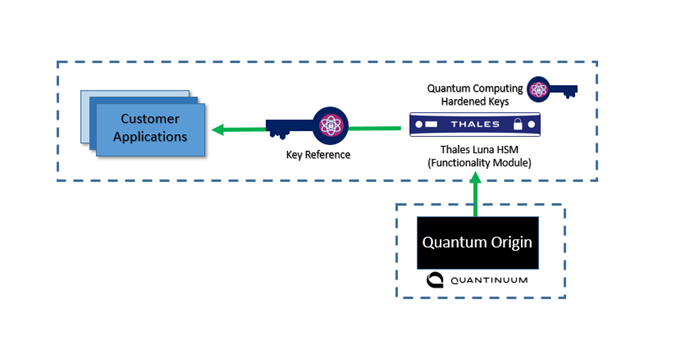
The combined innovation of Thales and Quantinuum creates a trusted solution that customers can rely on, as a crucial building block as they transition to quantum-secure measures. Integrating Quantum Origin into Thales’s Luna 7 HSM provides a solution that is easy to deploy and helps create a crypto-agile, or hybrid, foundation that allows organizations define a clear path towards building holistic quantum-resilience. Most importantly, it offers future-proof data protection today that helps protect data from advancing cyber threats, even as quantum computing power grows.

 Blair Canavan | Director, Alliances – PQC Portfolio, Thales
Blair Canavan | Director, Alliances – PQC Portfolio, Thales