Once upon a time no one had to worry about who had access to their organization’s data. There were few, if any, data dependent businesses, and for those that were data dependent, the world was a safe place of static systems that were disconnected from the world in which real people lived.

Over time that all changed.
Organizations moved from using accounting ledgers, address books and filing cabinets to store their data, to embracing digital systems to capture and analyze every bit of data they could collect.
Industry leaders started to rely on this data for business intelligence and competitive advantage. These systems, and the data they contained, became critical to business success. The information was made widely accessible, often available from almost any corner of the world, as companies’ embraced globalization.
Initially the new digital way of life was good.
Things got done fast!
Management had instant insight into how their organization was performing and could make quick and insightful decisions to make business course corrections; rather than waiting until the end of every financial quarter for the numbers to be rolled up into simple point-in-time financial reports.
People could work from anywhere and on any device. Organizations were able to access global talent pools.
Customers and clients were delivered better and faster services that were more attuned to their needs.
New disruptive services and products came to market that sometimes changed our way of life forever.
Yet lurking in the background were the seeds of future problems and chaos.
Bad people and governments wanted to get their hands on anyone and everyone’s data for their own nefarious purposes.
Government and industry regulators also started to be concerned that organizations were collecting or using data that needed to be more rigorously regulated and protected.
The days of the data wild west were drawing to a close.
Organizations were faced with a dilemma. How would they police their data systems to protect them from harm? How would they ensure they met the new regulatory and compliance landscape, which most of their critical systems had never been built to accommodate?
Luckily, there were people who saw this nightmarish situation coming well before anyone else. During the heady days of rapid digital transformation and exponential data growth, they developed technology and capabilities that allowed any data dependent organization to embed data security into the very fabric of their business systems.
Embedded data security delivered many advantages:
- It allowed organizations to protect their data crown jewels from harm regardless of where they were held: on premise, within virtual machines or in cloud platforms.
- It accommodated protecting data from the time it was captured or created, to whenever or wherever it was saved or stored.
- It automated the enforcement of attribute controls, allowing only authorized and trusted users or applications to write or read to data - while concurrently providing proactive alerts to when data was under threat from cyberattack or human error.
- It delivered the necessary reporting to demonstrate compliance and conformance to external regulatory authorities or to internal security control frameworks.
- It was off-the-shelf ready for use with hundreds of other digital and cybersecurity vendors, allowing affordable remediation of legacy digital systems and rapid deployment of new digital transformation systems.
So while some are still hiding their heads in their hands or averting their eyes from this nightmarish change of fortune for their data dependent businesses, others are embracing the opportunity to embrace and embed data security to achieve a happily ever after.
To view how this data story could end for your organization, take a stroll through Thales’ online storyboard today.
Data Sources:
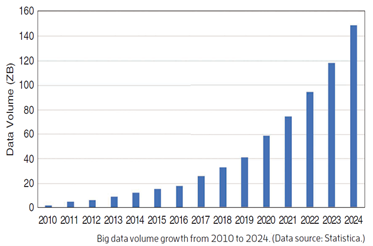
Volume of data/information created, captured, copied, and consumed worldwide from 2010 to 2025, Statistica.

 Brian Grant | CPL ANZ's Regional Director
Brian Grant | CPL ANZ's Regional Director