While the wide-ranging threats to users and devices remain one of the top cybersecurity concerns for business and cybersecurity leadership, just because a weakness exists doesn’t mean it can be effectively defended.

Today the log4j security exploit will be, and should be, the focus of almost everyone associated with cybersecurity. Once this critical flaw is resolved, as it inevitably will be through the extraordinary effort of people, we will need to get back to the day-to-day task of better protecting our critical digital assets - such as the data we collect and use to make decisions, deliver services or disrupt competitors.
You would think that given people and their personal devices and applications are the most common attack vector organizations face, we should invest all our time, effort and resources on defending them. There is one flaw in this strategy – it presumes people, and how they use devices and applications, are defendable...
Yes! It is important to develop and apply cyber-awareness training to your users.
Yes! It is important to deploy anti-virus and anti-malware software on those laptops and mobile phones.
Yes! It is important to secure network access and inspect network traffic, especially connections originating from the public internet.
Yet the very nature of the world in which we now operate, with everyone and everything interconnected, will compromise this strategy. It takes just one user error, overlooked device exploit or delayed security patch to allow a threat inside your organization.
Let’s pretend the extensive security programs you apply to your users and their devices and applications is compromised just once this coming year and the bad guys get inside your outer defenses. The target for many of these attacks is your valuable and essential business data. To either steal it, or disable it, in order to gain a financial reward.
So, what can you practically do to secure your critical data and remove the risk that human error could accidentally leave your data exposed?
Resolution #1 I will reduce the attack surface of data itself.
Many people reading this would have heard the phrase “need-to-know”. It is a foundational approach to information security before the time of computers and databases.
As opposed to the concept of Zero Trust whereby it is all about access, it applies a principal whereby even if you are trusted, be it a person, device or application, if there is no need-to-know (or change) something, your action is blocked and someone is notified in order to take corrective action.

Not many people realize that data platforms, from file servers to cloud storage, to databases in all their many forms, can be secured in a way that enforces need-to-know. The security tools to achieve this are off-the-shelf today and can easily enforce control over who or what can read or write, from or to data systems, at a very granular level…even down to a specific application instance or single user.
My first resolution recommendation is to take your most critical data and enforce need-to-know rules, for reading or writing, to not only mitigate the risk of human error but to also reduce the attack surface for other threats to your organization, such as ransomware.
Resolution #2 I will automate alerts and actively respond to threats to my data.
For anyone who has worked in a Security Operations Centre (SOC) or been responsible for analyzing the torrential downpour of log data that streams in from every device and system in an organization, identifying real threats within this cacophony is challenging at best and sometimes impossible.
While threat analysis tools that use machine learning and artificial intelligence can reduce stress and errors, analyzing logs associated with data systems is often not considered as critical as user and network analysis.
Yet, if you are trying to effectively defend critical data, any alert that is indicative of a deliberate or accidental threat to that data needs to be easily recognizable and immediately actioned.

The benefit of applying our first resolution of enforcing need-to-know, on who or what can read or write to critical data systems, is that alerting on unauthorized activity becomes very easy. Regardless of how trusted someone or something is, if their activity is unauthorized, a threat alarm should be generated to notify security teams that data is at risk – be it intentional or accidental.
Subsequently, my second resolution recommendation is to automate the generation of priority alerts when data is at risk and to have cybersecurity response teams take these alerts very seriously; they will be very limited in number and are indicative of a critical risk to data.
Resolution #3 I will embed security wherever critical data resides and is at risk.
In a perfect world, we would always secure data at point of capture, creation and or use. However, because many of our current systems were not built with data security in mind, this is not always possible. Subsequently we must be flexible in where, but not how, we apply data security.
Sadly, we cannot rely on other people or providers to secure our data for us. Even cloud or hyperscale computing providers deem that securing data is the responsibility of the customer.
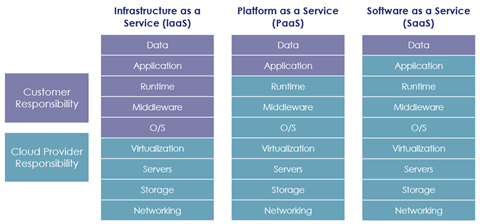
When applying data security, the general rule is to go as high up the stack as you can go for the best possible security outcomes. However, be careful, this should not be at the exclusion of securing raw data from privileged users or applications who traditionally have had extensive read and write access at the storage, folder or file level. Leaving this data exposed to privileged access abuse, while securing the data at the application layer, is like placing a high-quality deadbolt on your front door while leaving the back door wide open for anyone to walk in.
The good news is that it’s quite easy to enforce data security at multiple layers with the right Data Security Platform. In fact, Gartner have even taken the time to publish a strategic roadmap to help you understand the principals of what encompasses a Data Security Platform, which you can download from Thales’ website,
So, my third and final resolution recommendation is to embed your need-to-know data security at all applicable layers; so as to prevent compromise. Consider not only securing the confidentiality of the information to meet your privacy and compliance obligations, but also secure the integrity and protect the availability of the raw data from compromise by privileged (supposedly trusted) users, devices or code.
Implementing these resolutions will definitely help you mitigate the risk of human error when securing your data to prevent cyber-attacks or meet compliance. However, this is not a one-time task for the modern organization. In a world where data is continually being created and used; I like to say data security is a continuous journey rather than a single destination. Discover more about Thales’ data protection solutions.

 Brian Grant | CPL ANZ's Regional Director
Brian Grant | CPL ANZ's Regional Director