 Jose Caso | Product Marketing Manager, IAM
More About This Author >
Jose Caso | Product Marketing Manager, IAM
More About This Author >
 Jose Caso | Product Marketing Manager, IAM
More About This Author >
Jose Caso | Product Marketing Manager, IAM
More About This Author >
The digital shift in critical infrastructure is exposing a risk that many leaders haven’t fully accounted for: the rising influence - and volume - of external users.
Suppliers, contractors, research partners and distributors now play central roles in day-to-day operations. Yet in many organizations, they’re still treated as exceptions when it comes to identity and access. The systems managing them are often improvised, outdated, or too rigid to handle the complexity.
The result? Operational inefficiencies, security gaps and compliance exposure.
The new identity reality
Most IAM programs in critical infrastructure were designed around two user groups: employees and customers. But that model is breaking down.
Today:
- External users make up nearly half of those accessing enterprise systems
- Critical Infrastructure organizations rely on an average of 90 cloud applications
- Over 60% of data in those applications is considered sensitive
That’s not just a trend - it’s a fundamental shift in the identity perimeter.
What is B2B IAM?
Business-to-Business Identity and Access Management (B2B IAM) refers to the tools, processes and policies used to manage access for external entities like suppliers, contractors, vendors and partners. It addresses the unique needs of known third-party users who require ongoing, controlled access to internal systems. Unlike workforce IAM, which is built for employees, or customer IAM, which supports anonymous or high-scale consumer access, B2B IAM supports structured relationships, access governance and accountability. It sits at the intersection of operational efficiency, security and regulatory compliance.
These external users need access to the same core systems as employees: supplier portals, order management tools, ERP platforms, quality systems, collaboration spaces. But their access journeys are often slower, less secure and harder to manage.
Compliance is raising the stakes
Regulations are no longer vague about third-party risk, they’re increasingly explicit.
In Europe, the NIS2 Directive mandates that organizations in critical infrastructure sectors demonstrate control over third-party access to systems and data. The General Data Protection Regulation (GDPR) extends the definition of accountability to include data processors and external actors. Similar frameworks exist across Latin America, Asia-Pacific and the Middle East, with growing emphasis on shared liability.
In the U.S., existing state-level laws like CCPA and NYDFS already touch on external access, while federal proposals like the American Privacy Rights Act (APRA) are expected to raise the bar even further. Energy, defense and healthcare organizations are already seeing identity governance become a key audit point in federal inspections.
What this means in practice: businesses must be able to demonstrate who accessed what, when and why - even for users outside their organization.
One real example on what’s at stake: a user from a third-party organization still had access to internal systems six months after leaving their role. That’s not just poor hygiene, it’s a regulatory liability.
What internal IT teams are up against
Managing internal access is already hard enough. But managing hundreds of thousands of external users - with varying roles, timelines and requirements - creates an entirely new level of complexity.
One large aerospace manufacturer we work with is reported managing access for 250,000 external users, with plans to gradually expand that number to 700,000. Without delegation or automation, every access request or change flows through internal IT - creating bottlenecks, delays and overreliance on manual processes.
This slows down operations. A supplier who can’t access your order management system might delay shipments. A quality auditor stuck in provisioning limbo may push back critical certification. These are small delays that cascade into measurable business impacts.
Compounding the issue, many third-party users exist within hierarchies. A global vendor may have regional offices. A subcontractor may rotate staff frequently. Managing identity across these layers with manual tools is simply unsustainable.
A better path: Delegated User Management
Delegated User Management gives external organizations the ability to manage their own users - within limits defined by you.
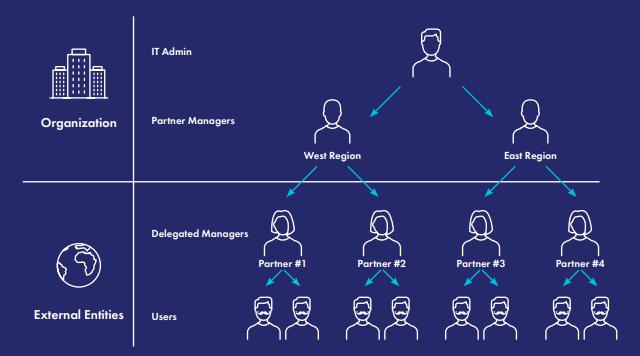
It reduces the workload on IT and gives partners more autonomy, while ensuring that access is granted according to policies, timelines and audit controls. This model works especially well when external users:
- Are time-bound or project-based
- Operate in distributed or regional hierarchies
- Require access to systems tied to regulatory or operational goals
Delegation doesn’t mean full control. It means assigning responsibility closer to the user source - while retaining policy, oversight and security at the platform level.
For example, a supplier admin might be allowed to add users to a procurement portal, but not assign access to finance systems or HR data.
Why current IAM tools fall short
Workforce IAM is typically tied to an internal HR system and built around full-time employees. Customer IAM, on the other hand, is optimized for high-scale, self-service use cases with minimal access governance.
Third-party identity doesn’t align with either model. These users:
- Aren’t in your Human Resources Information System (HRIS)
- Aren’t anonymous customers
- Do require consistent access and often handle sensitive data
To manage them effectively, organizations need platforms that support:
- Federated or native identities
- Delegated admin with role-based control
- Time-bound access and scheduled deprovisioning
- Consent management for regulatory alignment
- Full audit trails and reporting
This is exactly what B2B IAM is designed for.
What happens when this goes unsolved
Failing to address third-party identity has wide-reaching consequences:
- Procurement slowdowns when onboarding is delayed
- Security gaps when orphaned accounts go unnoticed
- Compliance violations when data access isn't traceable
- Partner frustration from clunky onboarding or rigid workflows
Perhaps most importantly, it becomes harder to scale your ecosystem. Growth often depends on external collaboration, but collaboration is slowed when every new partner or vendor requires days or weeks of manual IAM support.
What forward-thinking teams are doing
More organizations are recognizing that third-party identity is no longer an edge case - it’s a core design requirement.
They’re prioritizing IAM platforms that:
- Support external use cases out of the box
- Include delegation with organizational and hierarchy support
- Can be managed by business teams, not just IT
- Meet the audit and consent requirements of privacy laws worldwide
They’re also involving procurement, legal and compliance teams early - turning identity from a technical task into a cross-functional capability.
Final thought
Third-party access is no longer something that can be patched together with spreadsheets, emails, or legacy workarounds.
In critical infrastructure sectors - where compliance, continuity and control are paramount - managing external identity well is now a strategic capability.
Organizations that modernize how they handle third-party access will not only reduce risk, but also gain the agility to move faster, collaborate better and grow with confidence.
Want to go deeper? Watch the full webinar: Addressing 3rd-Party & Supply Chain Risks in Critical Infrastructure with B2B IAM. In this session, we explore real-world risks, industry data and how B2B IAM helps critical infrastructure organizations take back control.
It’s time to make B2B IAM a first-class citizen in your identity strategy.